Blog
The Most Critical Cyber Threats Middle East Businesses Face

The cyber threats in the Middle East are growing at an alarming rate. With rapid digitalization, cloud adoption, and an evolving geopolitical climate, businesses in the region are increasingly becoming prime targets for cybercriminals.
A recent report by IBM Security revealed that the average cost of a data breach in the Middle East was $7.46 million in 2023, significantly higher than the global average of $4.45 million. This highlights the urgency for organizations to strengthen their cybersecurity defenses.
Cybercriminals today are not only stealing sensitive data but also crippling operations, demanding ransom payments, and exploiting third-party vendors to gain access. The financial and reputational damage caused by these breaches can be catastrophic. This article will explore the Middle East cybersecurity risks and the top cyber threats for businesses, along with strategies to mitigate them.
1. Ransomware Attacks
Ransomware is a type of malware that encrypts an organization’s files, making them inaccessible until a ransom is paid to the attacker. In many cases, businesses must decide between paying the ransom (which does not guarantee file recovery) or losing critical data.
Why is the Middle East a Target?
The ransomware attacks in the Middle East have been rising due to multiple factors:
- The region’s reliance on critical industries like oil and gas, healthcare, and financial services makes it a lucrative target.
- Geopolitical tensions that lead to cyberwarfare tactics.
- Increasing adoption of digital systems and cloud technologies, which expand the attack surface.
The Financial Impact
The report by Chainalysis highlights that ransomware payments exceeded $1 billion globally in 2024, and a significant portion was linked to attacks in the Middle East. The cost of ransomware isn’t limited to the ransom itself—it includes downtime, reputational damage, and regulatory penalties.
Notable Ransomware Variants in the Region
Several ransomware families are responsible for high-profile attacks in the Middle East:
LockBit – A highly efficient ransomware-as-a-service (RaaS) group.
Conti – Known for targeting large enterprises.
Clop – Specializes in stealing and publishing sensitive data if ransom demands aren’t met.
How to Prevent Ransomware Attacks
Preventive measures focus on early detection, limiting exposure, and ensuring recoverability:
Endpoint Detection and Response (EDR): Monitors suspicious activity and blocks threats before they execute.
Regular Backups: Keeping secure, offline backups ensures business continuity even if data is encrypted.
Employee Training: Phishing remains the most common delivery method for ransomware, making staff awareness crucial.
2. Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are highly sophisticated cyberattacks that aim to infiltrate a system and maintain unauthorized access for long periods. Unlike typical cybercriminals who aim for quick financial gains, APT attackers often engage in long-term espionage, data theft, and system disruption. These threats are often state-sponsored or linked to well-funded cybercriminal groups.
Why the Middle East Is a Major Target
The Middle East cybersecurity risks have escalated due to the region’s strategic geopolitical importance and its reliance on industries such as:
- Government agencies – Targeted for political and intelligence-gathering purposes.
- Financial institutions – Attackers seek financial data and customer records.
- Energy sector (Oil & Gas) – A primary target due to its economic significance.
Notable APT Groups in the Middle East
Several well-known APT groups have been actively targeting Middle Eastern organizations:
- APT33 (Elfin Group) – Allegedly linked to Iran, this group has targeted aerospace, energy, and defense sectors.
- APT34 (OilRig) – Focuses on cyber espionage against financial and government institutions.
- MuddyWater – Engages in prolonged cyber infiltration, using malware to spy on targets.
These groups use techniques such as:
- Spear Phishing – Crafting targeted, deceptive emails to steal credentials.
- Zero-Day Exploits – Using previously unknown software vulnerabilities to gain entry.
- Custom Malware – Deploying advanced malicious programs tailored to specific targets.
Defense Strategies Against APTs
Businesses can mitigate APTs in the Middle East through the following measures:
- Network Segmentation – Dividing IT networks into secure zones to prevent attackers from moving laterally.
- Threat Intelligence – Continuously monitoring and analyzing emerging cyber threats to stay ahead of attackers.
- Zero Trust Security Model – Ensuring strict verification for every user and device before granting access.
3. Cloud Security Vulnerabilities
The rapid shift to cloud computing has revolutionized business operations, offering flexibility, scalability, and cost efficiency. However, with this transformation comes an increase in cloud security vulnerabilities, making organizations in the Middle East susceptible to cyberattacks.
According to Gartner, 99% of cloud security failures by 2025 will be the customer’s responsibility, primarily due to misconfigurations and weak access controls. This is particularly concerning for Middle Eastern enterprises that are aggressively adopting cloud technologies.
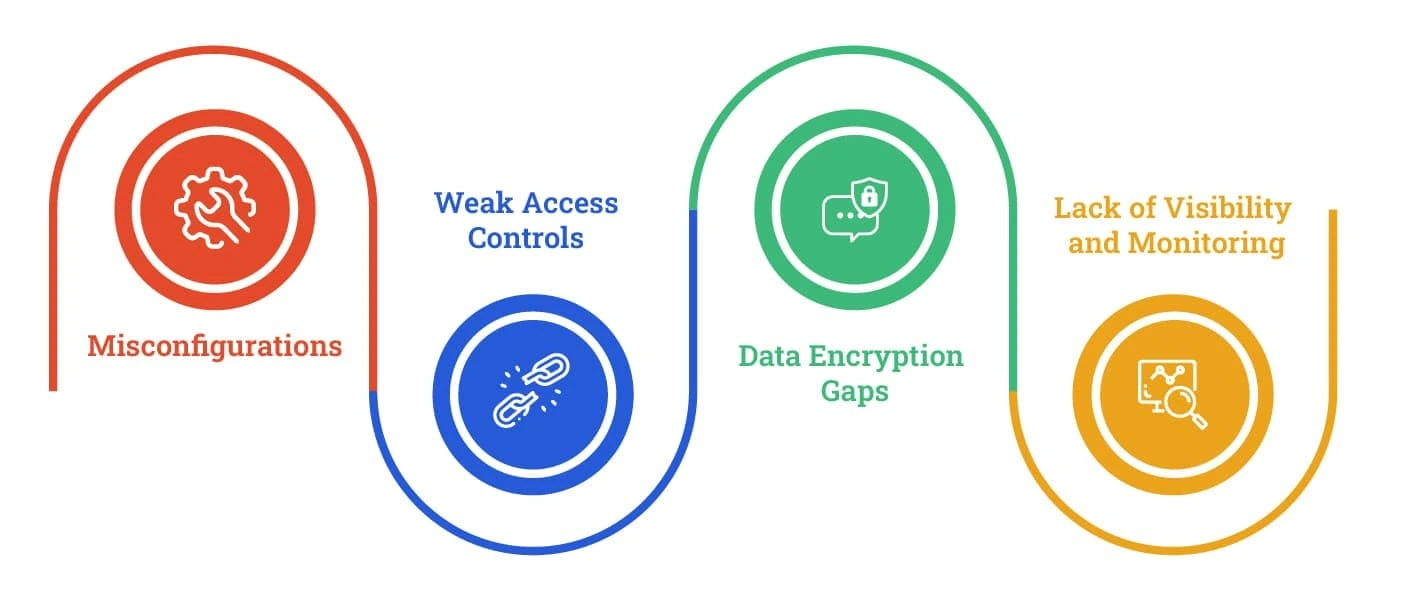
Common Cloud Security Vulnerabilities
- Misconfigurations – One of the most common cloud security risks, misconfigured databases, storage systems, and access settings can expose sensitive information. A 2023 study by Palo Alto Networks revealed that 65% of cloud breaches were due to misconfigurations.
- Weak Access Controls – Without proper Identity and Access Management (IAM), unauthorized users can gain access to critical business data. The absence of Multi-Factor Authentication (MFA) increases the likelihood of credential theft.
- Data Encryption Gaps – Some businesses fail to encrypt their data properly, leaving it vulnerable to breaches. Unencrypted data in transit or at rest can be intercepted by malicious actors.
- Lack of Visibility and Monitoring – Organizations that do not have a Cloud Security Posture Management (CSPM) tool struggle to detect suspicious activities within their cloud environments.
Regulatory Compliance Challenges in the Middle East
As cyber threats increase, governments in the region are imposing stricter regulations to ensure data protection.
- Saudi Arabia’s National Cybersecurity Authority (NCA) has set clear cloud security requirements, requiring businesses to meet specific security controls.
- The UAE’s Cybersecurity Framework mandates cloud providers and enterprises to implement stringent security measures.
Non-compliance with these frameworks can result in hefty fines and reputational damage.
Solutions to Strengthen Cloud Security
To combat cloud security vulnerabilities, businesses should implement the following security measures:
- Multi-Factor Authentication (MFA): Enhances access security by requiring additional authentication beyond just a password.
- Identity Governance and Administration (IGA): Ensures that only authorized personnel can access specific cloud resources.
- Cloud Security Posture Management (CSPM): Continuously scans cloud environments for misconfigurations and compliance issues.
4. Insider Threats
Insider threats occur when employees, contractors, or business partners misuse their access to an organization’s systems, either maliciously or negligently. Unlike external cyberattacks, insider threats originate from within the organization, making them harder to detect and mitigate.
Why Are Insider Threats a Growing Concern?
The rise of remote work, cloud adoption, and digital transformation has increased the attack surface for businesses. According to the Ponemon Institute, insider threats have increased by 44% in the last two years, costing businesses an average of $15.38 million per incident.
There are three main types of insider threats:
- Malicious insiders – Employees or partners who deliberately steal, leak, or sabotage data for personal or financial gain.
- Negligent insiders – Employees who unintentionally expose data due to careless behavior, such as weak passwords or falling for phishing attacks.
- Compromised insiders – Employees whose credentials have been stolen by hackers and used for unauthorized access.

How Insider Threats Impact Middle East Businesses
- Data Leaks: Sensitive company data, such as intellectual property or financial records, can be sold on the dark web.
- Financial Losses: Insider attacks can result in regulatory fines, legal battles, and revenue loss.
- Reputation Damage: Customers and stakeholders lose trust when insider attacks expose confidential data.
How to Mitigate Insider Threats
To reduce insider threats in cybersecurity, businesses should implement the following strategies:
1. Data Loss Prevention (DLP):
- Monitors data transfers and prevents unauthorized access.
- Detects unusual file-sharing activity and restricts sensitive information from leaving the organization.
2. User Activity Monitoring:
- Tracks employee behavior to detect suspicious actions, such as accessing files outside of work hours.
- Uses AI-powered analytics to identify anomalies in user behavior.
3. Strict Access Controls:
- Implements a least privilege policy, ensuring employees only have access to data relevant to their role.
- Uses multi-factor authentication (MFA) to prevent unauthorized logins.
5. Supply Chain Attacks
A supply chain cyber attack occurs when hackers exploit vulnerabilities in a company’s third-party vendors, service providers, or software suppliers to gain access to its systems. Instead of directly attacking a well-secured enterprise, cybercriminals compromise less-protected suppliers, using them as entry points to infiltrate the primary target.
Why Are Supply Chain Attacks a Major Threat?
Many businesses heavily rely on third-party providers for software, IT services, cloud storage, and logistics. Attackers take advantage of this interconnectivity to spread malware, steal sensitive data, or disrupt operations.
- A 2023 study by Symantec found that 62% of global cyberattacks involved third-party suppliers.
- A PwC survey reported that 56% of Middle East businesses experienced a cyber incident linked to a vendor.
- Given the region’s focus on oil & gas, banking, and smart city projects, hackers target software updates, hardware supply chains, and IT management systems to breach organizations.
Notable Supply Chain Attacks Affecting the Middle East
- SolarWinds Breach (2020): This attack compromised government agencies, corporations, and cybersecurity firms worldwide, including organizations in the Middle East. Hackers inserted malicious code into a trusted software update, granting them remote access to thousands of networks.
- Kaseya Ransomware Attack (2021): Cybercriminals exploited IT management software to deploy ransomware across hundreds of companies globally, impacting businesses in the Middle East.
- Nobelium & APT34 Attacks: State-backed hackers have repeatedly targeted regional supply chains, particularly in finance and energy sectors, using compromised cloud providers and IT contractors.
How Attackers Exploit Supply Chains
- Compromising software updates: Injecting malicious code into legitimate software updates.
- Hijacking third-party credentials: Stealing employee credentials from vendors to gain unauthorized access.
- Exploiting weak security policies: Targeting smaller suppliers with inadequate cybersecurity measures.
How to Secure Supply Chains Against Cyber Attacks
Businesses must take a proactive approach to securing their supply chains by implementing strict security policies and continuous monitoring.
Key Security Strategies:
1.Vendor Risk Assessments:
- Evaluate third-party security measures before onboarding new suppliers.
- Conduct regular security audits on vendors to ensure compliance.
- Require vendors to follow Middle East cybersecurity regulations like Saudi Arabia’s NCA framework.
2.Zero Trust Principles:
- Never automatically trust any vendor or third-party access.
- Require multi-factor authentication (MFA) for all external users.
- Limit third-party access to only necessary systems.
3.Continuous Monitoring:
- Implement real-time threat intelligence to detect suspicious activity in vendor networks.
- Use endpoint detection and response (EDR) to spot malicious behavior.
- Automate security patching to prevent software supply chain compromises.
6. Phishing and Social Engineering Attacks
Phishing attacks on businesses remain one of the most effective methods for cybercriminals to gain unauthorized access. These attacks often involve deceptive emails or messages designed to trick individuals into revealing sensitive information.
Targeted Attacks on Middle Eastern Executives
Spear phishing campaigns targeting executives, known as “whaling,” have increased, aiming to exploit high-level access for substantial gains.
Combating Phishing
To reduce phishing risks:
- Security Awareness Training: Educate employees on identifying and reporting phishing attempts.
- Email Security Solutions: Deploy advanced filters to detect and block malicious emails.
- Single Sign-On (SSO): Simplify authentication processes while maintaining security.
7. IoT and OT Security Risks
The proliferation of Internet of Things (IoT) and Operational Technology (OT) devices in industries like oil & gas and smart cities has introduced new vulnerabilities. These devices often lack robust security features, making them attractive targets.
Vulnerabilities in Critical Sectors
Compromising IoT or OT systems can lead to operational disruptions, safety hazards, and significant financial losses, especially in sectors critical to national infrastructure.
Securing IoT/OT Environments
To enhance security:
- Network Access Control (NAC): Implement NAC solutions to regulate and monitor devices connecting to the network, ensuring only authorized IoT and OT devices gain access.
- Endpoint Security: Deploy robust endpoint protection to detect and mitigate threats targeting IoT and OT devices.
- Segmentation Strategies: Divide networks into segments to contain potential breaches and limit attackers’ lateral movement.
8. Regulatory and Compliance Risks
Governments are strengthening cybersecurity regulations in the Middle East to protect businesses and critical infrastructure. Compliance with regulations such as Saudi Arabia’s NCA framework and the UAE’s cybersecurity framework is essential for avoiding fines and protecting sensitive data.
Challenges in Achieving Compliance
Organizations often struggle with:
- Complexity of Regulations: The presence of multiple frameworks across the region can lead to confusion and difficulty in ensuring compliance.
- Resource Allocation: Implementing and maintaining compliance programs require significant investment in human, financial, and technical resources.
- Evolving Standards: Keeping up with rapidly changing regulations and ensuring continuous compliance can be daunting.
Importance of Cybersecurity Governance
Establishing robust cybersecurity governance involves:
- Risk Assessment: Regularly identifying and evaluating cybersecurity risks to inform mitigation strategies.
- Policy Development: Creating comprehensive policies that align with regulatory requirements and organizational objectives.
- Continuous Monitoring: Implementing systems to monitor compliance and detect deviations promptly.
How Paramount Helps Businesses Mitigate These Risks
Paramount provides cutting-edge security solutions to help businesses combat enterprise cybersecurity threats. From ransomware protection to cloud security posture management, Paramount ensures organizations remain secure and compliant. Their offerings include:
- Advanced threat intelligence to identify and neutralize cyber threats.
- Zero Trust security frameworks to enhance protection.
- Continuous monitoring and incident response for real-time threat mitigation.
Conclusion
The cybersecurity landscape in the Middle East is fraught with challenges that demand proactive and comprehensive strategies from businesses. Addressing threats such as ransomware attacks, Advanced Persistent Threats (APTs), cloud security vulnerabilities, insider threats, supply chain attacks, phishing, IoT and OT security risks, and regulatory compliance is crucial to safeguard assets and maintain trust. By investing in advanced security solutions, fostering a culture of awareness, and adhering to regional regulations, organizations can navigate these threats effectively and ensure resilience in an increasingly digital world.
Recent Posts
- IT/OT convergence a way forward towards robust OT security system
- Ransomware attack on Chinese bank’s US subsidiary another warning signal
- Rockwell Automation is rocked by serious Vulnerabilities: A Comprehensive Approach to Securing Industrial Control Systems
- Everything You Need to Know About IGA Light
- Maximize Cybersecurity with Existing Cloud Investments | Paramount

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
