Blog
10 Tips to examine while implementing zero trust model

Shifting to a Zero Trust Network Access Model from a traditional Virtual Private Network (VPN) model can be a significant undertaking for an organisation. It entails fundamental shift in security architecture from trusting everyone entering the perimeter network to trusting nobody.
In the fast-growing IT landscape and ever-increasing cyber threats, to stay ahead of the game organisations may jump on the bandwagon of shifting to Zero Trust. However, the high spirits may be dampened if appropriate planning and execution are not done carefully.
While transition can greatly enhance security, but it also presents several challenges. Information is power. Learn before you leap: So, it is vital for every organisation to have complete understanding of Zero Trust Network Access approach, what it takes to adapt to new systems, and challenges associated with implementation of the same.

What is Zero Trust Network Access?
Shifting to a Zero Trust Network Access Model from a traditional Virtual Private Network (VPN) model can be a significant undertaking for an organisation. It entails fundamental shift in security architecture from trusting everyone entering the perimeter network to trusting nobody.
In the fast-growing IT landscape and ever-increasing cyber threats, to stay ahead of the game organisations may jump on the bandwagon of shifting to Zero Trust. However, the high spirits may be dampened if appropriate planning and execution are not done carefully.
While transition can greatly enhance security, but it also presents several challenges. Information is power. Learn before you leap: So, it is vital for every organisation to have complete understanding of Zero Trust Network Access approach, what it takes to adapt to new systems, and challenges associated with implementation of the same.
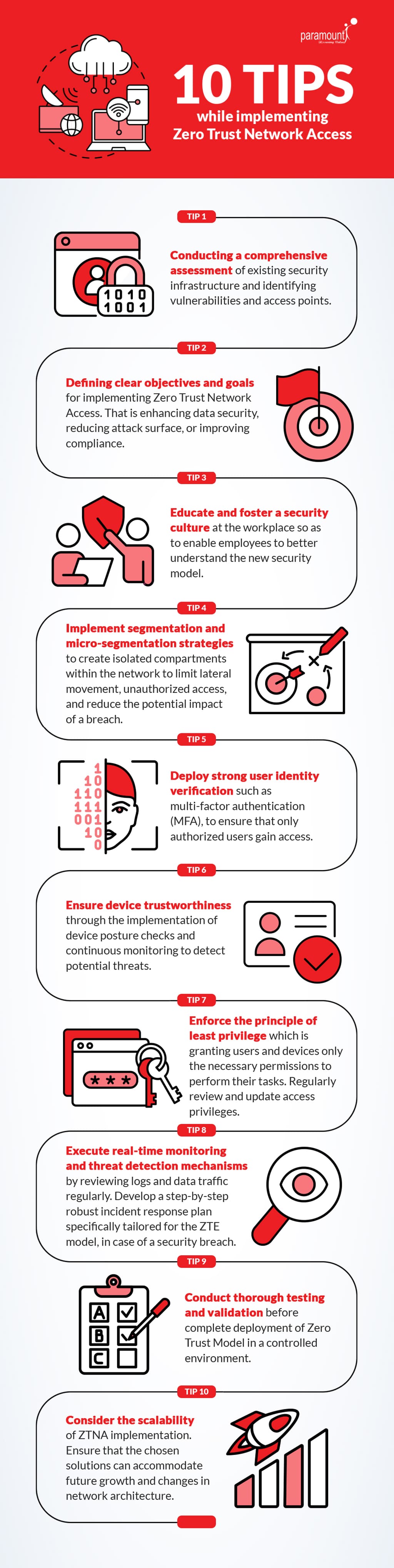
Implementing Zero Trust solutions may involve significant changes to your existing network and security infrastructure. For a smooth transition, consider engaging with industry experts or hiring consultants to assist with the implementation process. Their expertise can help streamline the transition and provide valuable insights and guidance, and stay informed about the latest security threats and best practices.
ABOUT AUTHOR
Recent Posts
- Best Practices for Maintaining Regulatory Compliance in Middle East
- Never Trust, Always Verify: Why Zero Trust is the Key to Modern Cyber Defense
- Ransomware attack on Chinese bank’s US subsidiary another warning signal
- Clearing the Air on Cloud Security: Myths, Facts, & Benefits
- Maximize Cybersecurity with Existing Cloud Investments | Paramount

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.

