Blog
Best Practices for Implementing Robust OT Security

Best Practices for Implementing Robust OT Security
Introduction
In a world where operational technology (OT) powers everything from energy grids to manufacturing plants, the stakes for OT security have never been higher. Every networked device, every interconnected system, and every control mechanism is a potential gateway for threats that could disrupt entire industries. With cyber threats targeting critical infrastructures on the rise, implementing robust OT security is no longer optional—it’s a business imperative.
This blog dives into OT security best practices, giving you a clear path to safeguarding your systems and ensuring resilience in today’s dynamic threat landscape. Discover the strategies that can transform your OT security from a vulnerability into a competitive advantage.
Setting the Foundation for Robust OT Security
According to a report by ABI Research and Palo Alto Networks, 70% of industrial organizations faced cyberattacks in the past year, with a troubling 26% experiencing attacks on a weekly—or even more frequent—basis. These incidents not only led to immediate losses in data and revenue but also severely disrupted ongoing business operations, with a fourth of these organizations having to shut down due to the attacks.
Building a resilient OT security framework starts with a well-rounded operational technology strategy. An effective OT security strategy must focus on several foundational elements, each working to bolster the system’s defenses. By setting the groundwork for robust OT security, organizations can address unique vulnerabilities and challenges within OT environments and tailor their security approach to meet specific operational needs.
Essential Components of Robust OT Security Implementation
Implementing an effective OT security strategy requires understanding the various components that make up a secure OT environment. Below are key OT security best practices that lay the foundation for an effective security strategy:
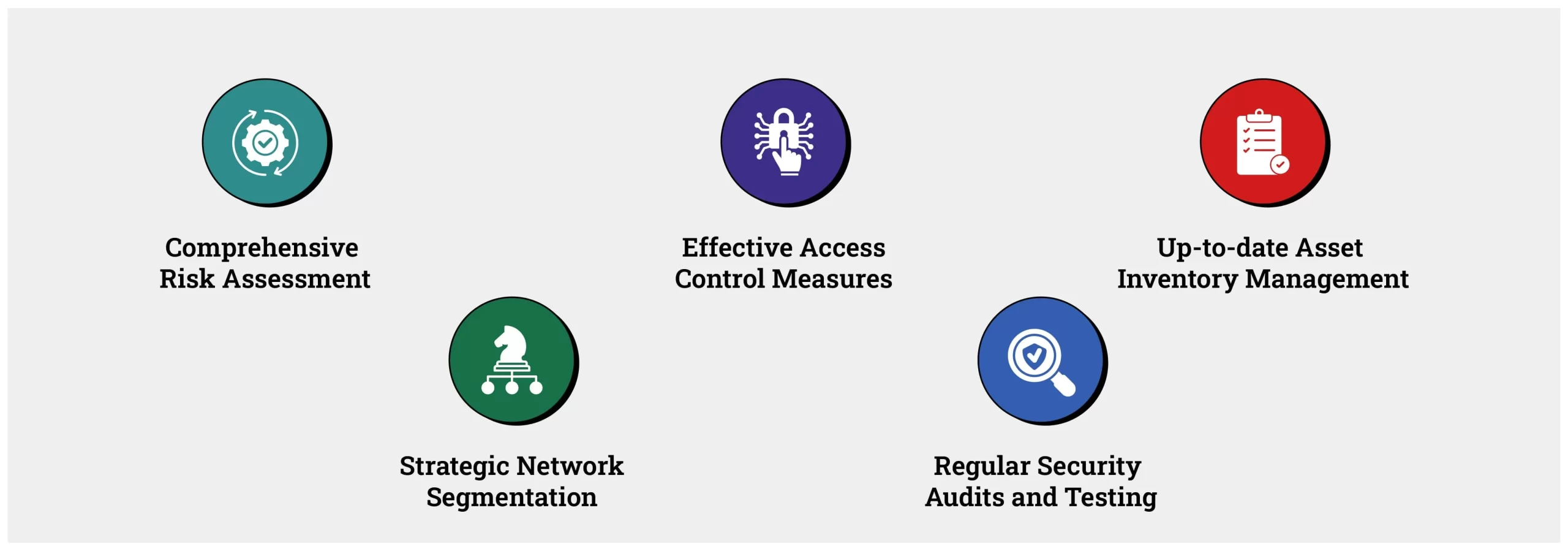
-
Comprehensive Risk Assessment:
The cornerstone of any OT security strategy, risk assessment identifies vulnerabilities specific to OT environments. Conducting thorough assessments allows organizations to pinpoint and mitigate risks unique to industrial systems, forming the first line of defense.
-
Effective Access Control Measures:
Access control is essential in managing who can interact with critical OT systems. Implementing multi-factor authentication, strict access protocols, and role-based permissions can prevent unauthorized access and protect sensitive data.
-
Up-to-date Asset Inventory Management:
Maintaining an accurate and updated inventory of all OT assets is a core security best practice. With a comprehensive inventory, organizations gain visibility into all devices, ensuring that security measures are applied consistently across the entire OT landscape.
-
Strategic Network Segmentation:
The Palo Alto survey revealed that 40% of respondents reported friction between their OT and IT teams, while only 12% indicated these teams were fully aligned. Isolating OT networks from IT networks and other critical components significantly reduces the risk of lateral movement during a cyberattack. Network segmentation helps contain potential threats, making it a valuable component of a robust OT security strategy.
-
Regular Security Audits and Testing:
Frequent security audits and penetration testing help organizations identify weaknesses and stay proactive in addressing vulnerabilities. Regular assessments are essential to any operational technology strategy, as they ensure systems are continuously protected against emerging threats.
Strategies for Achieving Robust OT Security
Organizations must keep in mind strategic OT security practices such as:

-
Incident Response Planning:
Establishing a tailored incident response plan is fundamental for OT security. A well-defined response plan ensures that teams can react quickly and efficiently in the event of a security breach, minimizing potential damage and downtime.
-
Employee Training and Awareness:
Employee training is a powerful tool in any OT security strategy. By fostering a culture of security awareness, organizations can mitigate the human factor, one of the leading causes of security incidents, ensuring that staff can recognize and respond to potential threats.
-
Integration of Advanced Technologies:
Advanced tools, such as AI and machine learning, have become essential in detecting anomalies within OT environments. Leveraging these technologies strengthens the operational technology strategy ensuring a more efficient and robust security system.
-
Collaboration Between IT and OT Teams:
A siloed approach can hinder security efforts, making collaboration between IT and OT teams a crucial OT security best practice. A unified approach allows teams to align their security practices, resulting in a more comprehensive and effective strategy.
-
Adherence to Regulatory Compliance:
Regulatory standards exist to ensure a minimum baseline of security. Over the next two years, 74% of executives across 16 countries anticipate increased regulatory pressures on OT security, reflecting heightened organizational awareness of the need for stronger OT security measures. This shift signals preparation for stricter standards and enhanced resilience across industries. Adhering to these regulations is not only a requirement but also a best practice, as compliance helps ensure that the operational technology strategy remains robust and in line with industry standards.
Overcoming Common Challenges in OT Security Implementation
Implementing OT security best practices comes with challenges; here are strategies to address common hurdles organizations may encounter:

-
Legacy System Integration:
Many OT environments rely on legacy systems that lack modern security features. Securing these systems requires specialized strategies, such as network segmentation and regular patching, ensuring that legacy components do not compromise the broader OT security strategy.
-
Resource Constraints:
Budget limitations are a common concern in OT security implementation. Focusing on high-impact OT security practices, such as access control and asset management, can help organizations establish a secure foundation without exceeding resource constraints.
-
Vendor Management:
Ensuring that third-party vendors adhere to OT security best practices is critical. Conducting regular audits and establishing clear security requirements for vendors can help mitigate risks introduced by external parties.
-
Complexity in OT Environments:
OT environments often consist of various systems and devices, adding layers of complexity. In the ABI Research study, over 60% of respondents pointed to the complexity of OT security solutions as a significant challenge when selecting security software and equipment. This finding underscores the demand for simpler, more streamlined security solutions tailored to OT environments. Implementing scalable OT security practices that can adapt to different systems and environments simplifies the overall security management process.
Conclusion
In today’s rapidly evolving threat landscape, robust OT security is a vital component of long-term business resilience. With global OT security spending projected to soar from USD 20.7 billion in 2024 to USD 44.9 billion by 2029, the demand for robust security strategies has never been more urgent. As regulations tighten and cyber risks grow more complex, the need for effective, actionable security strategies becomes essential. By embracing OT security best practices, organizations can not only protect their critical systems but also gain a strategic advantage.
To build a security framework that meets these demands, trust in a partner like Paramount Assure—where expertise in OT security ensures your operations remain secure, compliant, and future-ready.
Explore Paramount for tailored solutions to safeguard your organization.

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
