Fixing classification doesn’t start with labels. It starts with context.
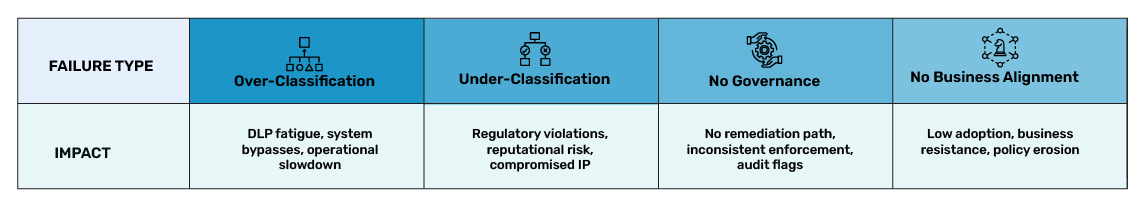
When data is classified in isolation, every enforcement mechanism downstream becomes unreliable. DLP alerts become noise. Cloud protections are misaligned. And regulatory audits become defensive exercises.
Here’s how to rebuild classification from the ground up, anchored in the business, not the tooling.
Phase 1: Engage the business early
Most classification models fail because they’re built in IT conference rooms and then enforced on people who were never consulted.
Start with a structured workshop involving risk, IT, legal, and departmental leaders. Your task is to identify:
- What kinds of data are being created and handled daily
- Where that data moves (e.g. between systems, across regions)
- What teams believe is “sensitive,” and why.
These conversations are often the first time the business realises that classification isn’t just about security, it’s about enabling safe. compliant productivity.
Phase 2: Build a fit-for-purpose framework
A classification model should be as simple as it is enforceable. Most enterprises don’t need seven tiers. In GCC markets, a three- or four-tier model often provides the best balance of precision and usability:
- Public – No restrictions, approved for external distribution
- Internal – For internal use only, low sensitivity
- Confidential – Business-sensitive; misuse can impact operations or brand
- Restricted / Regulated – Subject to legal, regulatory, or contractual obligations
Tiers should map directly to enforcement logic in your data loss prevention strategy, access control policies, and cloud computing security services.
Phase 3: Map data to business processes
Classification isn’t about documents. It’s about workflows.
For example:
- An HR document containing salary data may be “Internal” when stored on the intranet, but “Confidential” once sent for external benchmarking.
- Marketing campaign files may be “Internal” pre-launch, and “Public” once cleared for release.
Identify how classification changes across the data lifecycle at rest and in motion. This also helps define what should trigger alerts or block actions
Phase 4: Establish governance and accountability
You can’t secure what no one owns. Classification requires operational governance:
- Data owners must review and validate classifications
- Security teams must define enforcement rules and reporting protocols
- Business leaders must be accountable for misuse within their teams
This structure prevents misclassifications from becoming systemic and enables course correction before audits or breaches expose the gap.
Phase 5: Automate smartly, not hastily
Once context, logic, and ownership are in place, only then should you apply automation. Integrate automation with:
- DLP and CASB systems
- Cloud platform-native controls (e.g., Azure Information Protection)
- SIEM correlation rules
- Role-based access policies
Automating too early locks in the wrong logic at scale. Doing it at the right point ensures that automation enforces intent, not errors.