Insights
History of DNS Abuse Attack Vector & Countermeasure

The Domain Name System (DNS) is the backbone of the internet, translating human-readable domain names into IP addresses. However, this critical infrastructure has often been a target of various cyber-attacks and abuses.
This blog is about my book, which concisely overviews my extensive research on DNS threats. It highlights the historical context of DNS abuse, various attack vectors, and the countermeasures developed to combat these threats. Dive in to discover the critical importance of DNS security in today’s digital landscape.
The Importance and Vulnerability of DNS
DNS is essential for the smooth operation of the internet, acting as a phonebook that links domain names with IP addresses. Despite its importance, DNS has been frequently exploited for malicious purposes by both cybercriminals and nation-states. According to the 2021 DNS Security Survey, 87% of companies experienced one or more attacks.
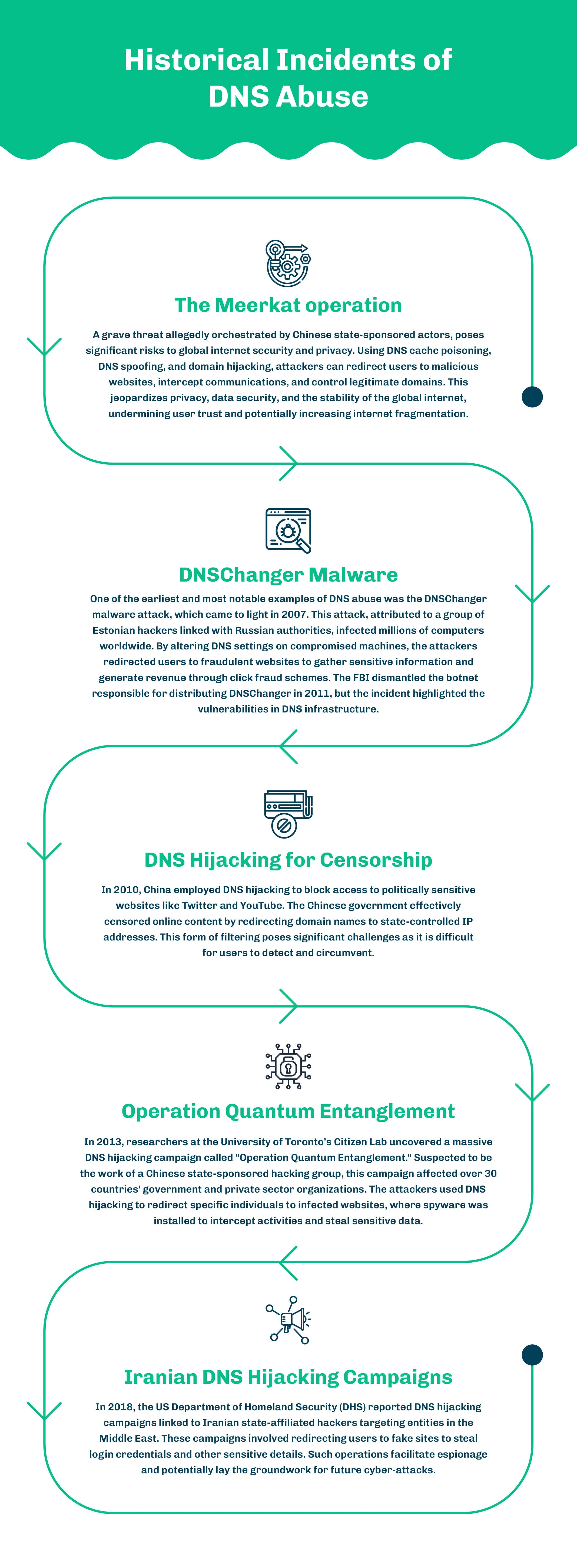
Techniques and Tools for DNS Abuse
1. Fast Flux DNS
Fast flux is a technique cybercriminals use to evade detection by rapidly changing the IP addresses associated with a domain. This method is often employed in social engineering campaigns, command-and-control (C2) infrastructures, and even illicit gambling and adult sites.
2. Smoke Loader C2 Campaign
In a smoke loader C2 campaign, fast flux DNS enables cybercriminals to maintain control over compromised systems by constantly rotating IP addresses. This agility makes it difficult for security researchers and law enforcement to pinpoint and disrupt the malicious infrastructure.
3. DNS Cache Poisoning
DNS cache poisoning involves inserting false information into a DNS cache, causing it to return an incorrect IP address and redirect traffic to malicious sites. This technique can lead to significant security breaches by misdirecting users to fraudulent websites where their personal information can be stolen.
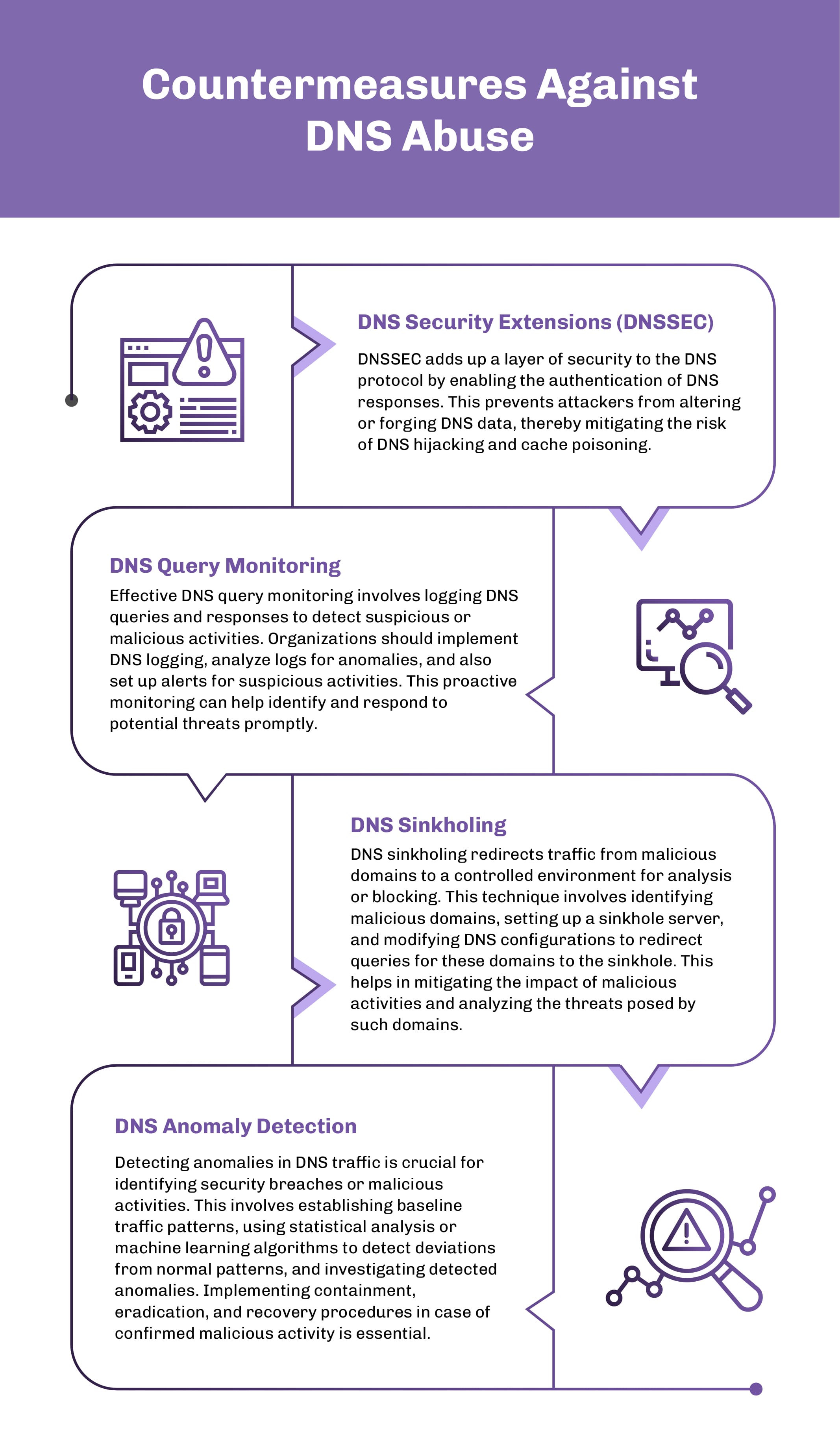
Advanced Threat Detection Using MITRE D3FEND Framework
The MITRE D3FEND framework provides a comprehensive set of countermeasures for DNS-based cyber-attack techniques:
- DNS Denylisting (D3-DNS-DNYL): Proactively blocking malicious domains by maintaining and regularly updating a centralized Denylist.
- DNS Allowlisting (D3-DNS-ALWL): Permitting access only to approved domains by maintaining and updating a centralized allowlist.
- DNS Query Monitoring (D3-DNS-QMON): Implementing DNS logging and analyzing DNS traffic to detect suspicious activities.
- DNS Traffic Anomaly Detection (D3-DNS-ANOM): Using statistical and machine learning strategies to identify deviations from normal DNS traffic patterns and investigate anomalies.
The Role of International Cooperation
While technical measures are crucial, addressing DNS abuse requires greater international cooperation and accountability. Developing norms governing responsible state behavior in cyberspace and mechanisms to hold violators accountable is essential. Collaborative efforts can help create a safer online environment by preventing state-sponsored cyber-attacks and ensuring global internet security. In the first quarter of 2024, Cloudflare’s defence systems automatically mitigated 4.5 million DDoS attacks, representing a 50% year-over-year (YoY) increase.
Conclusion
I hope you have enjoyed reading this blog as much as I enjoyed writing it. The history of DNS abuse demonstrates the evolving tactics employed by cybercriminals and state actors to exploit DNS vulnerabilities. Organizations must prioritize DNS security as the threat grows by implementing robust countermeasures and fostering international cooperation. By staying vigilant and proactive, we can mitigate the risks posed by DNS abuse and ensure the integrity and security of the Internet.
Why Paramount?
Paramount helps protect your organization’s DNS security by using technologies like DNS Security Extensions (DNSSEC) and DNS over HTTPS (DoH) to secure your DNS traffic. Their monitoring tools detect anomalies in real time, providing early warnings of potential abuses. Paramount offers solutions such as DNS sinkholing and secure DNS configuration to guard against hijacking and cache poisoning. They also provide education and awareness programs to help your team implement best practices and enhance overall security.
Recent Posts
- 10 Tips to examine while implementing zero trust model
- 10 Tips to examine while developing Cybersecurity Awareness Program
- Cybersecurity Lessons from the Cyberattack on MGM Resorts
- Why is choosing the Right Security Operations Center Necessary?
- Generative AI adoption risks you should address to safeguard your enterprise
- IT/OT convergence a way forward towards robust OT security system
- Ransomware attack on Chinese bank’s US subsidiary another warning signal

