Blog
Achieving Zero Trust in the Middle East with Endpoint Privilege Management

Achieving Zero Trust in the Middle East with Endpoint Privilege Management
In today’s digital age, cybersecurity is a top priority for organizations in the Middle East. As cyber threats evolve, adopting a zero-trust security model has become essential. One critical aspect of this approach is Endpoint Privilege Management (EPM), which helps organizations manage and restrict admin rights to minimize security risks.
In this blog, we’ll explore the importance of EPM in the Middle East, the challenges it addresses, and how it enables organizations to enhance security and compliance in today’s fast-paced digital environment.
The Need for Endpoint Privilege Management (EPM) in the Middle East
As Middle Eastern organizations face rising cyber threats, regulatory demands, and evolving technology landscapes, the need for Endpoint Privilege Management (EPM) has never been greater. The region’s rapid digital transformation, particularly in sectors like finance, healthcare, and energy, has made endpoint security a top priority. These industries often serve as high-value targets for attackers aiming to exploit vulnerabilities through mismanaged privileges.
EPM addresses critical challenges by enforcing least privilege policies, reducing attack surfaces, and maintaining compliance with regional cybersecurity mandates, such as those set by the UAE’s NESA and Saudi Arabia’s SAMA guidelines.
The Threat Landscape: Why Endpoint Security is Essential
The threat landscape continues to expand, with 83% of breaches globally being attributed to external attackers. In the Middle East, the risks are amplified by geopolitical tensions and targeted attacks on critical infrastructure.
Key statistics underscore the urgency:
- 49% of companies were affected by malware in 2022, highlighting the vulnerability of endpoints to malicious software.
- 80% of breaches impacted servers, emphasizing the need to secure endpoint privileges effectively.
- The cost of breaches globally has risen to $4.45 million on average, straining organizational budgets and resources.
Endpoint Privilege Management serves as a critical line of defense, addressing vulnerabilities like stolen credentials, insider threats, and ransomware.
Balancing Security and Productivity with EPM
One of the primary concerns for organizations is maintaining a balance between robust security and employee productivity. Removing administrative privileges can appear disruptive; however, well-implemented EPM solutions offer seamless operations without compromising security.
Features like dynamic application control, just-in-time privilege elevation, and trusted application protection allow businesses to:
- Empower users to perform their roles effectively.
- Prevent unauthorized application use.
- Secure endpoints against sophisticated threats.
- Organizations can achieve a fast time-to-value by deploying EPM with pre-configured policy templates, minimizing the need for extensive manual adjustments.
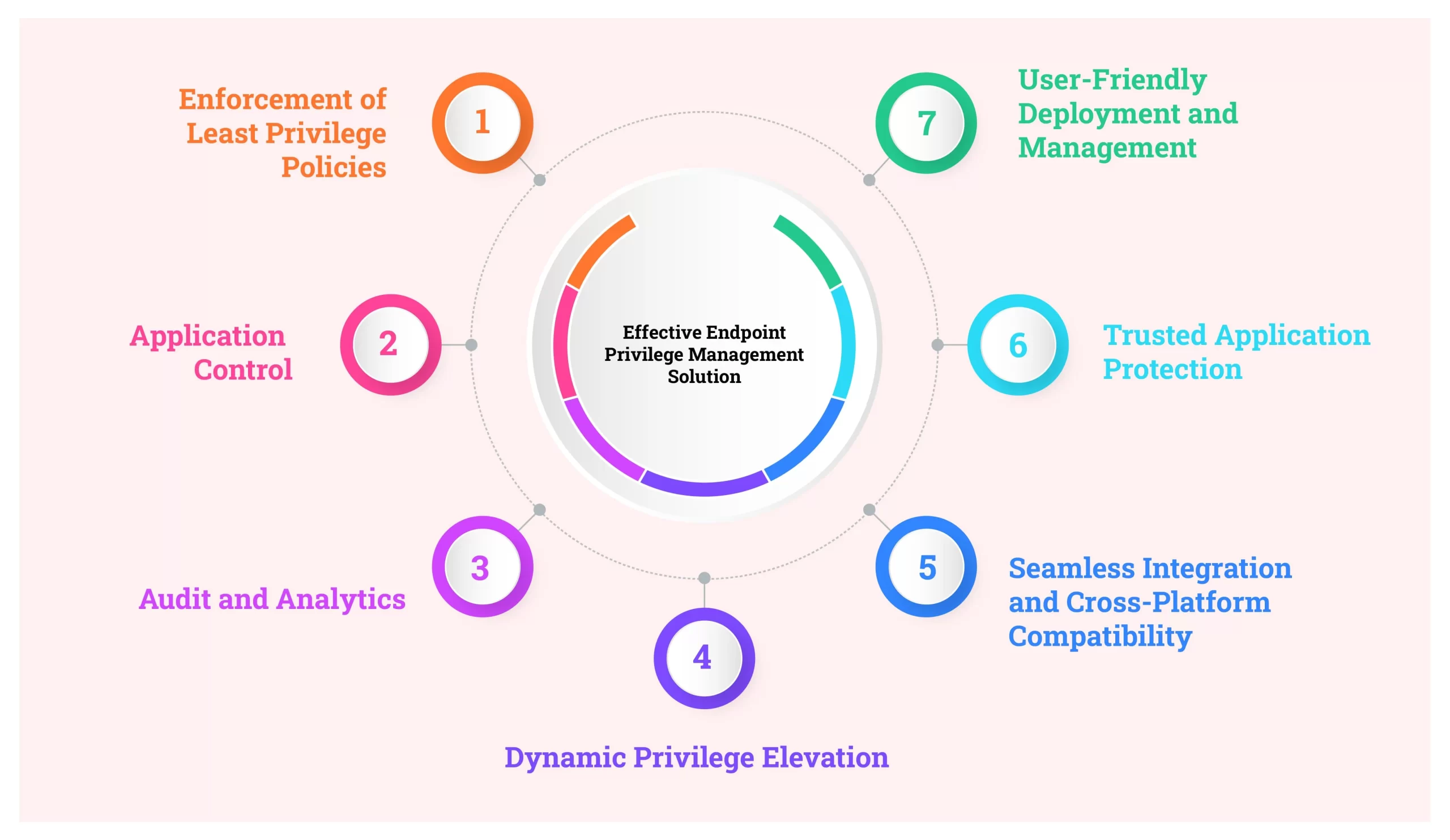
Key Components of an Effective Endpoint Privilege Management Solution
Implementing a successful Endpoint Privilege Management (EPM) strategy requires robust features designed to enhance security without disrupting user productivity. The following are the key components of an effective EPM solution:
Enforcement of Least Privilege Policies
- Automatically removes local admin rights from users to reduce the attack surface.
- Ensures privileges are granted dynamically and temporarily, based on the principle of “just enough access, just in time.”
- Supports Zero Trust security by minimizing standing privileges across endpoints.
Application Control
- Implements allow and deny listing to control what users can install or run on their devices.
- Offers granular policies to differentiate between trusted and untrusted applications, ensuring flexibility without compromising security.
- Prevents execution of malicious scripts, unauthorized software, or unapproved tools.
Audit and Analytics
- Provides detailed, immutable logs of all privilege usage for compliance and forensic purposes.
- Delivers actionable insights into user behavior, enabling policy refinement and stronger security postures.
- Simplifies compliance with regulatory requirements by ensuring transparency in privilege management.
Dynamic Privilege Elevation
- Elevates privileges only to specific applications, never the user, ensuring control and accountability.
- Evaluates contextual triggers like time, location, and identity to grant temporary access when necessary.
- Prevents privilege misuse and limits lateral movement within networks.
Seamless Integration and Cross-Platform Compatibility
- Works across diverse environments, including Windows, macOS, Linux, and cloud-based systems.
- Integrates easily with existing security tools like identity management systems, endpoint detection and response (EDR), and compliance platforms.
Trusted Application Protection
- Protects against fileless threats and exploits targeting trusted applications.
- Monitors and controls application behaviors, such as child process spawning and DLL injections.
User-Friendly Deployment and Management
- Offers out-of-the-box QuickStart templates, reducing the time required for deployment.
- Provides intuitive interfaces for administrators to create, refine, and enforce policies.
- Minimizes the IT service desk workload by maintaining user productivity even after admin rights are removed.
How Paramount Assure Can Help Middle Eastern Organizations with EPM
Paramount Assure specializes in providing cybersecurity solutions tailored to the Middle Eastern market. Their EPM solutions offer:
- Rapid Deployment: With QuickStart policy templates, organizations can enforce least privilege in days, ensuring minimal downtime.
- Comprehensive Protection: Features like trusted application protection and dynamic application control defend against ransomware and fileless malware.
- Seamless Integration: Compatibility with Windows, macOS, and Linux environments ensures coverage across diverse IT ecosystems.
Paramount Assure also offers localized support, ensuring compliance with regional regulations and industry standards.
Conclusion
As Middle Eastern organizations continue their digital transformation, robust endpoint security solutions are paramount. Endpoint Privilege Management (EPM) provides a critical layer of defense by enforcing least privilege policies, reducing attack surfaces, and aligning with Zero-Trust principles.
Solutions like those from Paramount Assure offer a fast and effective way to implement EPM, providing comprehensive protection and operational efficiency. With the right tools and strategies, organizations in the Middle East can achieve a resilient cybersecurity posture, ensuring they are prepared to meet today’s and tomorrow’s challenges.

Case Study
A financial services organization in the GCC faced significant challenges due to unmanaged admin rights and non-compliant applications. After implementing EPM:
- Privileged users were reduced by 98%, from 18,000 to fewer than 400.
- Audit compliance was streamlined, addressing regular regulatory audits.
- Enhanced software control reduced risks associated with unauthorized installations.
- The result was a secure, compliant environment with improved operational efficiency.

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
