How to be ready for cloud compliance audits Middle East
How to be ready for cloud compliance audits Middle East
Tak to usIntroduction
Your cloud workloads pass every uptime test, but will they survive a regulator’s inspection
Across the Middle East, regulators aren’t waiting for breaches to occur. They’re conducting routine checks, demanding evidence, and enforcing penalties even when enterprises show the “intent to comply”. With cloud compliance audits in the Middle East becoming a recurring reality. most enterprises discover too late that passing a security test doesn’t mean passing an audit.
Increased cloud adoption by banks, telcos, and public-sector entities has triggered a parallel wave of legal scrutiny. New data protection laws, such as the cloud compliance regulations like the Saudi PDPL and UAE DIFC DP Law are reshaping the way compliance is enforced. But the audit doesn’t begin with a request for documentation. It begins with the assumptions made during architecture planning.
In this blog, we will examine what determines audit success in a cloud-first, regulation-heavy environment and where even mature teams typically fall short.
Pre-audit preparation for audit success
Most cloud compliance audits in the Middle East don’t fail because of misconfigured tools. They fail because no one can prove what’s already in place. Evidence gaps, unclear ownership, and undocumented assumptions are what get regularly flagged.
To avoid scrambling during an audit window, preparation must begin at the architecture and policy level:
Identify your applicable regulatory frameworks early
For enterprises in the Middle East, compliance isn’t one standard but a layered set of obligations. Cloud compliance regulations like Saudi PDPL, UAE DIFC DP Law, central bank mandates, and ISO or PCI requirements often apply in parallel.
Begin audit preparations by mapping which laws govern which parts of your environment. Otherwise, you’ll end up applying controls that don’t satisfy the right stakeholders, or worse, missing the mandatory ones entirely.
Map existing controls against legal expectations
Don’t assume encryption, access policies, or backups meet compliance just because they exist. Review whether encryption keys are managed inside the right jurisdiction, whether IAM policies reflect actual user roles, and if log retention aligns with each standard. This is where most internal teams rely too heavily on cloud provider defaults only to find later that regional requirements override those defaults.
Centralize documentation-and version it
Every security policy, data flow diagram, audit trail, and incident log must be easily retrievable, version-controlled, and current. Screenshots. architecture diagrams, even DFDs, auditors will not chase them down. If documentation is spread across shared drives or owned by individual teams, it’s as good as missing.
Run internal pre-audits with real data flows
Simulate an external audit using actual production flows and control enforcement. Validate whether logs are retained as per mandate. whether alerts fire on misconfigurations, and if classification is consistently applied.
Use this dry run to eliminate easily avoidable gaps, especially the ones around SaaS connectors and unmanaged admin accounts, as they often fall outside the standard coverage.
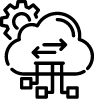
Assign clear ownership through a RACI model
Compliance is not an IT function. In well-run programs, audit readiness is jointly owned by GRC, Risk, Security, and Cloud Ops teams. Without a formal RACI matrix, control handoffs break down, tickets stall, and no one takes accountability for remediating flagged issues.
Define and track your cloud perimeter
It’s not enough to document which environments are in scope. You need tooling, such as SIEMS, CSPM platforms, or native inventory trackers to confirm that unsanctioned services or shadow workloads aren’t quietly expanding your footprint. If auditors uncover services not declared in your audit scope, your exposure doubles overnight.
Audit success in this region depends less on your cloud stack and more on your ability to prove who owns what, where data lives, and how controls are enforced. Without that baseline, even technically sound environments fail to demonstrate cloud security compliance Middle East regulators require.
Assign clear ownership through a RACI model
Compliance is not an IT function. In well-run programs, audit readiness is jointly owned by GRC, Risk, Security, and Cloud Ops teams. Without a formal RACI matrix, control handoffs break down, tickets stall, and no one takes accountability for remediating flagged issues.
How to Achieve Most Effective Audit Execution
A cloud compliance audit doesn't test your intent. It tests what's actually enforced. Auditors aren't interested in slide decks or plans; they want evidence that the controls in place are operational, traceable, and aligned to law. In regulated Middle Eastern environments, this validation process is both technical and procedural.
Access and identity management
Auditors will request admin login records, IAM policies, and proof of access reviews. If user permissions haven’t been audited recently-or if roles are still scoped to departments instead of functions-expect a finding. Temporary privileges with no expiry, shared credentials, or overly broad groups like “All Staff” are treated as red flags, regardless of intent.
Incident and breach history
Even if no breach has occurred, you’ll be asked to show logs of incident response readiness. This includes playbooks, notification procedures, and any DR drills conducted. Under laws like PDPL and DIFC DP Law. breach response is time-bound, so missing this can escalate a minor issue into a regulatory violation.

Security and privacy policies
Security and privacy policies: Every policy, including acceptable use, classification, encryption, data retention, etc., must be versioned, enforced, and aligned to data protection laws in the Middle East. Auditors will cross-reference policies with actual system behavior. For example, if your policy mandates in-country backups, they’ll verify whether snapshots, logs, and telemetry data actually reside in approved regions.
Architecture diagrams and data flow visuals
Regulators in the Middle East emphasize cloud data residency laws. That means auditors will review diagrams showing where data moves, which regions it touches, and which services process it. If workloads cross borders, even indirectly, you’ll need to justify it with user consent records and processor agreements. Informal SLA clauses won’t suffice.

Third-party validation
You’re responsible for proving that every external system, e.g., SaaS tools, managed service providers, and integrated APIs complies with the same standards that you do. This includes collecting vendor contracts. certifications, audit reports, and occasionally. conducting your own third-party assessments.

Evidence artefacts, not statements
Everything mentioned above must be backed by proof: screenshots of access control settings, encryption status pages, control-plane logs, data tagging views. configuration reports. Text descriptions aren’t enough. If you can’t show it, it doesn’t count.
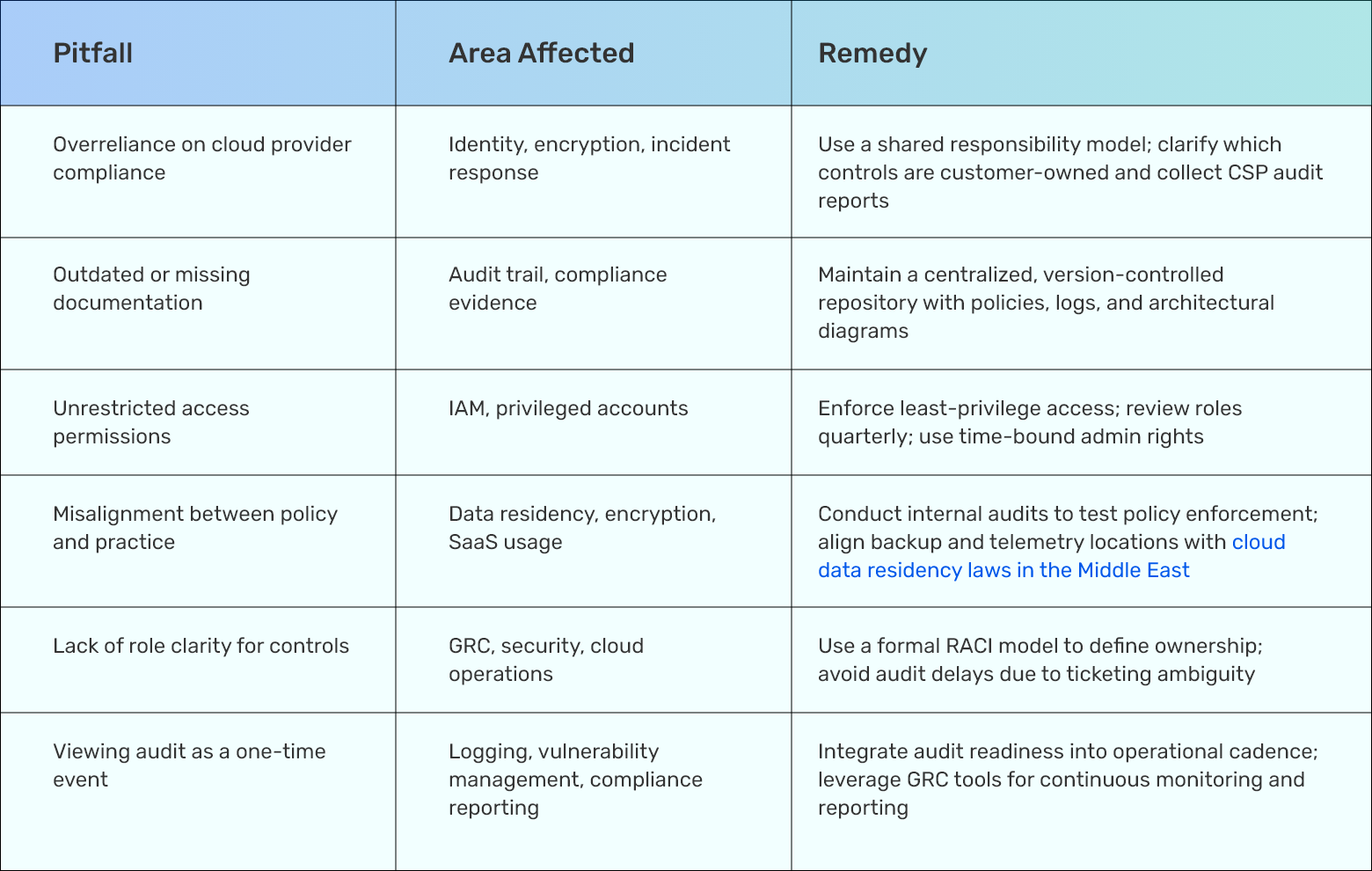
Common Failure Patterns During Audits
Audit failures are surprisingly predictable. Most errors occur because teams either misplace trust in cloud vendor defaults, skip internal enforcement, or assume documentation exists when it doesn’t. In regulated Middle Eastern markets, these gaps will directly trigger findings under cloud security audits in the Middle East.
Here are some recurring pitfalls, the areas they compromise, and what can be done to address them:
Build Audit-Ready Cloud Environments with Paramount
In the Middle East, where data protection laws impose strict expectations on cloud operations, audit readiness must be embedded across architecture, identity, policy, and enforcement. And it should be done long before regulators ask for proof.
Paramount helps enterprises across the Middle East convert fragmented compliance practices into enforceable, audit-ready systems. Whether you’re navigating cloud compliance regulations or sector-specific mandates, we align your cloud controls with real-world audit expectations.
From access governance and classification enforcement to evidence collection and documentation frameworks. Paramount ensures your environment can meet the demands of cloud compliance audits in the Middle East before the questions are even asked.
