Blog
Data Privacy in the GCC

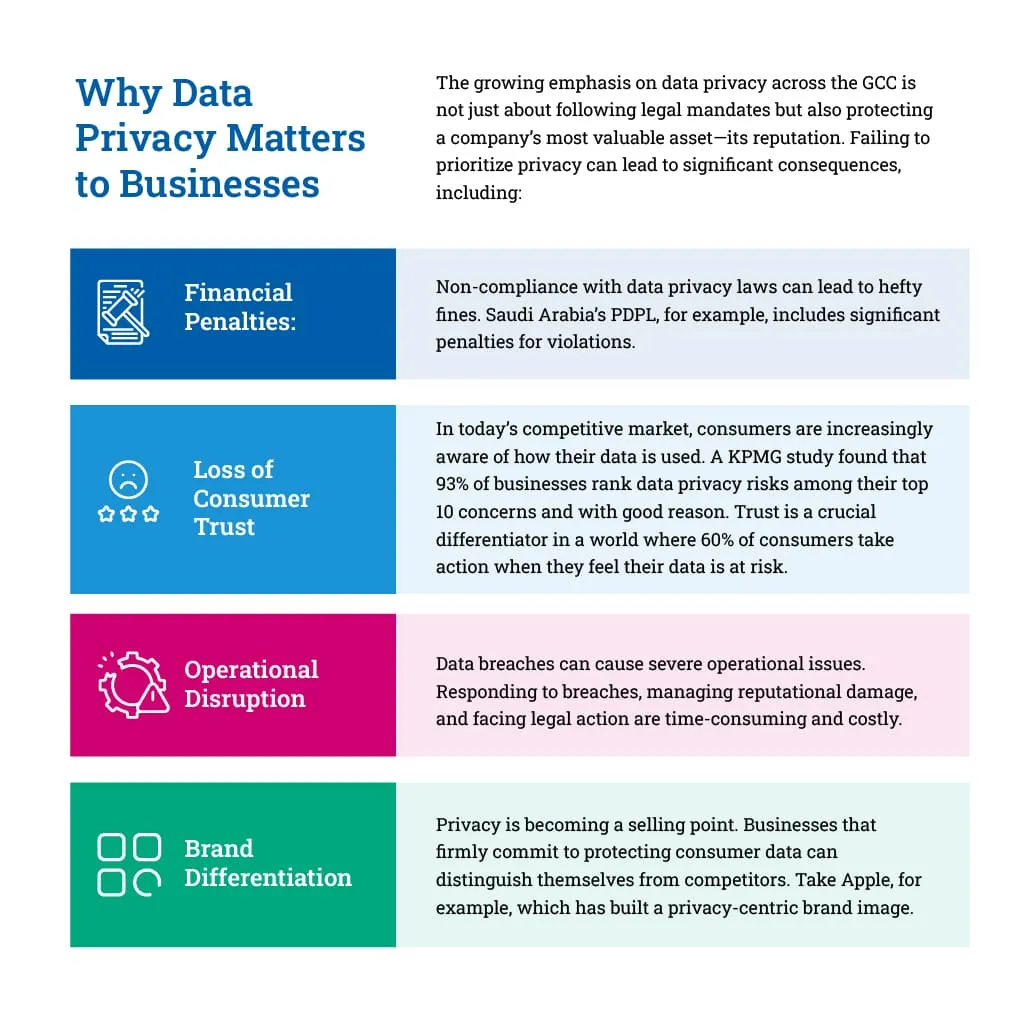
Nowadays, data is the lifeblood of organizations, whether it’s customer information, employee records, or sensitive business data. Companies across sectors rely heavily on data to drive decision-making, improve customer service, and gain a competitive edge. However, with data’s increasing volume and complexity comes the responsibility to protect it. Privacy laws around the globe are evolving rapidly to safeguard personal information, placing organizations under greater scrutiny. This is particularly true in the GCC (Gulf Cooperation Council), where governments are ramping up efforts to enforce stringent data privacy regulations.
This blog explores the trends, challenges, and practical strategies organizations operating in the GCC can implement to ensure data privacy compliance.
The Gulf region is not exempt from the global movement towards data privacy protection. The GCC has witnessed a surge in implementing robust privacy laws across its member states. The region is committed to aligning with global privacy standards from Saudi Arabia’s Personal Data Protection Law (PDPL) to Oman and Kuwait’s data privacy frameworks.
-
Saudi Arabia’s Personal Data Protection Law (PDPL)
Saudi Arabia’s PDPL is a significant milestone for the Kingdom. It regulates personal data collection, processing, and sharing. Private and public organizations must comply with the PDPL’s stringent requirements or face penalties. The law was introduced in 2022 with a one-year grace period for organizations to ensure compliance. As the deadline approaches, businesses must demonstrate their readiness, including implementing policies and practices that protect personal data per the law.
-
Qatar’s Pioneering Privacy Law
Qatar was one of the first GCC countries to introduce a data privacy law back in 2016. Over the past few years, the country’s Data Protection Authority (NDPO) has become more proactive in enforcing the law. Companies are now regularly audited to ensure they comply with privacy requirements. This development serves as a wake-up call for other GCC countries, emphasizing that privacy laws are no longer theoretical but actively enforced.
-
Other GCC Countries
The UAE, Oman, and Kuwait have also implemented their privacy laws, with varying degrees of enforcement. Oman and Kuwait’s laws were introduced recently, and compliance is already required. The UAE, which implemented its privacy regulations in 2021, is awaiting the release of executive regulations to begin full enforcement.
Key Trends Shaping Data Privacy in the GCC
As privacy regulations in the GCC continue to evolve, several key trends are emerging that businesses must be aware of.
-
The Role of AI and Automation in Privacy Management
The rise of AI and automation has transformed how companies manage privacy. AI-driven tools are increasingly being used to handle complex privacy tasks such as data discovery, data mapping, breach detection, and compliance reporting. These tools allow businesses to automate repetitive and time-consuming processes, enabling more efficient data privacy operations.
-
Fluidity in Regulatory Environments
The global regulatory landscape is dynamic, with new privacy laws, guidelines, and enforcement practices regularly introduced. For example, in July 2023, the European Union adopted the AI Act, a law aimed at regulating the use of artificial intelligence. In the GCC, similar regulatory developments are expected, such as ongoing updates from Saudi Arabia’s SDAIA (Saudi Data and Artificial Intelligence Authority).
-
Consumer Expectations Are Changing
Consumers in the GCC are becoming more privacy-conscious. Research suggests that 74% of consumers are more likely to trust brands that prioritize the safe use of personal information. This growing demand for privacy is pushing companies to comply with regulations and adopt a privacy-first mindset. The idea that privacy is merely a compliance issue is giving way to the notion that privacy can be a strategic advantage.
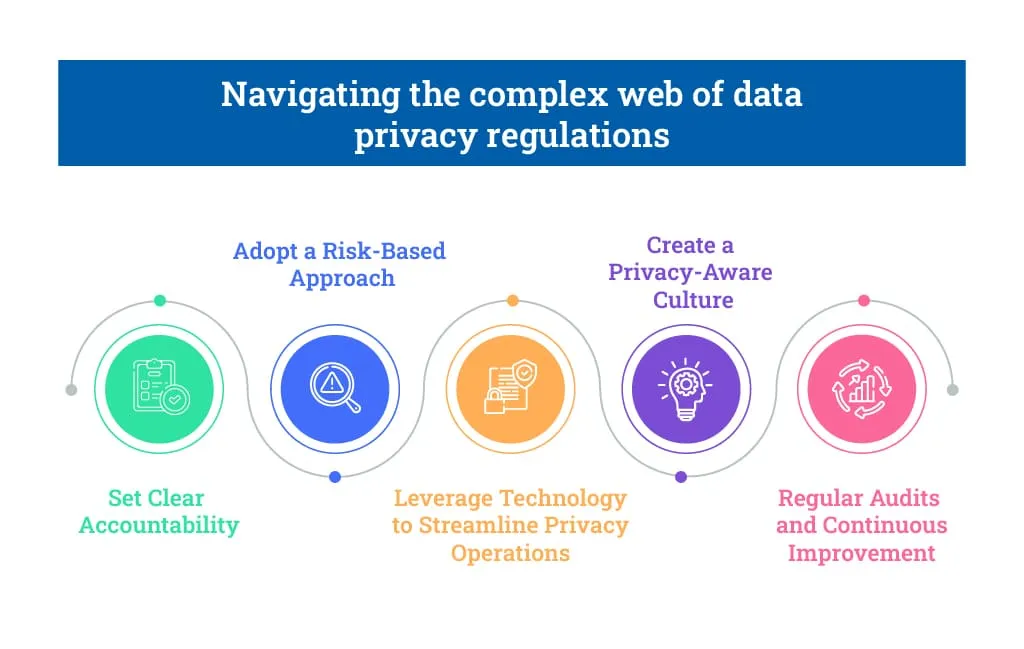
Navigating the complex web of data privacy regulations can be daunting, especially for organizations operating in multiple jurisdictions. Here are practical steps businesses can take to ensure compliance and mitigate the risk of data privacy violations.
-
Set Clear Accountability
One of the most critical aspects of data privacy compliance is assigning clear roles and responsibilities within the organization. Data privacy should not be a siloed function handled solely by IT or legal departments. Instead, accountability should be shared across all relevant departments, with senior management playing a key role in shaping the organization’s privacy strategy.
To this end, appointing a Data Protection Officer (DPO) or creating a Data Privacy Office that reports to senior leadership can ensure privacy remains a top priority. -
Adopt a Risk-Based Approach
Given the complexities of managing vast amounts of data, businesses should adopt a risk-based approach to privacy management. Companies should focus on high-risk areas rather than attempting to tackle every possible data privacy concern. Identifying which data processing activities pose the greatest risk to personal data and consumer trust allows organizations to allocate resources more efficiently and address critical privacy gaps.
-
Leverage Technology to Streamline Privacy Operations
As mentioned earlier, technology plays a pivotal role in optimizing data privacy management. Investing in privacy management software can help businesses automate essential tasks, such as:
Consent Management: Tracking and managing consumer consents across multiple channels.
Data mapping: Identifying where personal data resides within the organization.
Responding to data subject requests: Automating the process of responding to requests like data access or deletion.
Breach notification: Automatically detect and notify authorities and data subjects of breaches within legally mandated timeframes. -
Create a Privacy-Aware Culture
While technology and processes are important, the human element is one of the most significant factors in data privacy compliance. Employees across departments must be trained to understand their role in protecting personal data. Regular training programs and privacy awareness campaigns can ensure that staff are aware of the company’s privacy policies and best practices.
-
Regular Audits and Continuous Improvement
Once a privacy program is implemented, regular audits are essential to assess its effectiveness. Organizations should monitor key performance indicators (KPIs) related to privacy and make adjustments as necessary. Continuous improvement is crucial, especially in a constantly changing regulatory environment.
Conclusion: Privacy as a Strategic Asset
For organizations operating in the GCC, data privacy compliance is not just a legal obligation; it’s an opportunity to build trust, differentiate from competitors, and enhance business operations. As privacy regulations evolve, businesses must adopt a holistic and forward-thinking approach to privacy management. By embedding privacy into their organizational DNA, companies can meet compliance requirements and position themselves as responsible, customer-focused brands in the digital age.
Recent Posts

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
