Insights
Cybersecurity Lessons from the Cyberattack on MGM Resorts

As the world becomes more digital, cybersecurity threats are on the rise. More cyberattacks are occurring, and perpetrators are unleashing new types of cyberthreats on enterprises and individuals. Between January and October 2023 alone, 5+ billion records have reportedly been breached*. The ransomware attack on MGM Resorts International (MGM), the global hospitality and entertainment enterprise whose properties include MGM Grand, Mandalay Bay and Bellagio, provides important security lessons to CISOs, CSOs and other business leaders. It reinforces the need to view cybersecurity as more than a ‘tech’ domain because actors are increasingly exploiting human psychology.
*(source: https://www.itgovernance.co.uk/blog/list-of-data-breaches-and-cyber-attacks-in-2023)

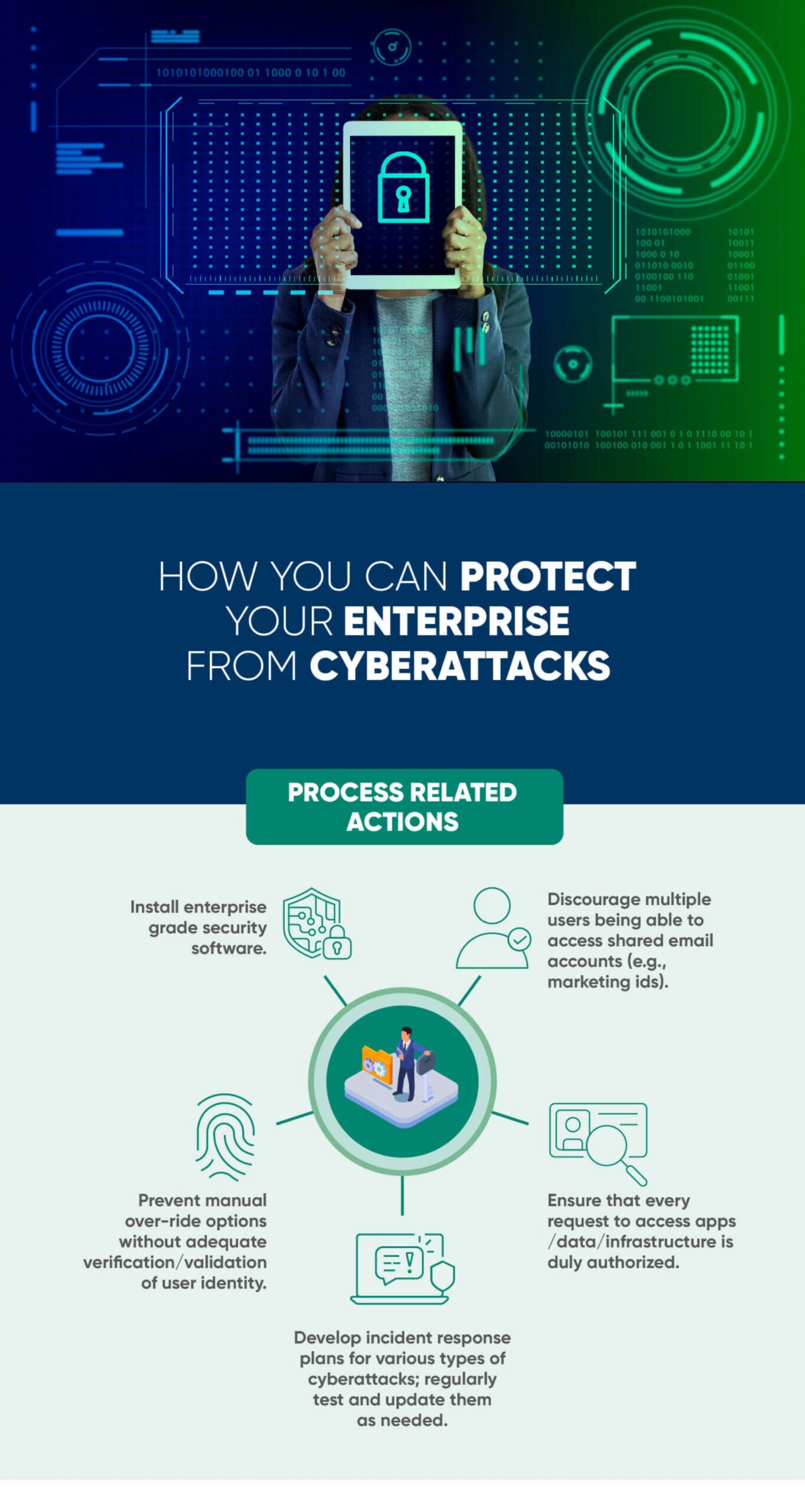
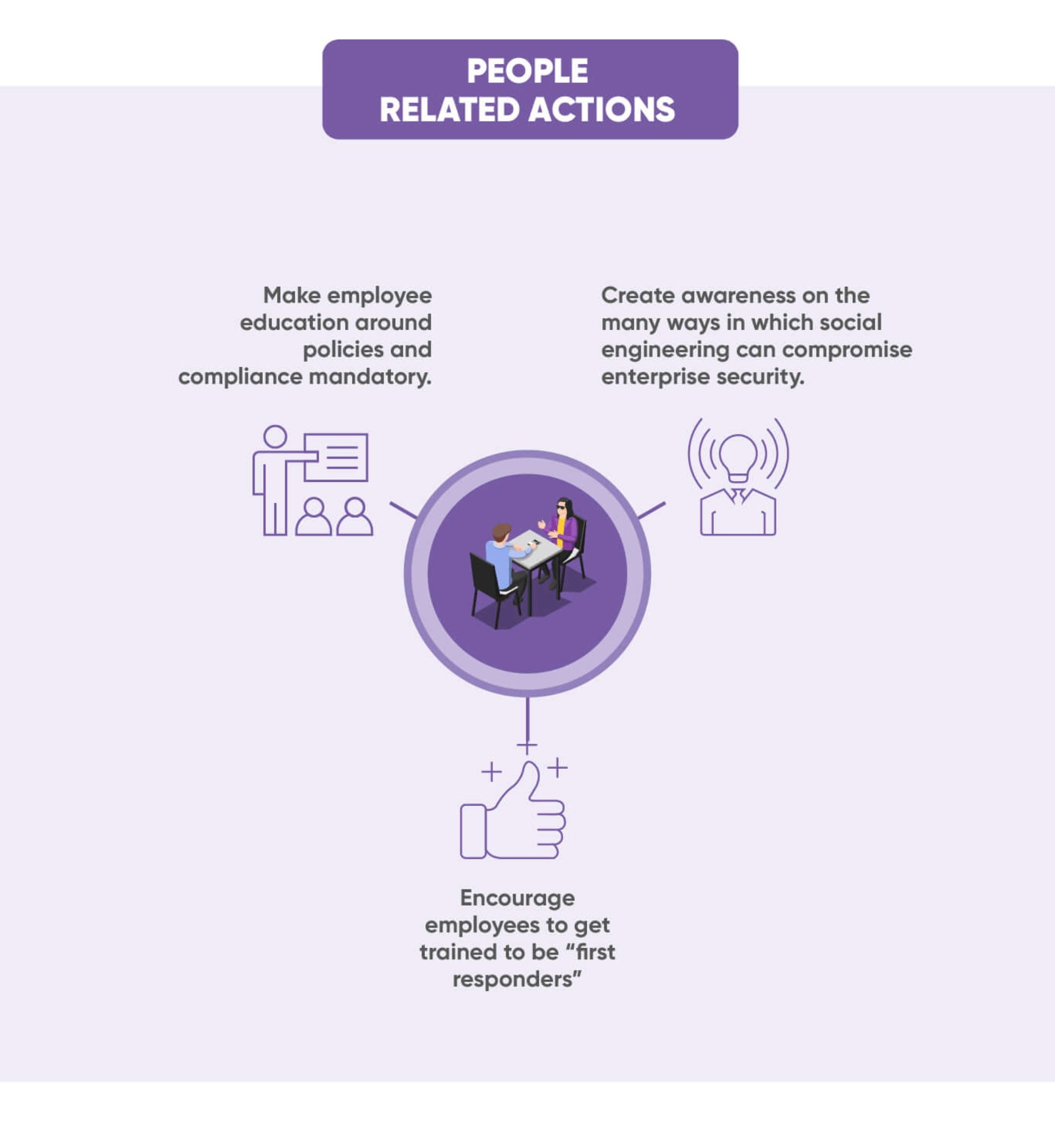
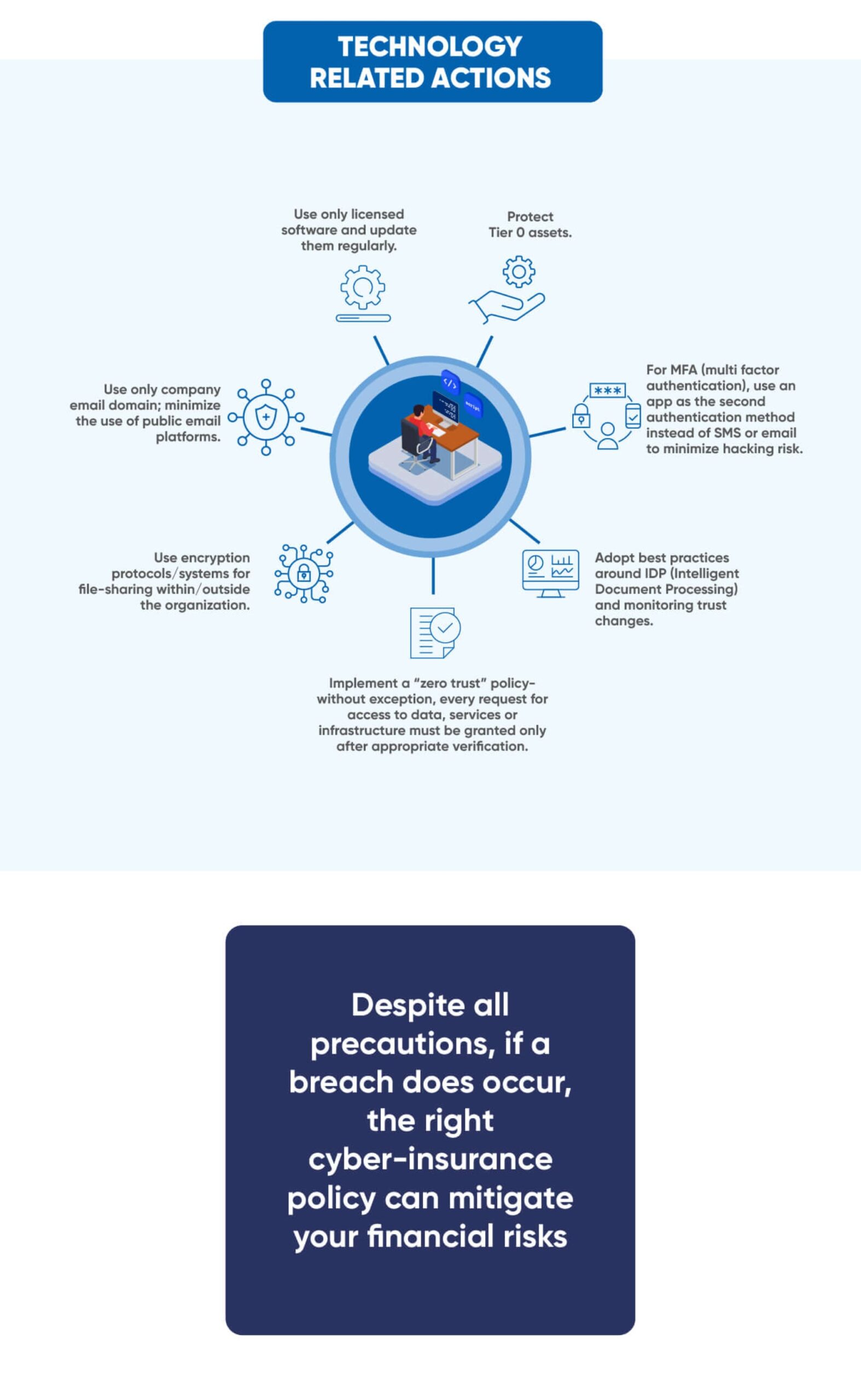
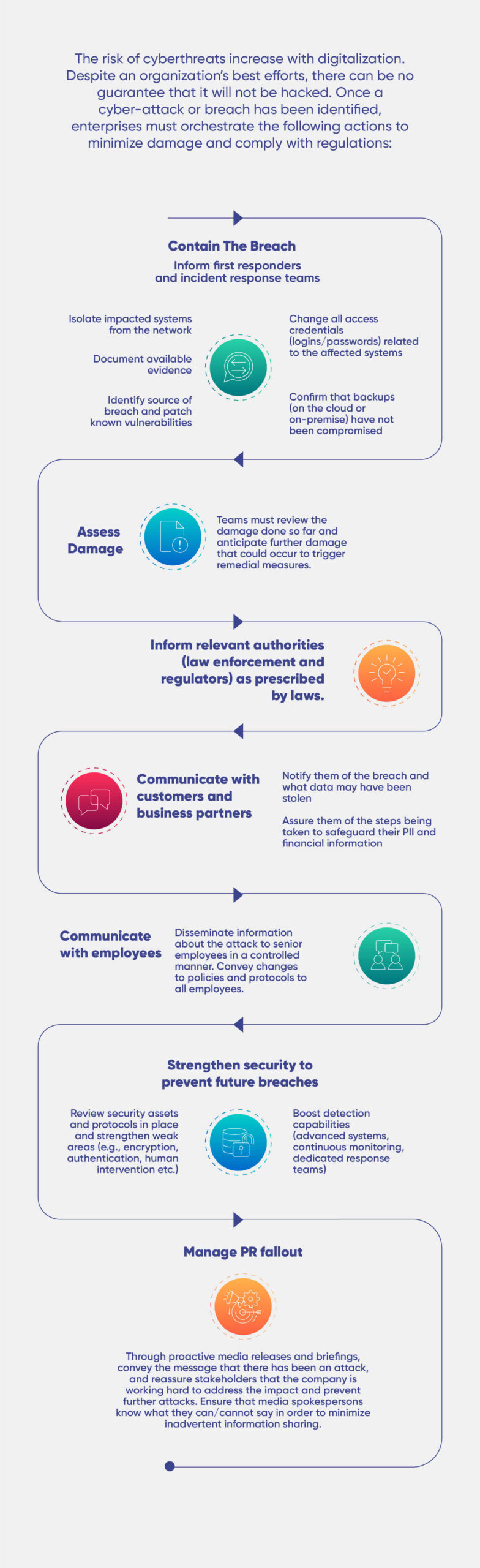
We at Paramount Assure https://paramountassure.com/ can help you review your existing cybersecurity measures and advise you on what more you can do to strengthen them. We can also help implement various cybersecurity defences in your enterprise. To schedule a discussion with our experts, write to us on [email protected].
Recent Posts
- Why is choosing the Right Security Operations Center Necessary?
- Ransomware attack on Chinese bank’s US subsidiary another warning signal
- 10 Tips to examine while implementing zero trust model
- 10 Tips to examine while developing Cybersecurity Awareness Program
- Generative AI adoption risks you should address to safeguard your enterprise
- History of DNS Abuse Attack Vector & Countermeasure
- IT/OT convergence a way forward towards robust OT security system


