Blog
How to Choose the Best Authentication Method for Your Business in 2025

How to Choose the Best Authentication Method for Your Business in 2025
In 2025, cyber threats are no longer a distant concern, they’re a daily reality. Ransomware, phishing, credential stuffing, and data breaches are hitting businesses of all sizes. Whether you’re running a growing startup or a global enterprise, protecting your systems and sensitive data isn’t optional anymore, it’s essential. And one of the most critical front-line defences in your cybersecurity toolkit is secure authentication for business.
Choosing the best authentication method for your business isn’t just a technical decision. It’s a strategic one that directly impacts user experience, regulatory compliance, and long-term scalability. With a growing number of authentication methods for businesses in 2025, selecting the right solution can feel overwhelming.
In this blog, we’ll unpack the various types of authentication methods, explain what makes each one effective or flawed, and walk you through how to choose an authentication method that aligns with your company’s needs. Whether you’re revisiting your existing system or starting fresh, this guide will help you make a confident, informed decision.
What Is Authentication and Why Does It Matter in 2025?
Authentication is the process of verifying that a user is who they claim to be before granting access to a system, application, or data. It might sound straightforward, but poor authentication choices are often the weakest link in a business’s security posture.
As we move further into 2025, the importance of business authentication solutions has increased exponentially. This is partly due to the rise of hybrid work environments, more sophisticated cyber attacks, and new regulatory frameworks that demand stronger user verification, think Zero Trust models and mandates around Multi-Factor Authentication (MFA) for certain sectors.
Authentication isn’t just about ticking a compliance box; it’s about reducing the risk of costly breaches while keeping workflows smooth and user-friendly. If your system makes it hard for users to log in securely, they’ll find workarounds, and that’s when security breaks down.
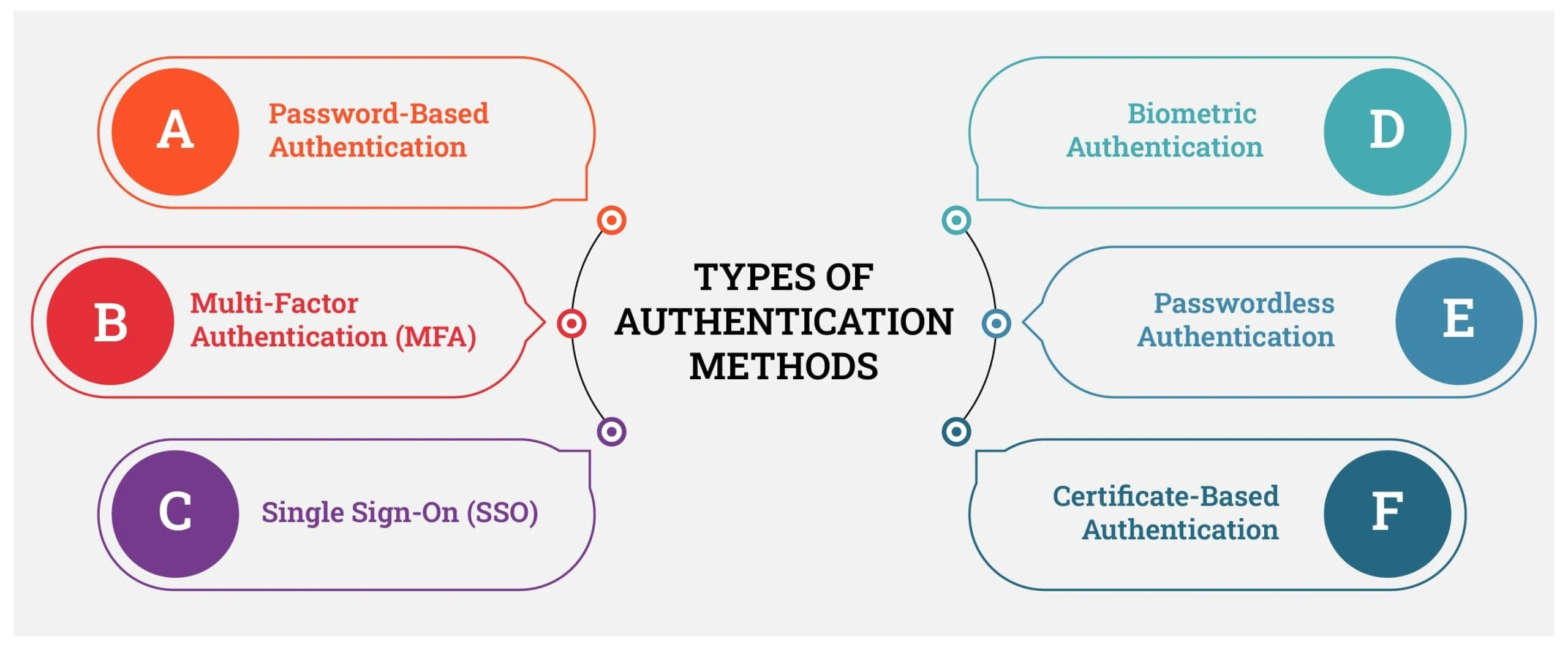
Types of Authentication Methods
There’s no one-size-fits-all approach. The types of authentication methods available in 2025 vary widely in complexity, usability, and security strength. Let’s take a look at the main ones businesses are considering today:
A. Password-Based Authentication
Still the most widely used method, but easily the most flawed. Passwords are vulnerable to brute-force attacks, phishing, and leaks, especially if users are recycling weak passwords across platforms.
- Pros: Easy to implement and familiar to users
- Cons: Weak security unless paired with other methods
- Best for: Low-sensitivity access where speed is more important than strict security
Despite its ubiquity, relying solely on passwords is no longer considered a secure authentication for business. If you still use password-only systems in 2025, you’re already a step behind
B. Multi-Factor Authentication (MFA)
MFA boosts security by combining two or more credentials: something you know (password), something you have (phone, token), and something you are (biometrics).
- Pros: Stronger defence against phishing and stolen credentials
- Cons: Can introduce friction if poorly implemented
- Best for: Most businesses, especially those handling sensitive or regulated data
MFA adoption has soared in recent years, and for good reason. For many companies, it’s the minimum requirement when thinking about the best authentication method for business.
C. Single Sign-On (SSO)
SSO allows users to log in once and gain access to multiple connected systems. It’s ideal for organisations juggling dozens of apps and services.
- Pros: Streamlined user experience; fewer forgotten passwords
- Cons: If compromised, access to multiple apps is at risk
- Best for: Medium to large enterprises prioritising employee efficiency
SSO works best when paired with strong authentication mechanisms in the background, such as MFA or passwordless authentication for businesses.
D. Biometric Authentication
Biometrics use unique physical traits to verify identity, think fingerprints, facial recognition, or even retina scans.
- Pros: Difficult to fake or share
- Cons: Privacy concerns and higher setup costs
- Best for: High-security environments like finance, healthcare, or defence
Biometrics are rapidly becoming a core part of business authentication solutions, especially when combined with other methods in a layered strategy.
E. Passwordless Authentication
This is where things get exciting. Passwordless authentication for businesses eliminates the weakest link, passwords. Instead, it relies on secure hardware tokens, biometric recognition, or magic links sent via email or app.
- Pros: Frictionless login and fewer attack surfaces
- Cons: Requires upfront investment in compatible systems
- Best for: Organisations seeking long-term, scalable security
In 2025, passwordless authentication for businesses will be the future of user-friendly security.
F. Certificate-Based Authentication
This method uses digital certificates and cryptographic keys to authenticate users or devices. Often used in B2B environments, it’s part of a broader Public Key Infrastructure (PKI) strategy.
- Pros: Very secure and ideal for machine-to-machine communication
- Cons: Requires complex setup and management
- Best for: Enterprises dealing with partners, vendors, or high-value data transactions
Factors to Consider When Choosing the Right Authentication Method
There’s no universal answer to how to choose an authentication method that fits every business. What works for a cloud-first SaaS startup won’t necessarily suit a healthcare provider handling patient records or a law firm dealing with confidential legal documents. When evaluating authentication methods for businesses in 2025, here are the key factors that should guide your decision-making:
A. Business Size and Structure
The size and complexity of your organisation play a big role in selecting the best authentication method for business. A small team working from a shared office may get by with simpler solutions, while a large enterprise with multiple departments, remote teams, and third-party collaborators will need more robust, scalable systems.
For example, a company with hundreds of employees accessing multiple cloud services daily may benefit from Single Sign-On (SSO) combined with Multi-Factor Authentication (MFA) to balance ease of use and strong security.
B. Type of Data You Handle
Not all data carries the same weight. If your systems store or process sensitive customer information, intellectual property, or financial records, your business authentication solutions must offer a higher level of protection. For businesses in sectors like finance, healthcare, or e-commerce, secure authentication for business isn’t just nice to have, it’s non-negotiable.
You might also consider certificate-based authentication if you’re dealing with high-value data exchanges between machines or external partners, as it provides a strong trust framework and data integrity.
C. Compliance and Regulatory Needs
Compliance requirements are becoming stricter across industries. From GDPR and HIPAA to PCI-DSS and industry-specific data protection mandates, there is an ongoing pressure to adopt authentication methods for businesses in 2025 that meet regulatory standards.
For instance, many regulations now explicitly require MFA or equivalent levels of identity assurance. Choosing an authentication method that aligns with these requirements will save you from legal headaches and fines down the line.
D. User Experience and Friction
Security should never come at the cost of usability. If your authentication system frustrates users with slow, clunky login processes, you risk poor adoption, or worse, people bypassing security protocols altogether.
Passwordless authentication for businesses is gaining traction in 2025 largely because it improves user experience while boosting security. Methods like biometric login or magic links offer low-friction access without sacrificing protection. This is particularly helpful in customer-facing platforms where ease of use is a competitive advantage.
E. Cost and IT Infrastructure
Budgets matter. So do internal resources. While a sophisticated biometric system might sound appealing, it may not be feasible for a company with limited IT support or a tight budget. Cloud-based business authentication solutions have made high-grade security more accessible, but implementation and maintenance costs can still vary significantly.
Before choosing a solution, assess your existing infrastructure. If your company already relies heavily on Microsoft or Google ecosystems, look for authentication tools that integrate well and don’t require major overhauls.
F. Integration with Existing Systems
No matter how strong or innovative an authentication method is, it won’t help much if it clashes with your current tech stack. Seamless integration is critical for day-to-day operations. Compatibility with existing identity management platforms, CRMs, and internal applications should be a top consideration.
Many modern providers offer APIs and plug-ins that allow their tools to blend into your existing workflows. The smoother the integration, the faster your team can adapt and the more likely you are to see a quick return on investment.
Best Authentication Practices for Businesses in 2025
Having the right authentication system in place is only part of the picture. The real strength of business authentication solutions lies in how well they’re implemented, maintained, and adapted over time. In 2025, simply setting up MFA or SSO and calling it a day won’t cut it. Businesses need to think smarter, act proactively, and treat authentication as a living part of their overall security posture.
Here are the top best authentication practices for businesses in 2025, based on what actually works in real-world environments:
1. Use Layered Authentication (Don’t Rely on Just One Method)
Think beyond single-point solutions. Relying on one mechanism, even something strong like biometrics, creates a single point of failure. The best approach is layered or adaptive authentication. Combine methods like Multi-Factor Authentication (MFA), Single Sign-On (SSO), and passwordless authentication for businesses to balance usability and security.
For example, you could require an employee to use biometrics on their mobile device, then enter a time-sensitive code for access to high-risk systems. The point isn’t to make users jump through hoops, but to apply the right level of control based on risk.
2. Regularly Review and Audit Authentication Policies
Your authentication setup should never be “set and forget.” Technology changes, threats evolve, and your business grows, so what worked last year might now be a liability.
Conduct scheduled audits of your authentication systems. Ask:
- Are we still using any outdated or vulnerable methods?
- Have we added new apps or users without updating permissions?
- Do our authentication methods for businesses in 2025 still comply with regulations?
This isn’t just about technical hygiene. It’s about making sure your secure authentication for business evolves with your needs.
3. Train Your People, Constantly
The weakest point in any security system is the human using it. You can have the most sophisticated business authentication solutions, but they’ll fail if your staff keeps falling for phishing links or sharing credentials on sticky notes.
Train your team regularly. Not just one-time onboarding, but ongoing awareness programmes that reflect new threats. Teach users how to recognise social engineering, why they shouldn’t reuse passwords (even with MFA), and how to report suspicious behaviour.
Don’t forget leadership either, attackers often target executives using spear-phishing and social engineering. Training should start at the top.
4. Embrace Adaptive and Context-Aware Authentication
Context-aware or risk-based authentication is becoming standard in authentication methods for businesses in 2025. These systems evaluate login attempts based on user behaviour and environment. For instance, if someone logs in from a known device at 9 a.m. in London, they get access quickly. But if the same credentials are used from an unknown IP address in another country, the system might ask for additional verification.
Adaptive authentication improves both security and user experience by not applying blanket rules. It only increases friction when there’s a good reason, reducing frustration for your users and making attacks far harder for bad actors.
5. Prioritise Mobile-Friendly Authentication
With remote and hybrid work firmly established, many employees now access systems from mobile devices. That means your business authentication solutions must work seamlessly on phones and tablets. Whether it’s biometric login, mobile push notifications, or app-based one-time codes, mobile-first support is no longer optional.
In particular, passwordless authentication for businesses often shines in mobile settings, where facial recognition or device-based trust is already in place. A poor mobile experience can lead users to delay updates, avoid MFA prompts, or worse, find insecure shortcuts.
6. Prepare for Scalability from Day One
A common mistake is choosing an authentication system that works today but can’t grow with your company. Whether you’re expanding into new markets, hiring rapidly, or integrating third-party tools, your authentication approach needs to be flexible and scalable.
Look for business authentication solutions that support:
- Role-based access controls
- Easy onboarding and offboarding
- API integrations with HR and IT systems
- Cloud and hybrid deployment options
The best authentication method for your business in 2025 is one that doesn’t need to be ripped out and replaced in a year.
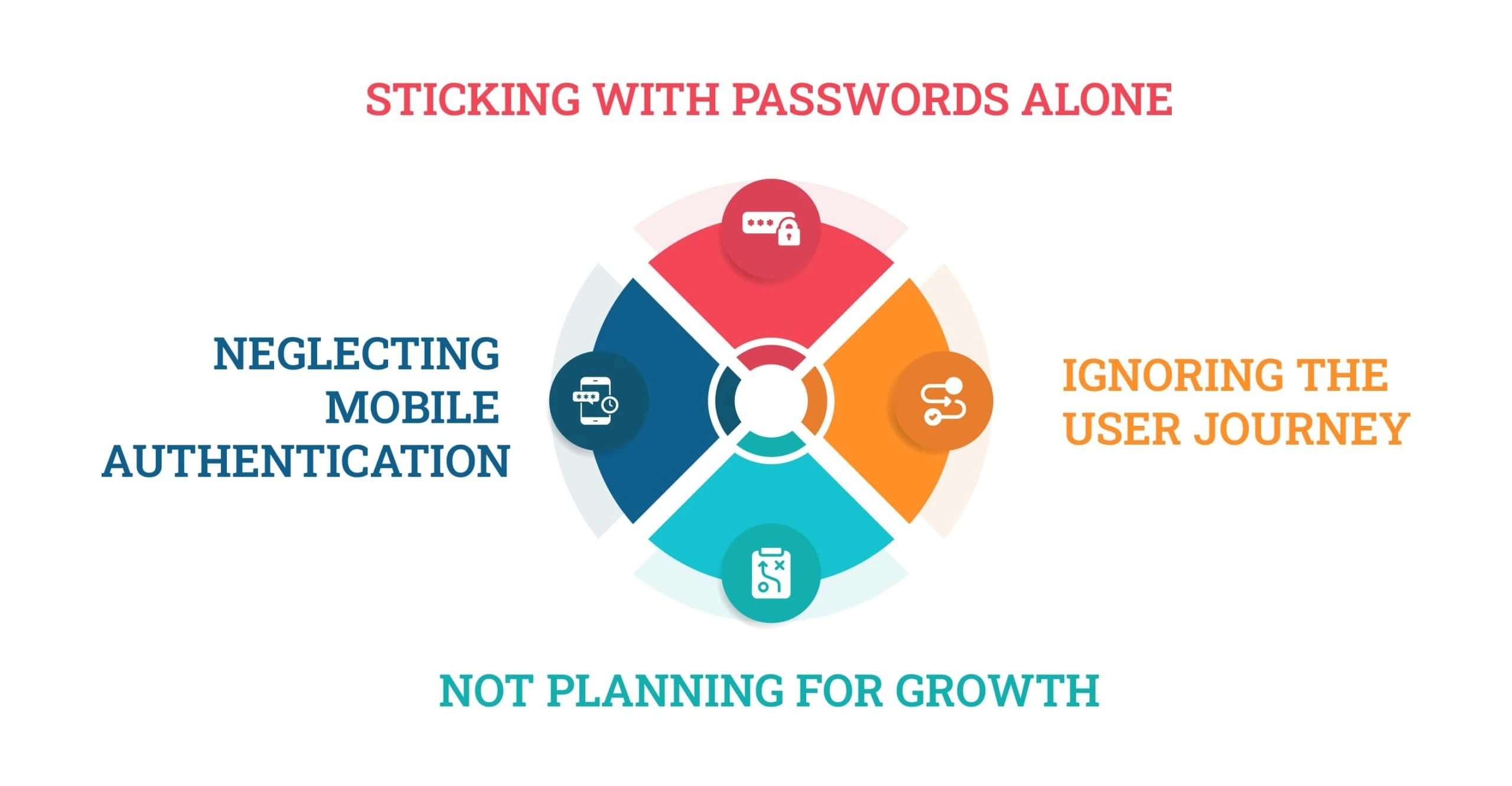
Common Mistakes to Avoid
Even with the best intentions, many businesses fall into traps when choosing and implementing authentication methods for businesses in 2025:
- Sticking with passwords alone: It might be easy, but it’s just not secure anymore.
- Ignoring the user journey: Overly complex logins frustrate users and lead to workarounds.
- Neglecting mobile authentication: In a remote/hybrid world, mobile-friendly solutions are critical.
- Not planning for growth: Today’s solution should still work tomorrow. Think ahead and choose scalable tools.
Paramount’s Take: Choosing Smart, Scalable Authentication Solutions
At Paramount, we work closely with businesses to assess their current systems and help implement the best authentication method for businesses based on size, industry, and risk profile. Whether you need a simple SSO setup, a robust MFA rollout, or want to transition to passwordless authentication for businesses, our advisory and managed security services ensure it’s done right the first time.
We don’t just recommend, we execute. Our team handles integration, employee onboarding, compliance mapping, and performance optimisation. This way, you’re not just choosing from a list of business authentication solutions, you’re building a smarter, more secure foundation for the years ahead.
Conclusion
Authentication in 2025 isn’t a nice-to-have, it’s fundamental. With new cyber threats appearing every day and regulatory pressure mounting, businesses need to invest in smarter, more resilient authentication strategies.
Whether you go with MFA, SSO, biometrics, or a passwordless authentication for businesses model, the key is finding the right fit for your company’s needs. Don’t settle for outdated solutions or one-size-fits-all approaches. Take a closer look at your infrastructure, your users, and your goals.
If you’re still unsure how to choose an authentication method that works for your business today, and in the future, Paramount is here to help.
Get in touch with our experts to secure your organisation with tailored, future-ready authentication solutions.

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
