Blog
Cybersecurity Lessons from the Cyberattack on MGM Resorts

As the world becomes more digital, cybersecurity threats are on the rise. More cyberattacks are occurring, and perpetrators are unleashing new types of cyberthreats on enterprises and individuals. Between January and October 2023 alone, 5+ billion records have reportedly been breached*. The ransomware attack on MGM Resorts International (MGM), the global hospitality and entertainment enterprise whose properties include MGM Grand, Mandalay Bay and Bellagio, provides important security lessons to CISOs, CSOs and other business leaders. It reinforces the need to view cybersecurity as more than a ‘tech’ domain because actors are increasingly exploiting human psychology.
*(source: https://www.itgovernance.co.uk/blog/list-of-data-breaches-and-cyber-attacks-in-2023)
The event and its impact
MGM reported that on Sept 11 2023, its computer networks and systems were hit by a cyber-attack. It is believed that a group calling themselves ‘Scattered Spider’ was behind the attack. The loss due to disruptions to operations and the costs of fixing the systems are expected to hit the company’s Q3 earnings by US$100 million (including a one-time cost of US$10 million). It took 10 days to restore operations, and even then, some functionalities were not available. The shutdown affected slot machines, hotel room keys, records of winnings etc., causing customers at MGM properties to experience a nightmare. The incident has shaken customer. Nobody is quite sure what personal/financial data has been exfiltrated from MGM’s systems, and what consequences this may have for individual customers.
The modus operandi
Although it will take more time to get an accurate picture of how exactly this cybersecurity attack was implemented, cybersecurity experts have reconstructed the event based on available evidence.
The attackers used a combination of human and technology vectors. Specifically, a social engineering technique known as ‘vishing’ (voice phishing) is believed to have been employed. The method involves using phone calls to identified human targets (or someone affiliated to them) to extract sensitive information that is used for further actions. Sometimes, the attackers ask targets to perform some actions that directly compromise security.
Experts feel that the hackers’ starting point was MGM usernames and passwords obtained from earlier breaches. Using additional information obtained from the LinkedIn profiles of certain ‘high value’ individuals (those likely to have a high level of access privileges to MGM’s security and other infrastructure), the perpetrators convinced MGM’s help desk to somehow bypass the multi factor authentication protocols.
After the initial infiltration, the attackers consolidated their control over critical infrastructure, enabling them to unleash chaos. Having gained access to MGM’s network, the attackers used the ‘inbound federation’ feature of MGM’s IAM (Identity and Access Management) solution to create persistence. Using BlackCat/ALPHV’s ‘Ransom as a Service’, the attackers encrypted a large number of MGM’s ESXi servers (Virtual Machines) that supported various systems. As the servers got impacted, the applications running on them crashed, affecting check in/check out, slot machines, room keys, table reservations, etc.
By this time, the attackers reportedly gained privileged access to accounts that managed MGM’s IAM infrastructure, including its IDP (Intelligent Document Processing) solution. This gave them control of MGM’s Microsoft Azure cloud environment.
STRATEGIC LEARNINGS FOR CISOs AND CSOs
This attack has taught cybersecurity professionals tactical lessons around configuration, how functionalities (not bugs) in IAM solutions can be exploited, implementation gaps, process/workflow weaknesses etc. CISOs/CSOs and others must appreciate the strategic dimensions of this attack in order to minimize the risk of future attacks.

HOW ENTERPRISES CAN PROTECT THEMSELVES FROM CYBERATTACKS
When it comes to cybersecurity, prevention is always better than cure. The actions listed below can strengthen the level of cybersecurity in your enterprise.
Consider buying cyberinsurance: In addition to mitigating the financial risks associated with breaches, this will force management attention and resource allocation to putting in place cybersecurity measures.
Given how cyberthreats can originate, effective cybersecurity needs multi-pronged actions. Some of these are easy to implement, while others require a high degree of technical skills.
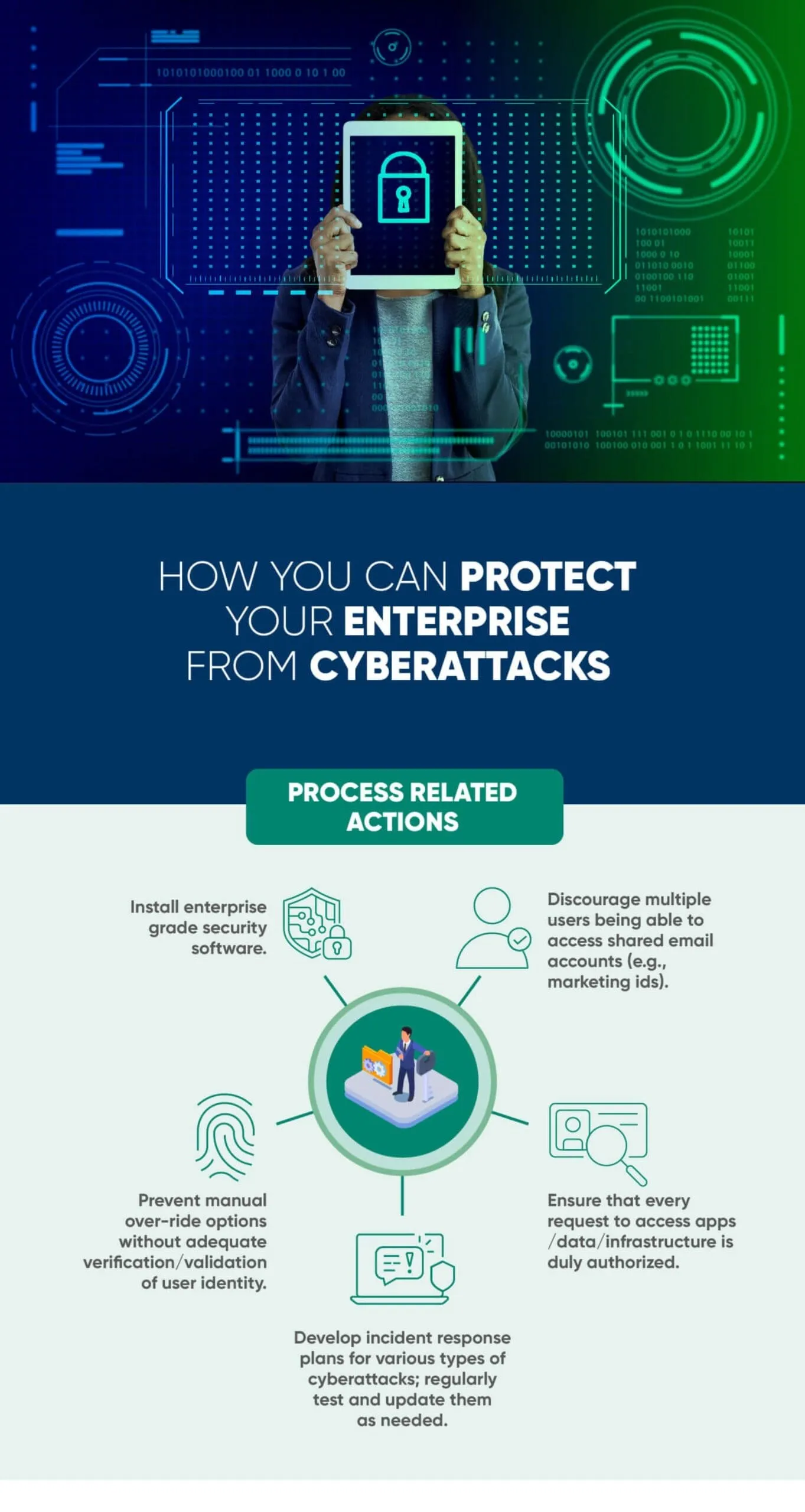
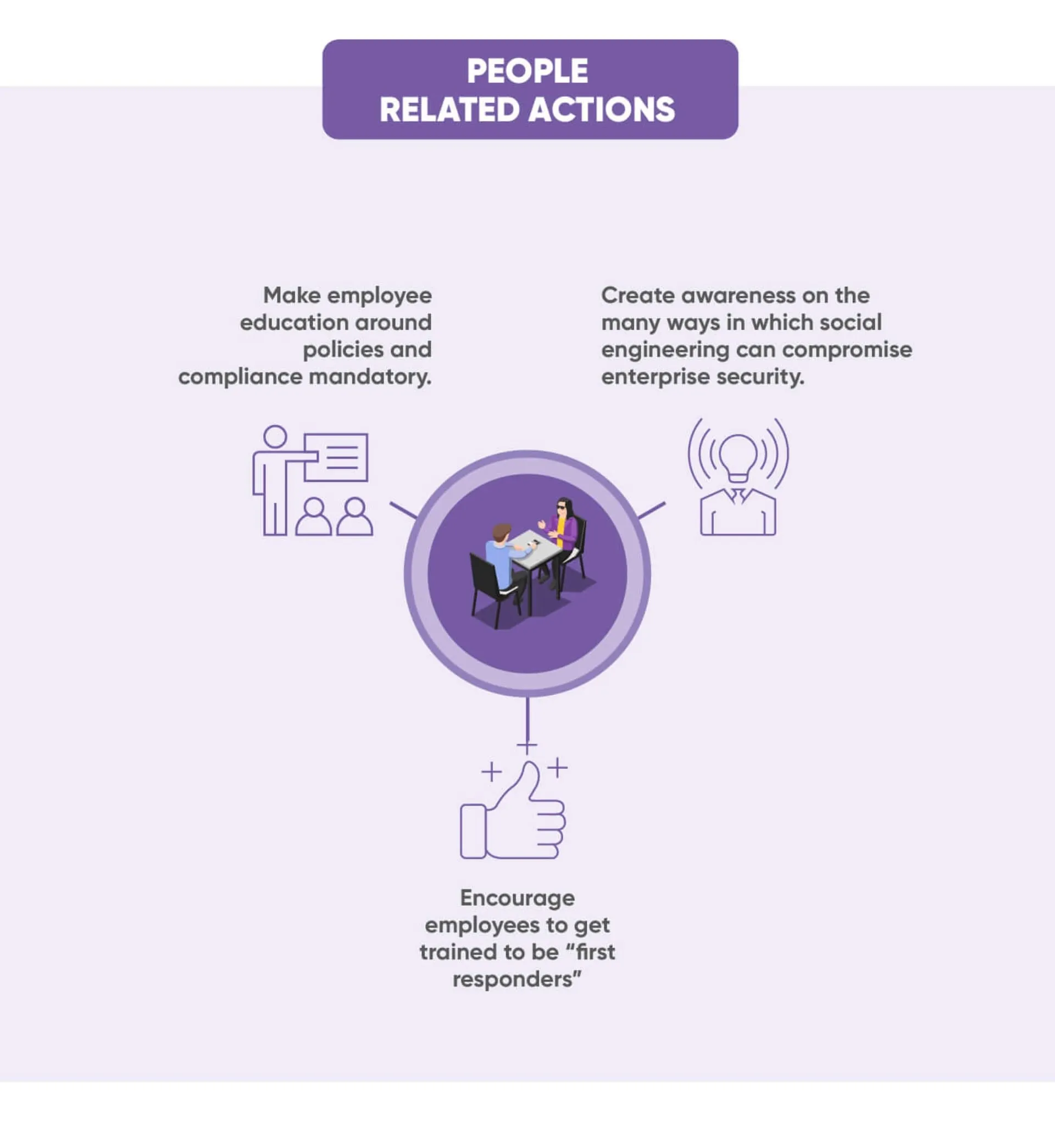
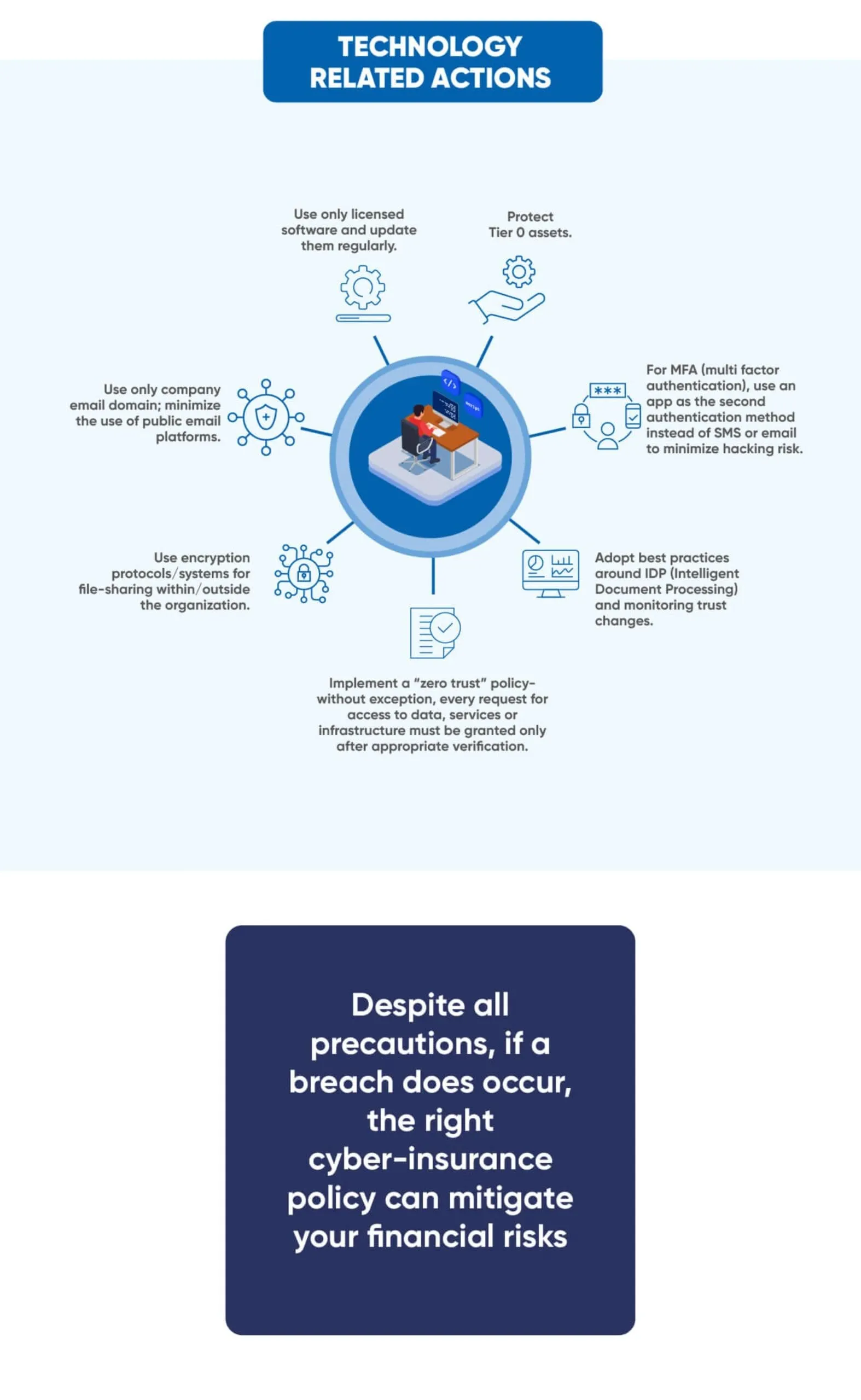
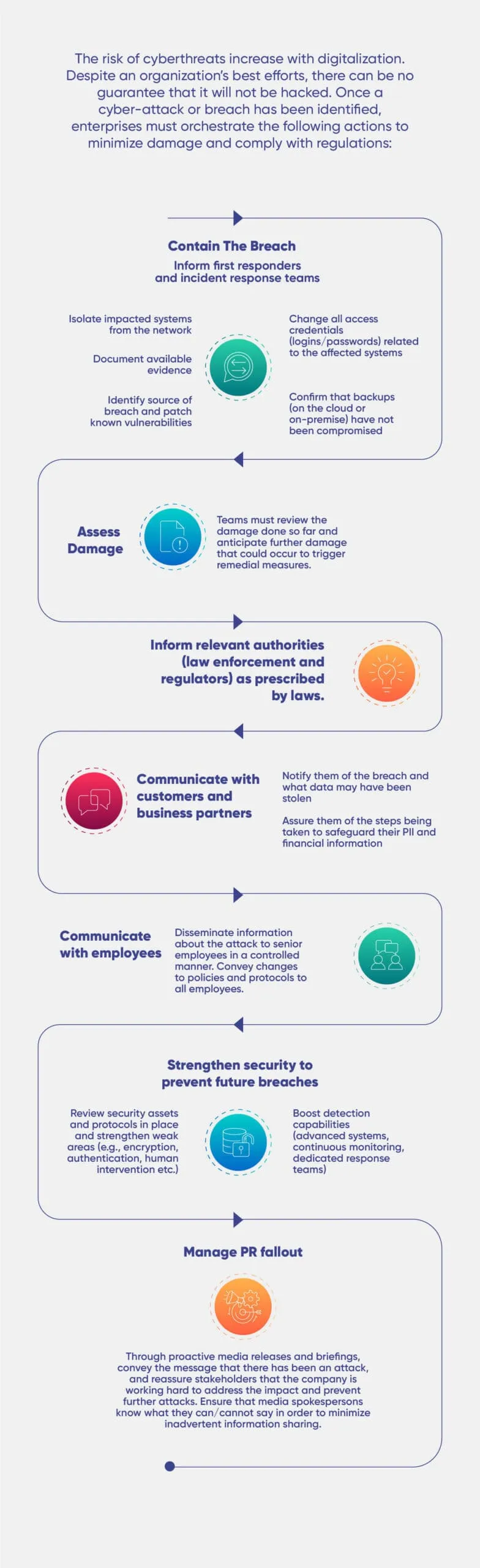
WHAT ENTERPRISES SHOULD DO IF THEY ARE HACKED
The risk of enterprises falling prey to various kinds of cyberattacks is rising. Although innovative cybersecurity solutions continue to evolve, threat actors are becoming more capable of beating them. Any chain is only as strong as the weakest link: one careless or ill-informed employee (or a friend/family member using the official device) can put enterprise security at risk. Specific responses and the sequence in which these actions need to be taken depend on the nature of the cyberattack, what parts of the IT stack have been impacted, and the type of business operations.
Once a cyber-attack or breach has been identified, enterprises must take the following steps to minimize damage and get back to normal at the earliest:
We at Paramount Assure https://paramountassure.com/ can help you review your existing cybersecurity measures and advise you on what more you can do to strengthen them. We can also help implement various cybersecurity defences in your enterprise. To schedule a discussion with our experts, write to us on [email protected].
ABOUT AUTHOR

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.


