A successful migration is not one large move. It’s a phased execution with defined checkpoints, risk controls, and compliance overlays-especially in regulated Middle Eastern environments.
Here’s a five-phase roadmap tailored to cloud migration for Middle Eastern enterprises:
Phase-1 : Discovery and Assessment
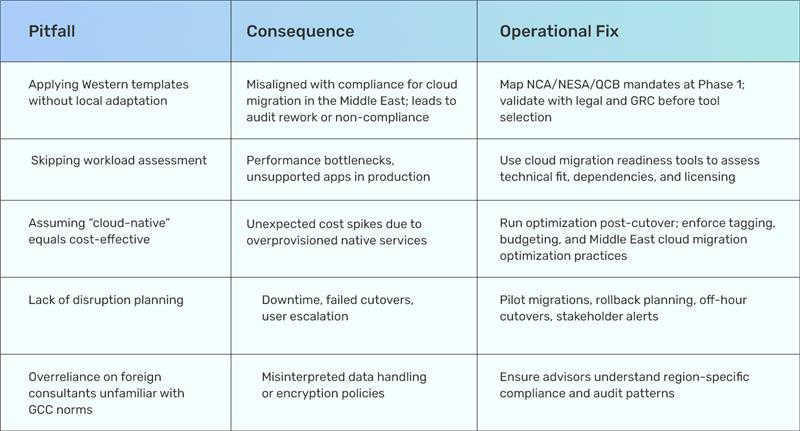
Begin by identifying what applications exist, their interdependencies, and readiness for the cloud. This is where most teams underestimate the complexity. Legacy systems with hardcoded IPs, unsupported OS versions, or outdated auth protocols routinely derail schedules.
Use cloud migration readiness tools like Azure Migrate, AWS Migration Evaluator, or Turbonomic to automate discovery and generate dependency maps.
Don’t move forward without validating:
- Application dependencies and shared infrastructure
- Data classification and compliance for cloud migration in the
Middle East
- Licensing and vendor restrictions
Phase-2: Strategy and Planning
This is where architectural decisions lock in downstream risk. Define which workloads will be rehosted, refactored, or replaced based on the 6Rs. Establish your landing zone-this includes network architecture, IAM policies, encryption controls, and logging standards.
Key planning requirements include:
- Selecting a compliant cloud model and in-region availability zones
- Establishing rollback paths and cutover windows
- Mapping business priorities against technical readiness
Phase-3:Landing Zone and Control Implementation
Before migrating any data, implement your cloud security posture. Regional regulatory mandates require you to configure
- In-region storage zones
- Encrypted backups and key management
- Identity federation and least-privilege access models
This phase also includes policy enforcement-define logging, cost monitoring, and guardrails for workload segmentation. Failure here often leads to failed audits and retroactive remediation.
Phase-4: Migration Execution
Workloads should move in controlled waves, not all at once. Start with dev/test systems or low-risk environments to validate tool performance and team coordination.
Use practices such as:
- Pilot migrations for tool validation
- Blue-green or parallel cutovers for critical workloads
- Stakeholder alerts and helpdesk readiness before each move
Each cutover must be followed by a validation checklist: Did the application come online? Were security controls carried over? Did performance baselines hold?
Migration tools such as CloudEndure, AWS Application Migration Service, and Carbonite can accelerate this phase while reducing risk.
Phase-5: Stabilization and Optimization
Cutover is not the end. This is where most cloud migration Middle East efforts succeed or unravel.
Key activities post-migration:
- Validate encryption and IAM policies
- Check tag hygiene and cost thresholds
- Tune workloads for performance and scaling
- Align optimization with Middle East cloud migration optimization best practices
This is also the time to schedule compliance audits and finalize documentation for regulators.