Blog
Passwordless authentication: The Open Sesame route to more secure digital enterprises

Password-based authentication is becoming a big cybersecurity risk
To paraphrase Stephen Covey, when you pick up one end of a stick, you pick up the other end as well. This prescient observation applies to digitalization as well. Across industries, as B2B, B2C and D2C enterprises embrace higher levels of digital transformation, the quantum and scope of security risks associated with “digital” also increase. For decades, passwords have been used to authenticate user identity prior to allowing them access to various applications and software systems. Employees, business partners, customers, and other service providers all need to be authenticated.
There are many drawbacks associated with passwords. They can easily be compromised, either because users choose easy-to-hack passwords or hackers use sophisticated algorithms. Techniques like phishing etc. make it easier for fraudsters and scamsters to gain access to passwords even without the users’ knowledge. Users tend to reuse passwords across apps, which increases the risk of breaches through credentials stuffing and password spraying. Often, users just forget passwords. The reset process can be annoying, but being locked out is worse. The need to change passwords every few months also affects user experience. From an internal perspective, password-based authentication is expensive for enterprises; they are also a burden for IT teams to manage.
Give your enterprise superior protection with Passwordless Multi Factor Authentication
Over the past decade, Two Factor Authentication emerged as a way to reduce the risk of relying only on a single password by adding a second “factor” (i.e., basis for identity verification and authentication). Unfortunately, cybercriminals are more than keeping pace with such innovations. They are evolving sophisticated new methods to exploit vulnerabilities in apps, devices, and other authentication processes employed by enterprises.
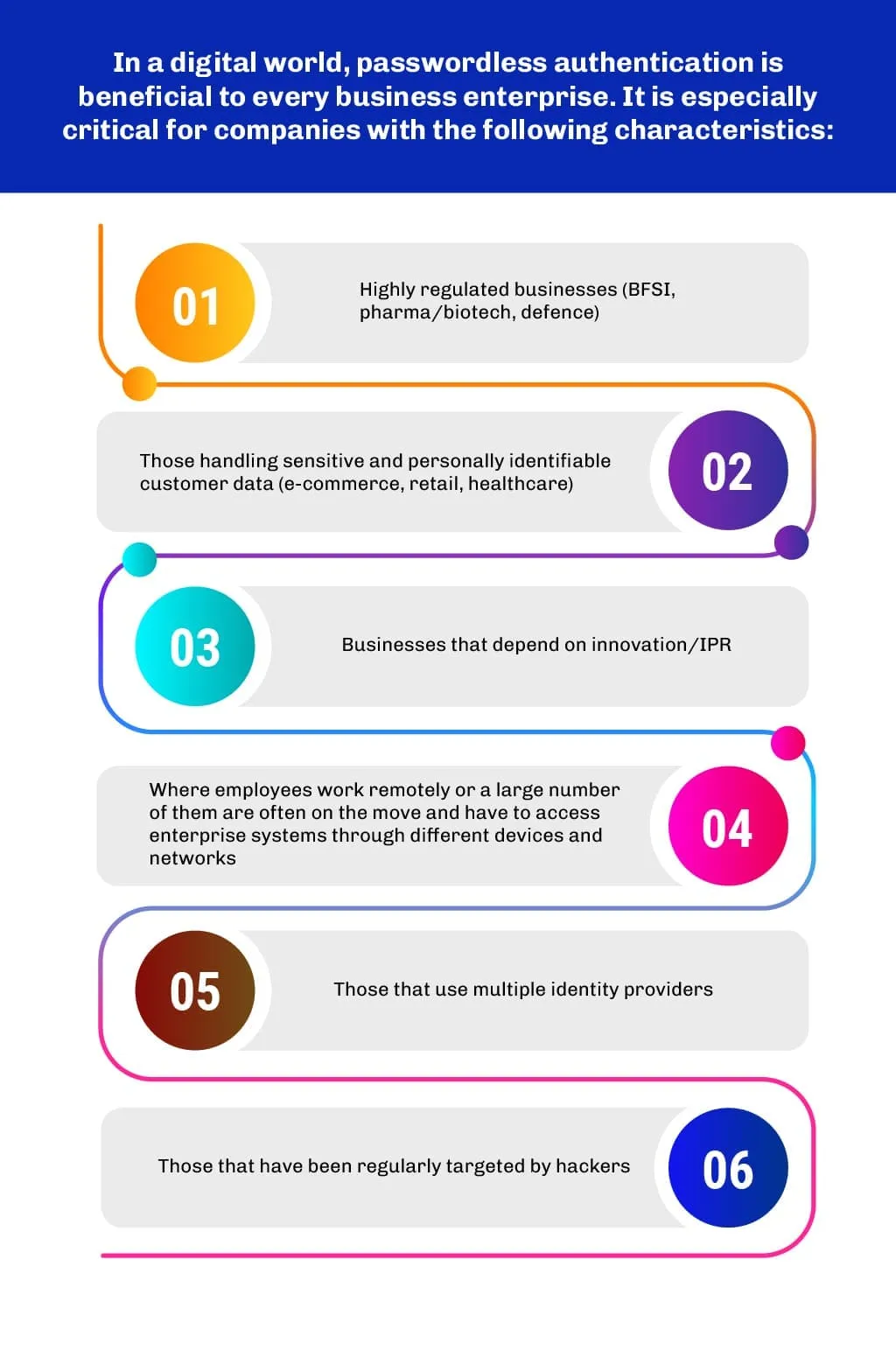
As a stakeholder category, employees access internal systems the most- thereby increasing the risk of cybersecurity breaches. To reduce the risk of cybersecurity breaches and digital identity-based frauds/scams, experts unanimously recommend that enterprises must consciously reduce the number of passwords that employees use. This risk is now higher because Generative AI is helping bad actors to employ voice impersonation as an additional method of social engineering to get past human-supported authentication processes (e.g., call centres).
It is in this context that Multi Factor Authentication (MFA) techniques are using criteria that go beyond “knowledge” (e.g., password, OTP, security questions, security grid etc.). MFA approaches increasingly use criteria such as possession, inherence, location, behavior etc. Such “passwordless authentication” methodologies are gaining popularity because they inherently offer a higher level of cybersecurity. Passwordless authentication can be used for physical laptops or desktops, servers, virtual machines, remote logins, websites, mobile apps etc. It can also secure applications that are accessed via VPNs.
How does passwordless authentication work?
access based on “factors” such as biometrics (fingerprint, facial recognition), or keys/tokens dynamically generated by hardware that is provided to users. The underlying principle is to match a private key generated at the user end by the device or other hardware with a public key that is generated/stored on the authenticating enterprise server.
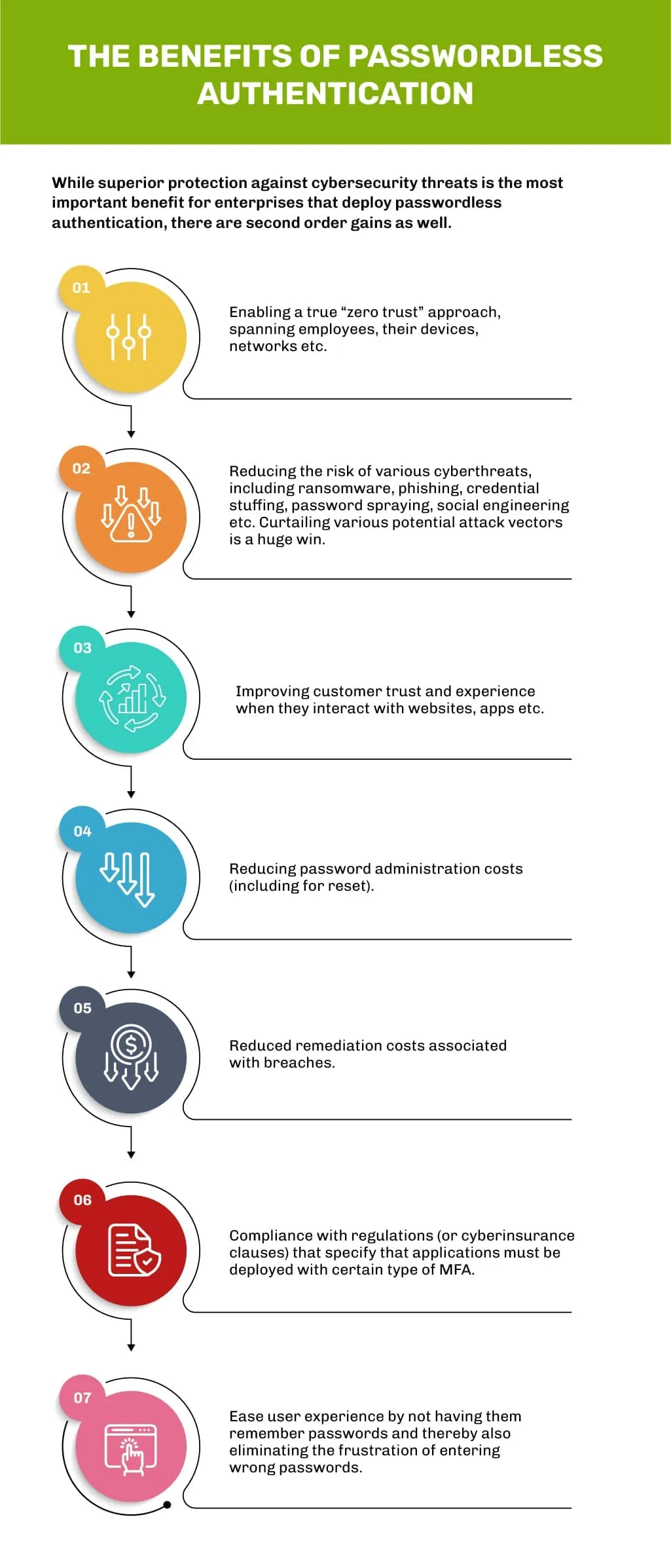
It is important to note that some solutions offer users “passwordless experience”. This does not mean that the underlying solution is truly “passwordless”- all that it may do is to continue to save passwords in the device, but eliminate the need for the user to actually type the password into the app, relying instead on device data. Such solutions cannot offer the entire gamut of benefits that a true passwordless authentication solution can.
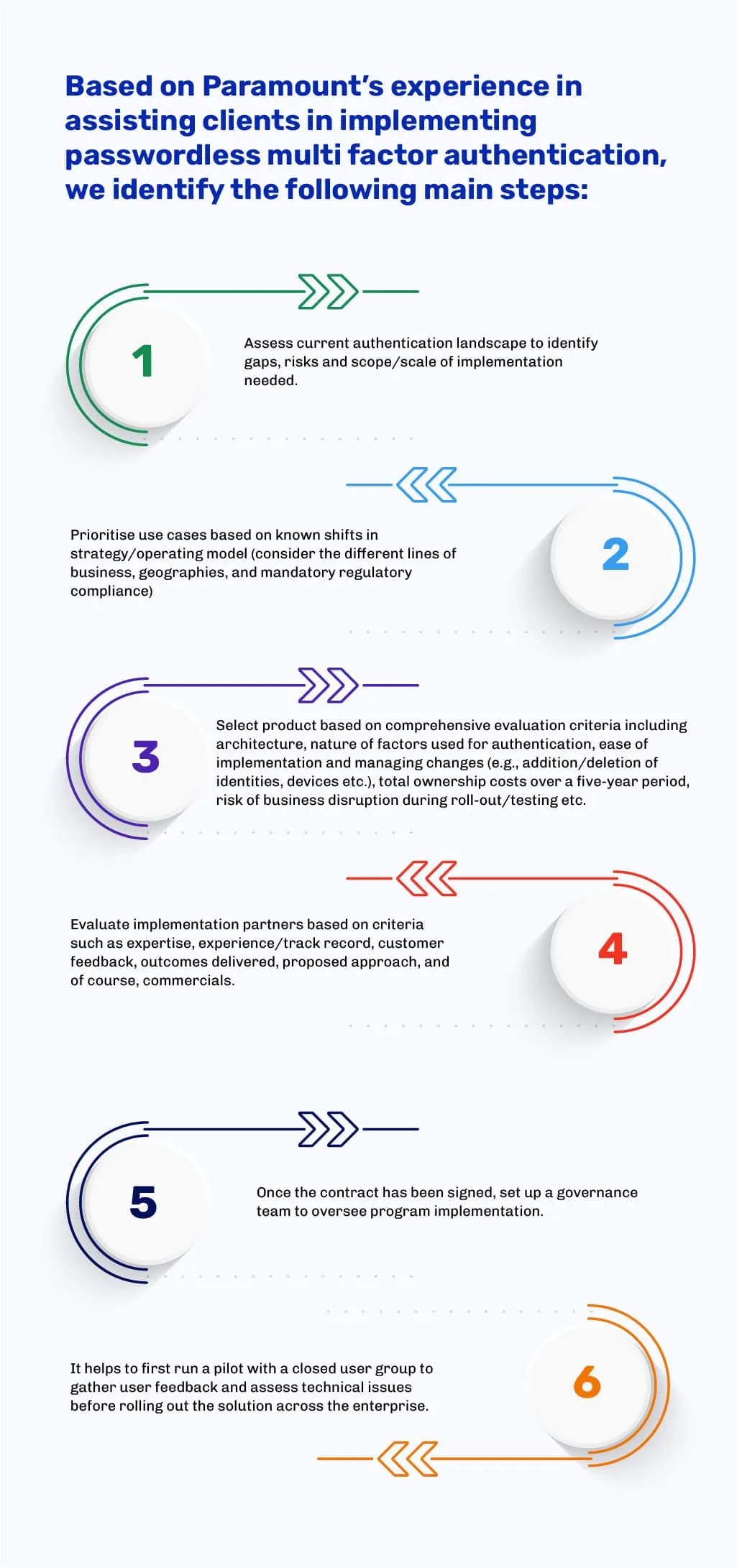
The roadmap to implementing true passwordless authentication
In order that your enterprise optimizes the benefits of passwordless authentication, you need to take it up as a well-defined project that includes properly documented objectives and specific use cases, scope of work, and business case (expected benefits and investments). You then also need to constitute a program team to oversee vendor/product selection, road mapping and planning and project management.
ABOUT AUTHOR
Recent Posts
- How to Choose the Best Authentication Method for Your Business in 2025
- History of DNS Abuse Attack Vector & Countermeasure
- A Step-by-Step Guide to Choosing the Right MSS Provider in the Middle East
- Think You’re Safe? Your Cybersecurity Assessment Might Say Otherwise.
- Rockwell Automation is rocked by serious Vulnerabilities: A Comprehensive Approach to Securing Industrial Control Systems

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.


