Insights
IT/OT convergence a way forward towards robust OT security system
In this digitalized world, cyber security as a threat, is not a problem of a single entity in a company, but rather a threat faced by the entire system that is connected with the internet.
With the digitalization and automation of the Operational Technology (OT), which forms the backbone of a company, is not safe from the disruptive threats faced by internet-connected devices, like data theft, ransomware attacks, etc. With the increased number of cyber-attacks on OT installations, the topic of OT cyber security has taken prominence.
Traditionally, OT systems were isolated from external networks to ensure security. However, with advancements like IoT and the convergence of IT and OT, these systems are becoming more connected, posing new security challenges.
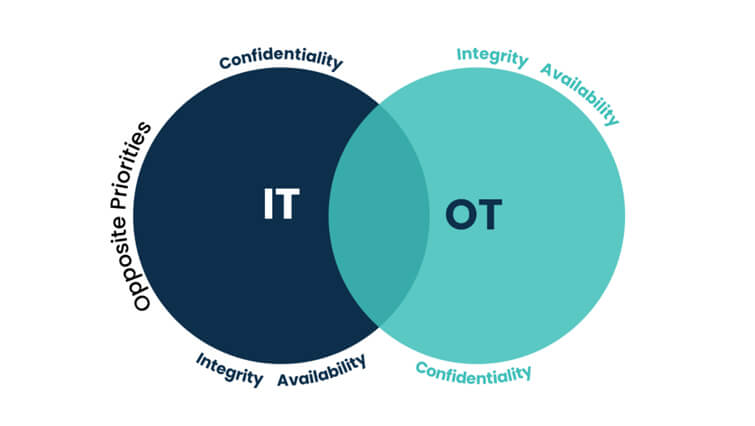
In OT and IT, systems are different, the environment they work in is different, and the language they speak is different, but both have a few things in common – network security, privileged access management, data security, and application security. In this connected world, be it OT or IT, both have a common goal – to counter “cyber-attacks”.
However, to combat the common threat, working in silos is definitely not the answer. According to the Gartner report, OT security is a growing priority and collaboration between IT and OT is important to counter cyber-attacks.
Hence, the company has to leverage the existing IT team’s cybersecurity expertise and collaborate with the OT team to better understand the OT environment, assets, and priorities, so that together they can create a robust OT security system.
Before understanding how a company can leverage the IT team’s strength to develop robust OT security, identifying the critical differences between OT and IT will be helpful.
Differences between OT and IT Security
Focus: OT security focuses on safeguarding industrial control systems and other operational technology used in critical infrastructure sectors like manufacturing, energy, utilities, transportation, and healthcare, while IT security focuses on protecting networks, data, information systems, digital assets, etc.
Assets: In OT environments, the assets being protected include physical machinery, industrial equipment, sensors, and devices that control critical processes. The infrastructure often includes specialized hardware and legacy systems, which may have limited security features. Whereas in IT, security protects digital assets, including servers, databases, workstations, networks, software applications, and sensitive data. The infrastructure is primarily based on computers, servers, cloud services, and networking equipment.
Risk: OT security breaches will have immediate and tangible physical consequences disrupting the business operations. OT breaches could have severe consequences like power outages or production shutdowns and at worse, loss of life!. While IT security breaches lead to data theft, financial losses, etc.
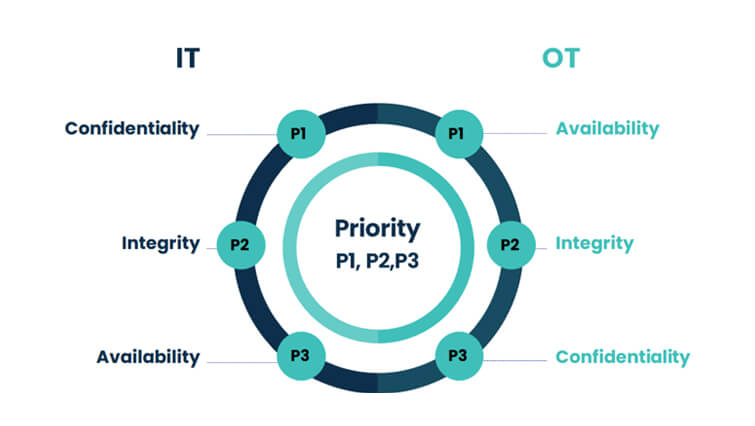
In IT, security priority is CIA – Confidentiality, Integrity, and Availability. In OT, Safety supersedes everything. While, availability is most sought after, may not necessarily be the same across various sectors, because the mission objective varies. For instance, if availability is important in the automobile industry, confidentiality is most sought after in pharmaceutical companies.
To identify a company’s OT security priority, given that Safety is non-negotiable, understanding mission objectives/ organizations/industry becomes important to address OT security.
In IT, security priority is CIA – Confidentiality, Integrity, and Availability. In OT although the availability is most sought after, may not necessarily be the same across various sectors, because the mission objective varies. For instance, if availability is important in the automobile industry, confidentiality is most sought after in pharmaceutical companies.
To identify a company’s OT security priority, understanding mission objectives/ organizations/industry becomes important to address OT security.
Although IT and OT work in different environments, the common goal being the same, that is, to counter cyber-attacks, there is a need to integrate both OT and IT security practices to ensure comprehensive protection against modern cyber threats.
While understanding the mission objectives of an organization, here are steps on how to leverage the IT security professional expertise and collaborate with the OT team to build a robust OT security system.
Steps to leverage IT expertise to secure OT infrastructure:
Build Defensible Architecture: Use and leverage existing IT tools and concepts like firewalls, and network segmentation, to ensure that you secure your OT and IT data flows and, in the process, build a robust architecture that protects your OT systems.
Introduce IT security tools and standards suitable for OT environments, such as firewalls, intrusion detection/prevention systems, and antivirus solutions tailored for industrial control systems. Adapt IT-centric methodologies to suit the dynamic nature of OT environments.
Implement Network Monitoring: Monitoring your industrial assets enables visibility of all the assets that are connected to your network. Visibility of connected assets allows you to manage your assets better as it gives control over the configuration and control over change. Set up continuous monitoring using IT-centric tools to detect anomalies, unusual activities, and potential threats within the OT network. Continuous monitoring enables you to draft incident response plans better. Overall, it allows you to manage your risks better.
OT-Specific Incident Response Plan: Communication protocols, devices, and threat groups, all are different in the OT environment. Understanding the distinct OT environment, an OT incident response plan needs to be drafted. Further, just having a draft plan in place will not suffice, practicing it through simulation is important, so one is ready to respond and not react when the actual incident happens.
Vulnerability Management: Conduct comprehensive risk assessments and vulnerability scans across OT networks. Apply IT-centric tools and methodologies to identify weaknesses, outdated systems, and potential entry points for cyber threats.
Secure Your Remote Access: Implement a strong encryption protocol and multi-factor authentication, or have tools or technologies in place that ensure zero trust secure remote access to your OT systems.
Education and training: Provide comprehensive training to OT staff on IT-centric cybersecurity best practices. Educate them about common threats, social engineering tactics, and the importance of following security protocols.
Fostering collaboration between IT and OT teams helps to create a unified cybersecurity approach. Encourage knowledge sharing and establish cross-functional teams to address security challenges holistically. As it is a continuous process, regularly reviewing and refining OT security strategies based on evolving threats, technological advancements, and lessons learned from incidents helps in securing OT systems.
By leveraging IT expertise, organizations can bring a systematic and structured approach to OT security, combining the strengths of both domains to create robust defenses against cyber threats while ensuring the reliability and safety of critical industrial processes.
Recent Posts
- 10 Tips to examine while developing Cybersecurity Awareness Program
- Ransomware attack on Chinese bank’s US subsidiary another warning signal
- 10 Tips to examine while implementing zero trust model
- Why is choosing the Right Security Operations Center Necessary?
- History of DNS Abuse Attack Vector & Countermeasure
- Cybersecurity Lessons from the Cyberattack on MGM Resorts
- Generative AI adoption risks you should address to safeguard your enterprise

