Blog
PAM Applications: How Privileged Access Management Enhances Cybersecurity

All organizations have certain user accounts with privileged access. These accounts have an additional layer of authority, permissions, and capabilities, allowing them to perform administrative tasks, access sensitive information, or even make changes to the IT infrastructure.
However, this deep level of access and control also makes them an attractive target to cybercriminals. If these accounts go unmanaged or are ever compromised, they can pose a serious threat to the organization, opening doors for serious data losses, system compromises, and fundamental IT threats. In fact, reports suggest that around 80% of data breaches result from stolen credentials or unauthorized access.
Fighting against this threat, Privileged Access Management (PAM) emerges as a critical line of defense, protecting an organization’s assets from unauthorized access. PAM refers to a collection of cybersecurity technologies and techniques that help businesses control, manage, and secure elevated access to their systems, applications, and data.
Let’s have a closer look at PAM’s applications, significance, and overall role in your organization’s data security system.
Importance of Privileged Access Management
Data breaches are a damaging event. On average, they can cost around $4.3 million. Protecting the privileged accounts from cyber-attacks, PAM prevents a significant chunk of threats and their implications. It plays a vital role in minimizing your organization’s attack surface and points of vulnerability, lowering the risk of data breaches.
The infamous SolarWinds hacks serve as a sobering reminder of the risks involved. In 2020, a group of cybercriminals exploited a new software vulnerability in SolarWinds by deploying malicious codes into its system, giving them unauthorized privileged access. The incident ultimately compromised numerous government agencies and Fortune 500 companies, leading to losses worth billions of dollars.
Incidents like these are a strong indicator of the importance of having a robust PAM solution.
Key Features & Benefits of Privileged Access Management
A PAM solution identifies the users, accounts, and processes requiring privileged access and specifies policies applicable to them with granular access controls.
The core of privileged access management features stands on the principles of least privilege, where users only receive the level of access they need to perform their job functions. PAM also includes real-time session monitoring, enabling prompt detection and responses to any security issues.

Use Cases and Applications of Privileged Access Management
The versatility of PAM applications extends across various scenarios, increasing security levels and reducing risk across different organizational situations.
For example, PAM solutions plays a pivotal role in securing administrative access to servers, databases, networking devices, and cloud resources. It allows IT administrators to control which account gets what access and improve overall security levels.
PAM can also create a centralized platform for managing privileged accounts, ensuring that only authorized personnel can perform administrative tasks. This reduces the number of people who have access to sensitive information, thereby diminishing the attack surface.
Moreover, PAM uses also extend to allowing third-party vendors or cloud providers (such as AWS or IBM Cloud) access to your organization’s data and applications. PAM reduces risk and offers secure, auditable channels for managing vendor access while protecting privileged accounts.
Let’s have a look at some real-world examples of PAM applications.
Another notable example is Walmart’s use of the BeyondTrust PAM solution. As one of the largest retailers in the world, with millions of customers, Walmart’s vast network of systems and data also presents a significant cybersecurity challenge.
BeyondTrust’s PAM solution allows Walmart to control access to its sensitive data and systems, providing visibility into all privileged activity. It provides the retail giant with an impressive level of control and oversight, ensuring the protection of customer information and the integrity of its operations.
Integration with Existing Security Infrastructure
An important aspect of the PAM solution is how seamlessly it blends with your existing security infrastructure.
The technology integrates with your broader Identity and Access Management (IAM) system, creating a cohesive security positioning. Working with IAM, PAM solutions can leverage existing user identities and access policies, streamlining the authentication and authorization process.
PAM can also integrate with Security Information and Event Management (SIEM) platforms, enabling you to centralize and analyze privileged access-related events, enhancing the overall incident response capabilities.

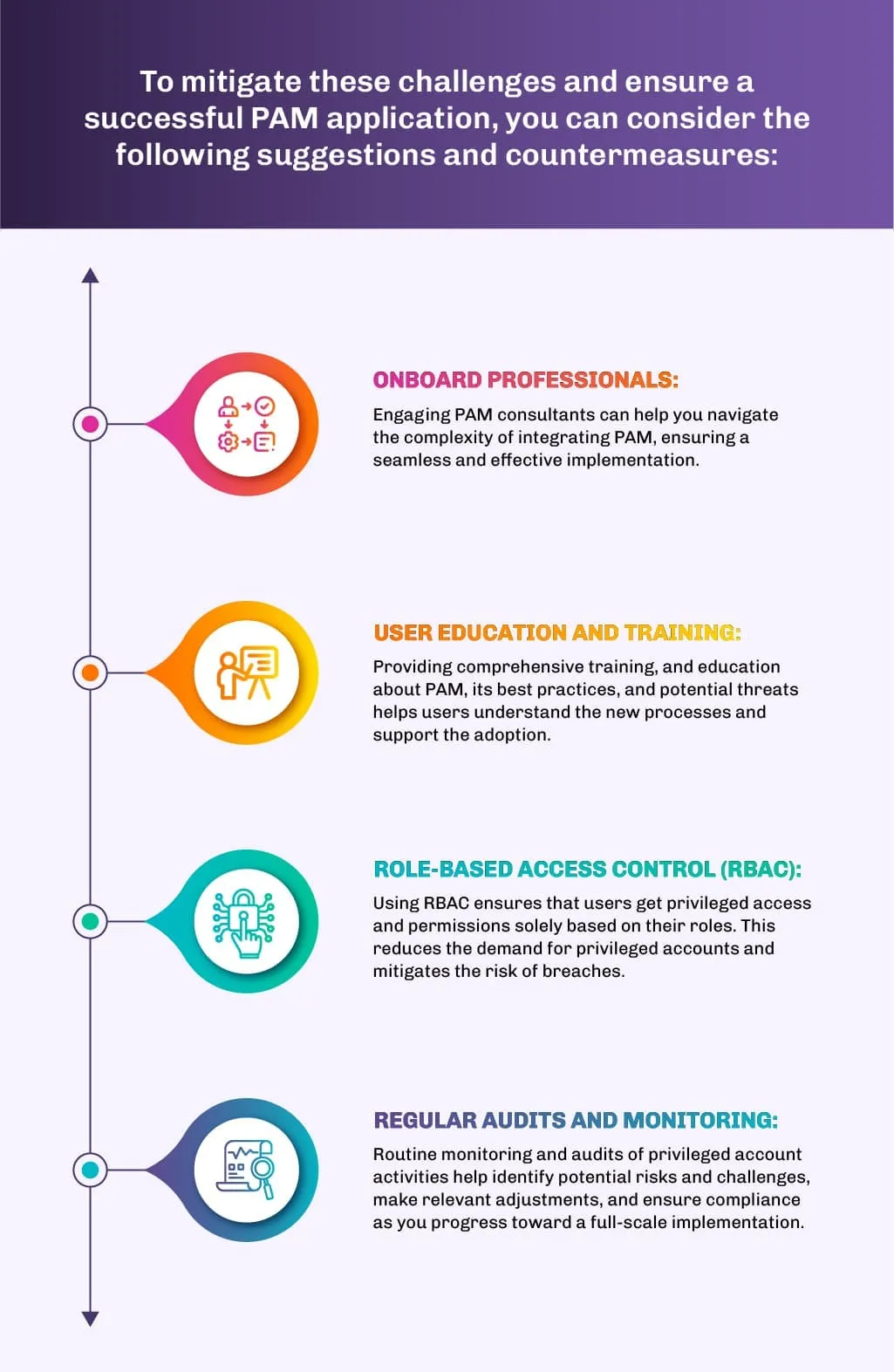
Future Trends in PAM
The field of PAM is constantly evolving, driven by emerging technologies and shifting cybersecurity landscapes. One notable trend that is taking the stage is the integration of AI and machine learning. PAM solutions enhanced with AI/ML can help identify anomalies and detect threats, helping organizations take preventive measures.
ML algorithms can also be trained to study user behavior patterns in privileged account activities, which can help detect suspicious patterns and revoke access whenever required.
In another trend, the concept of zero-trust architecture is gaining traction. It follows the approach that no entity should be trusted by default. The framework emphasizes the verification of every access request, regardless of the user’s location or device.
As per the current trends, the integration of AI/ML and zero-trust frameworks are all set to become integral parts of PAM solutions, reimagining the security posture of organizations as a whole.
Conclusion
With cybercriminals becoming smarter every day, it’s important for organizations to stay a step ahead. Implementing a PAM solution to protect their privileged account is no longer an optional task, but a necessity.
From mitigating the risks of insider threats and external attacks to ensuring regulatory compliance and improving operational efficiency, PAM solutions bring a suite of benefits that can significantly strengthen your IT infrastructure.
The solution can help you effectively manage and secure privileged accounts, reduce your attack surface, and minimize the potential risk of data breaches or system compromises. With these abilities, implementing PAM is becoming an increasingly relevant component of your cybersecurity strategy, especially in today’s unpredictable threat landscape.
However, to maintain a progressive approach and get the most out of a PAM solution, it’s also important to stay informed and keep in mind the emerging trends and technologies such as AI/ML and zero-trust architectures.
A well-informed, proactive approach toward implementing PAM, under the guidance of a trusted professional, can do wonders in fortifying your defenses, mitigating risks, and ultimately protecting your most valuable assets – your data, your reputation, and the trust of your customers and stakeholders.
ABOUT AUTHOR
Recent Posts
- Preparing for AI in Cybersecurity: A Strategic Guide for Businesses
- Everything You Need to Know About Passwordless Authentication
- Effective Data Security Strategies: A Comprehensive Guide for Middle Eastern Businesses
- Value-Driven Cybersecurity
- Generative AI adoption risks you should address to safeguard your enterprise

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.


