Blog
Never Trust, Always Verify: Why Zero Trust is the Key to Modern Cyber Defense

In an increasingly connected world, the need for robust cybersecurity frameworks has never been more critical. Traditional security models have long assumed that anything within the network’s perimeter could be trusted. However, this approach needs to be updated, given the sophisticated nature of modern cyber threats.
This shift has led to the rise of the Zero Trust security model, a framework designed to address the evolving landscape of cybersecurity by eliminating the concept of trust. According to a survey, 76% of organizations reported they were in the process of adopting Zero Trust, up from 58% in 2021
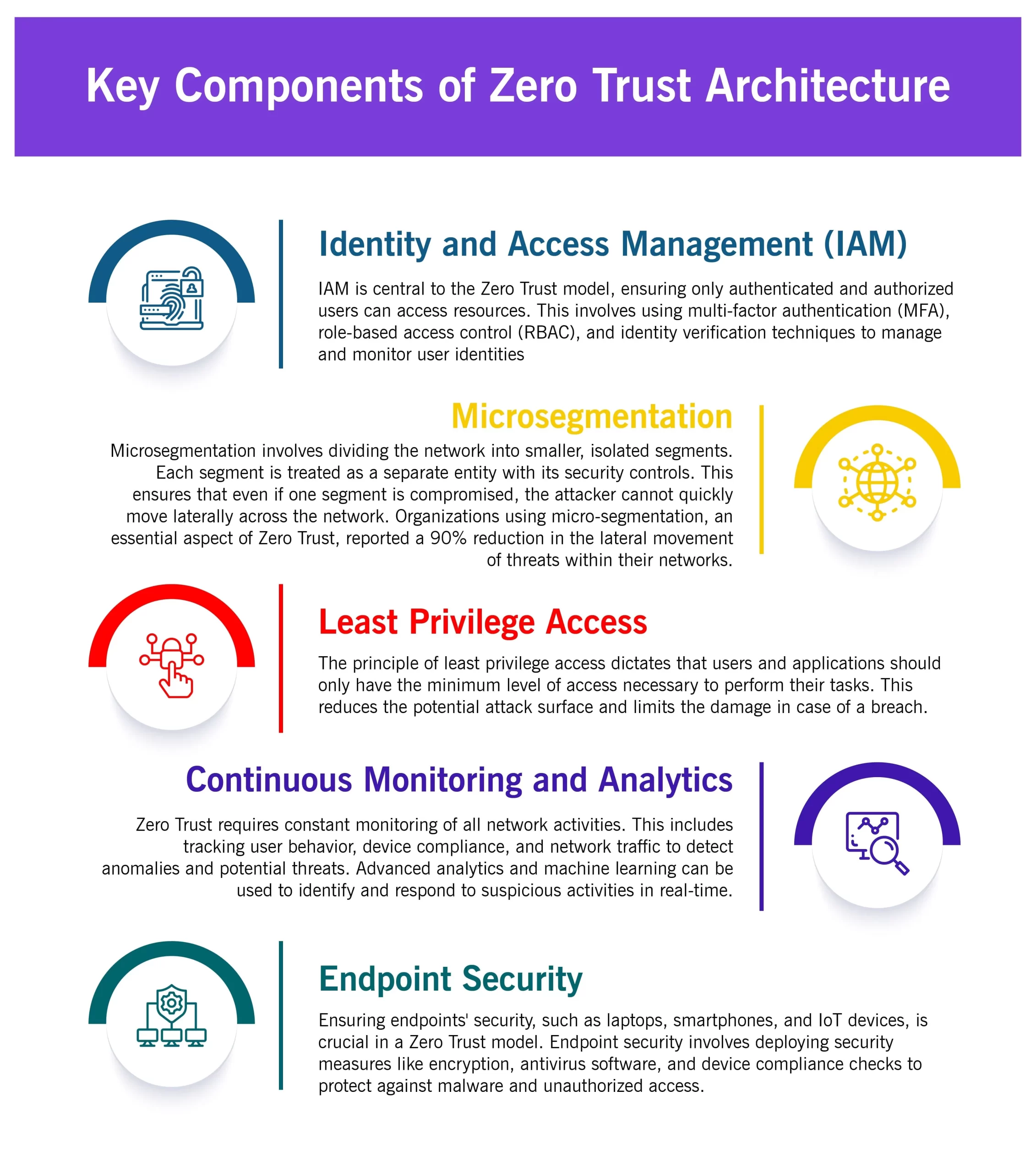
Implementing Zero Trust
While the Zero Trust model offers significant security benefits, implementing it can be challenging. Organizations must consider several factors to ensure a successful deployment:
- Understanding the Organization’s Architecture: Before implementing Zero Trust, organizations must clearly understand their network architecture, including all users, devices, applications, and data flows. This knowledge is essential for identifying potential vulnerabilities and designing an effective Zero Trust strategy.
- Building a Strong Identity Foundation: Identity management is at the heart of Zero Trust. Organizations must invest in robust identity and access management solutions that support Access Management, Identity Governance, multi-factor authentication, single sign-on (SSO), and identity federation. Additionally, ensuring the integrity of user identities is crucial to preventing unauthorized access.
- Adopting a Phased Approach: Implementing Zero Trust should not be an all-or-nothing process. Organizations can start by adopting Zero Trust principles in high-risk areas or for critical assets and gradually expand to cover the entire network. This phased approach allows for easier management and minimizes disruption to business operations.
- Integrating Security Tools: To maximize the effectiveness of Zero Trust, organizations should integrate their security tools and technologies. This includes combining IAM, endpoint security, network monitoring, and threat detection solutions into a cohesive security ecosystem. Integration ensures seamless communication between tools, enabling faster threat detection and response.
- Employee Education and Awareness: A successful Zero Trust implementation requires buy-in from all employees. Organizations must invest in cybersecurity training and awareness programs to educate employees about the importance of Zero Trust and their role in maintaining security. This includes understanding the risks of phishing attacks, practicing good password hygiene, and reporting suspicious activities.
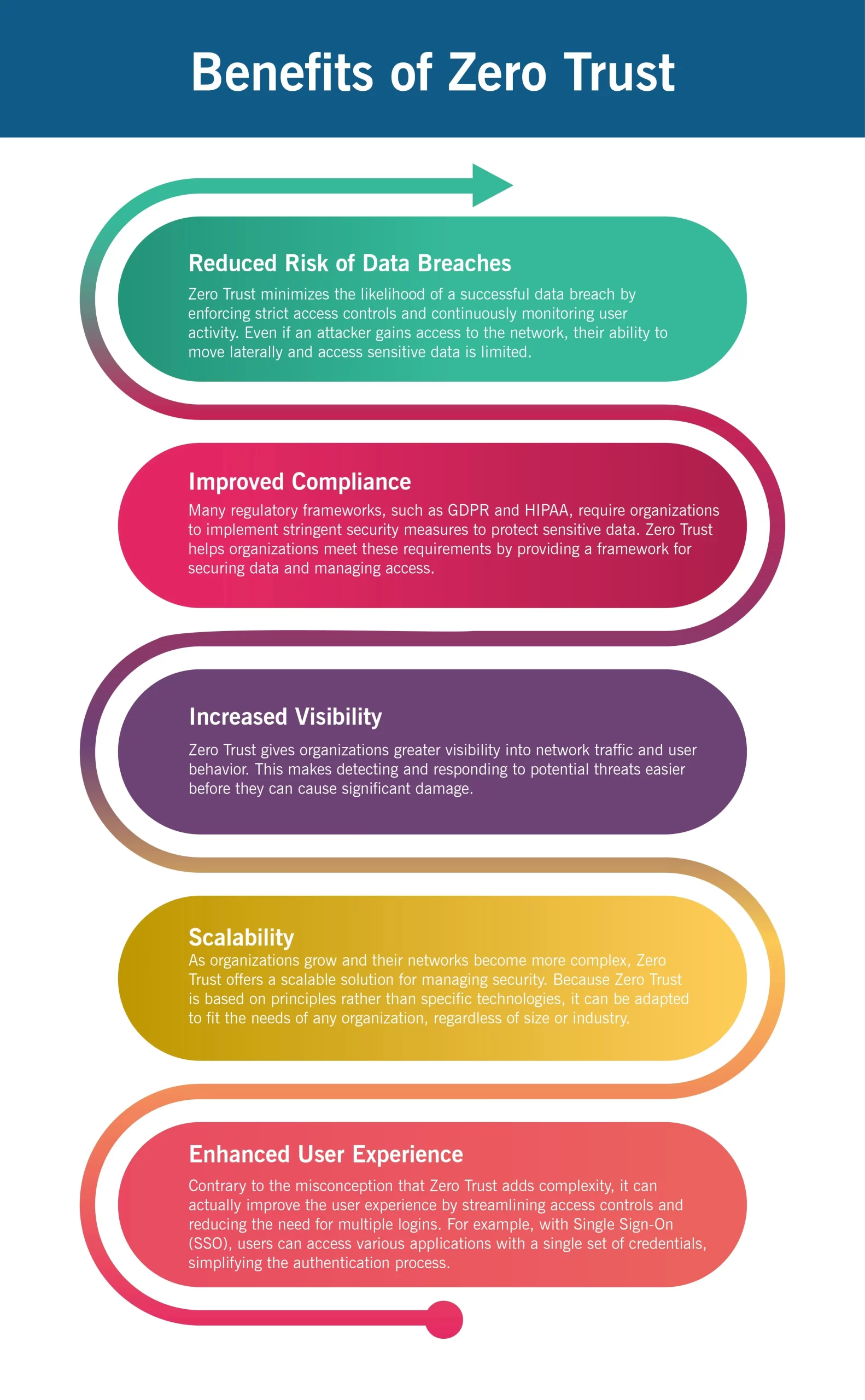
The Future of Zero Trust
Zero Trust’s importance will only increase as cyber threats continue to evolve. The model’s adaptability and focus on continuous verification make it well-suited to address modern cybersecurity challenges. However, the successful implementation of Zero Trust requires ongoing commitment, investment, and education.
Organizations must stay informed about emerging threats and continuously refine their Zero Trust strategies to stay ahead of attackers. By doing so, they can build a more resilient security posture that protects their assets, data, and reputation in an increasingly hostile digital environment.
Conclusion
Zero Trust represents a paradigm shift in how organizations approach cybersecurity. Eliminating implicit trust and enforcing continuous verification provide a robust protection framework against modern cyber threats. Implementing Zero Trust requires careful planning, a phased approach, and a commitment to ongoing education and improvement. However, the benefits of a successful Zero Trust strategy far outweigh the challenges, making it an essential component of any modern cybersecurity program.
ABOUT AUTHOR
Recent Posts
- Generative AI adoption risks you should address to safeguard your enterprise
- Everything You Need to Know About Quishing: The QR Code Scam You Can’t Ignore!
- A Business-Aligned Approach for GCC | Paramount
- 8 IAM Challenges Every Organization Faces and How to Tackle Them Using Identity Data Analytics
- How to Implement Identity & Access Management (IAM) Easily?

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.


