Blog
Everything You Need to Know About Passwordless Authentication
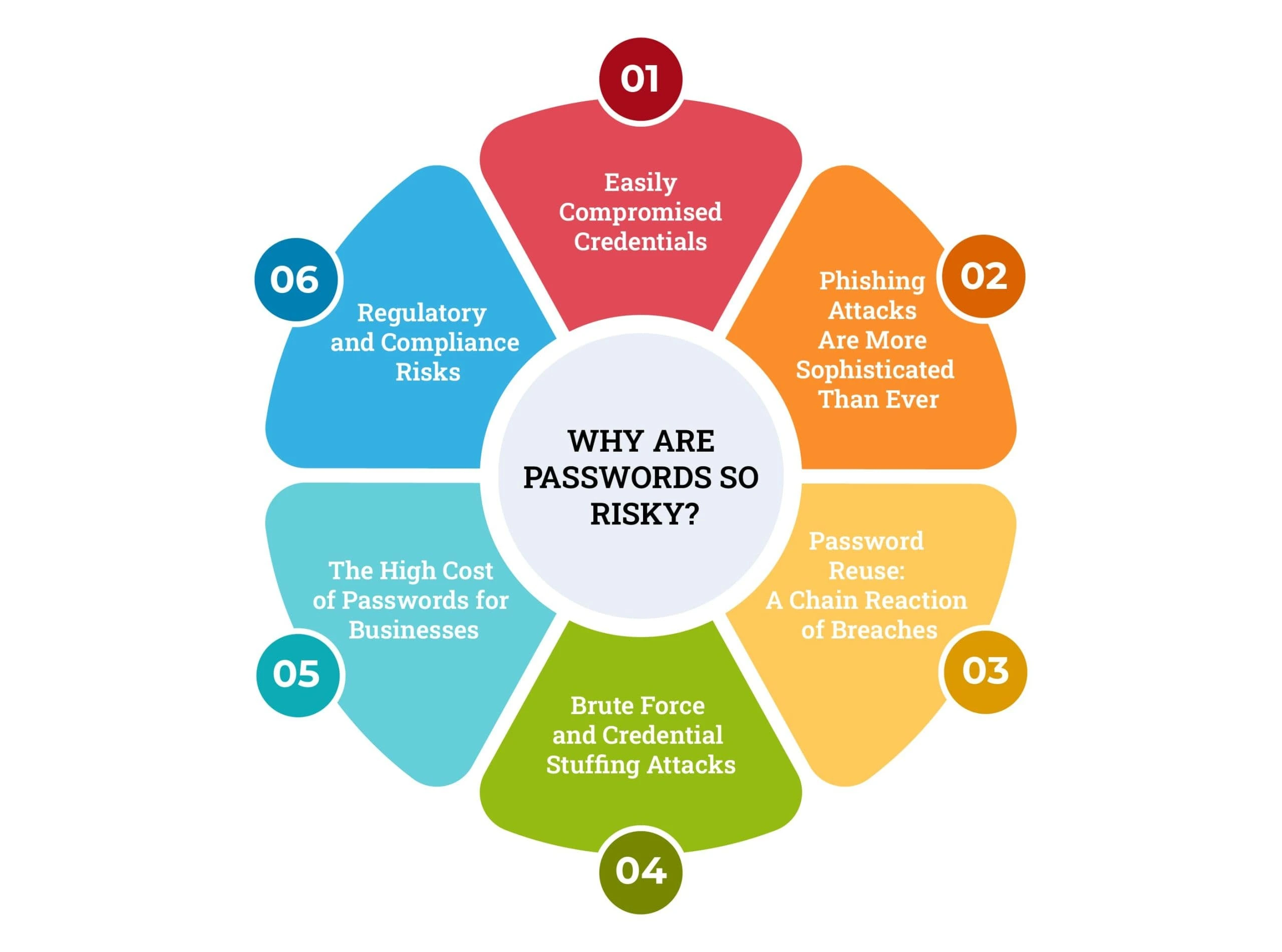
Why Are Passwords So Risky?
Despite their widespread use, passwords are a nightmare for security. Here’s why:
1. Easily Compromised Credentials
Passwords are a prime target for cybercriminals because they are often weak, reused, or easily guessable. According to Verizon’s 2023 Data Breach Investigations Report, 81% of hacking-related breaches are caused by stolen or weak passwords. Attackers use various techniques to steal or break into accounts, such as:
- Brute force attacks – Automated tools generate and test billions of password combinations until they find a match.
- Dictionary attacks – Hackers run through commonly used words and phrases to guess passwords.
- Data breaches – Millions of passwords leak every year due to corporate security failures, making them available for hackers on the dark web.
- Keyloggers and malware – Malicious software can record keystrokes and steal passwords as users type them.
2. Phishing Attacks Are More Sophisticated Than Ever
Phishing remains one of the most effective ways for cybercriminals to steal passwords. Attackers impersonate trusted entities (banks, employers, social media sites) to trick users into entering their login credentials.
- 40% of all cyberattacks in 2022 were phishing-related, according to IBM.
- AI-powered phishing scams are making it harder for users to detect fraudulent emails, texts, or fake login pages.
- Attackers use man-in-the-middle (MITM) attacks to intercept login data in real time, even when two-factor authentication (2FA) is in place.
Even tech-savvy users fall victim to phishing because these attacks are constantly evolving.
3. Password Reuse: A Chain Reaction of Breaches
The average person has over 100 online accounts, and it’s nearly impossible to remember unique passwords for each one. As a result, 65% of people reuse passwords across multiple accounts.
- If a hacker obtains one password from a breached website, they can use it to access multiple services (a technique called credential stuffing).
- In 2023, over 24 billion usernames and passwords were found circulating on the dark web.
- Cybercriminals use automated tools to test stolen credentials against thousands of websites.
Even with strong passwords, reuse creates a major security gap. A single leak can compromise banking, email, and work accounts in one go.
4. Brute Force and Credential Stuffing Attacks
Hackers don’t manually guess passwords—they use automation and AI-driven algorithms to test thousands (or even millions) of combinations per second.
- A 10-character password without special characters can be cracked in less than a day.
- Attackers use rainbow tables (precomputed lists of hashed passwords) to instantly crack weakly encrypted passwords.
- Bot-driven credential stuffing attempts to log in to thousands of accounts simultaneously using breached password databases.
Even if companies enforce strong password policies, these attacks still exploit human tendencies like predictable password structures (e.g., “Summer2024!” or “P@ssw0rd123”).
5. The High Cost of Passwords for Businesses
Beyond security risks, passwords are a financial burden for organizations:
- $5.2 million per year – The average cost businesses incur to handle password-related support requests.
- 50% of IT helpdesk calls are password resets, diverting resources from more critical security tasks.
- Employees spend an average of 11 hours per year just dealing with forgotten passwords, leading to lost productivity.
Security breaches caused by weak passwords cost businesses even more, with damages reaching millions per incident due to data theft, regulatory fines, and reputational damage.
6. Regulatory and Compliance Risks
With stringent regulations like GDPR, CCPA, and PCI DSS, businesses face severe penalties for failing to secure user data. Password-based authentication often falls short of compliance requirements, leading to legal liabilities.
- GDPR violations can result in fines of up to €20 million or 4% of annual global revenue.
- The PCI DSS (which governs payment security) strongly discourages the use of passwords alone for authentication.
What Are the Different Authentication Factors?
Authentication is the process of verifying a user’s identity before granting access to a system, application, or device. Traditional authentication methods primarily rely on passwords, but security experts categorize authentication into three main factors:
1. Something You Know
This refers to information that the user remembers and provides to verify their identity. Examples include:
- Passwords – The most common authentication method, but also the weakest due to reuse, phishing, and brute-force attacks.
- PINs (Personal Identification Numbers) – Short numeric codes used in banking and mobile authentication.
- Security Questions – Personal knowledge-based questions like “What’s your mother’s maiden name?” These are easy to guess or research, making them a weak form of authentication.
Problem: Human memory is unreliable, and users often create weak, reused, or easily guessable credentials, making this method highly insecure.
2. Something You Have
This factor involves a physical device or object that verifies the user’s identity. Examples include:
- Security Keys (e.g., YubiKeys, Titan Keys) – USB or NFC-based devices that generate cryptographic codes for authentication.
- Smartphones & Mobile Apps – Used for generating One-Time Passwords (OTPs) or approving authentication requests.
- Smart Cards & ID Tokens – Chip-based cards used in workplaces and government agencies for secure access.
Advantage: Unlike passwords, these items are not stored in a database, making them resistant to mass credential leaks.
3. Something You Are
This is the most advanced and secure authentication factor, as it relies on unique biological characteristics of the user. Examples include:
- Fingerprint Scanning – Used in mobile devices, laptops, and security doors.
- Facial Recognition – Common in smartphones and surveillance systems.
- Retina or Iris Scanning – Highly secure, but less common due to specialized hardware requirements.
- Voice Recognition – Sometimes used for banking authentication.
Advantage: Biometric traits are extremely difficult to replicate or steal. However, privacy concerns and potential false negatives (e.g., a wet fingerprint not scanning properly) need to be addressed.
What is Passwordless Authentication?
Passwordless authentication is a method of verifying identity without requiring a password or any form of shared secret. Instead, users authenticate using more secure alternatives like biometrics, hardware tokens, or cryptographic key pairs.
Unlike multi-factor authentication (MFA), which often still involves a password plus another factor, true passwordless authentication removes any form of shared secrets entirely, eliminating a major attack vector.
One step further is User nameless Authentication for certain scenarios which is based on FIDO2, involving push notifications with biometrics, QR Codes, FIDO2 security keys or Passkeys.
How Does Passwordless Authentication Work?
The Fast Identity Online (FIDO) guidelines, which are the “gold standard” of genuine passwordless authentication, aim to eliminate shared secrets entirely from the authentication procedure. Both FIDO and the enhanced FIDO2 standards employ public key cryptography to authenticate users and servers.
In reality, a standard passwordless login process looks like this:
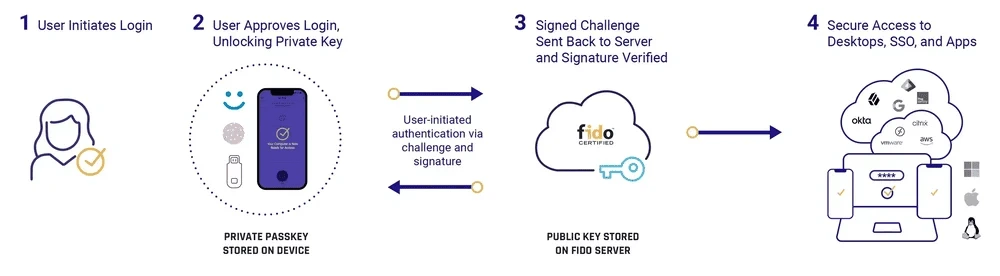
Step 1: The user initiates the login procedure by sending the server an authentication request.
Step 2: The authentication system prompts them to provide the necessary factors.
Step 3: A secure local action on the user’s device will unlock the private key, like presenting a fingerprint or face scan or using a security key.
Step 4: The challenge is signed using the private key to prove user possession.
Step 5: The authenticating server confirms that the public key provided in the signature matches.
Step 6: The user is authenticated for system access after a successful match.
By leveraging individuals unique biometrics, the user securely unlocks a private key stored on their device. This key, through secure cryptographic protocols, validates their identity against the public key, ensuring authentication without the exchange of sensitive information or reliance on central databases.
The Benefits of Passwordless Authentication Solutions
Going passwordless isn’t just a security upgrade—it’s a game-changer for both businesses and users. Eliminating passwords removes one of the biggest attack vectors while improving convenience and reducing costs. Here’s how:
1. Stronger Security: Eliminating the Biggest Weak Link
Passwords are the weakest link in authentication. By replacing them with passwordless methods, organizations significantly reduce the risk of:
- Phishing Attacks – No passwords mean nothing for attackers to steal through phishing emails.
- Credential Stuffing – Since there are no stolen credentials to reuse, hackers can’t exploit password leaks.
- Brute-Force Attacks – Passwordless authentication methods rely on cryptographic keys or biometrics, which can’t be guessed like traditional passwords.
- Man-in-the-Middle (MITM) Attacks – Traditional login credentials can be intercepted; passwordless authentication prevents this by using secure device-based authentication.
2. Frictionless User Experience: No More Forgotten Passwords
We’ve all been there—struggling to remember a password, clicking “Forgot Password,” waiting for a reset email, and going through an annoying process just to log in. Passwordless authentication eliminates this pain.
- Users log in seamlessly using biometrics, security keys, or trusted devices.
- No more frustration of creating complex passwords that meet arbitrary rules like “must include a special character, a capital letter, and be different from your last 10 passwords.”
- Businesses can provide one-click authentication or even background authentication, making logins feel effortless.
3. Huge Cost Savings for IT and Businesses
IT teams spend millions of dollars on password resets and support requests. A passwordless solution drastically cuts these costs.
- Password resets cost businesses an average of $70 per reset.
- Eliminating passwords reduces IT overhead, freeing up resources for more strategic security initiatives.
Case Study: Microsoft reported that switching to passwordless authentication reduced password-related IT support costs by 87%.
4. Compliance and Regulatory Advantages
With strict data protection laws like GDPR, CCPA, HIPAA, and PCI DSS, businesses must ensure secure authentication methods.
- Passwordless authentication helps meet compliance standards by removing shared secrets (passwords) that are prone to leaks.
- Stronger authentication methods like FIDO2, biometrics, and cryptographic keys align with modern regulatory security expectations.
5. Increased Productivity: No More Lockouts
Password-related issues are not just a security risk—they’re time-wasters for employees.
- Employees often lose productivity due to password lockouts and resets.
- With passwordless authentication, workers can instantly access business apps without interruption.
- A smoother login experience improves efficiency, especially in industries where fast and secure access is critical, such as healthcare, finance, and government.
6. Better Protection Against Insider Threats
One often overlooked security risk is insider threats—employees misusing credentials, whether intentionally or accidentally.
- Without passwords, employees can’t share, write down, or sell passwords (a common issue in data breaches).
- IT admins can enforce passwordless authentication across all accounts, reducing security loopholes.
The Challenges with Passwordless Authentication Solutions
Passwordless authentication may provide several difficulties, much like any new technology or big shift. These will differ based on the kind of passwordless solution and the company’s IT and IAM infrastructure.
1. User Adoption
One of the biggest challenges in going passwordless is ensuring that employees and customers are comfortable with the transition. People are accustomed to passwords, and any significant change can lead to resistance.
- Solution: Provide clear communication on the benefits of passwordless authentication, including improved security and ease of use. Offer training sessions, documentation, and hands-on demonstrations to ensure smooth adoption. Gradual rollout strategies, such as enabling passwordless authentication as an option before making it mandatory, can also help ease the transition.
2. Legacy System Integration
Many organizations still rely on legacy systems that were built around password-based authentication. Retrofitting these systems to work with passwordless authentication can be a complex challenge.
- Solution: Look for solutions that support open standards like SAML (Security Assertion Markup Language), OIDC (OpenID Connect), and FIDO2 to enable easier integration. Some vendors offer middleware or API-based solutions that bridge the gap between legacy infrastructure and modern authentication systems. Phased implementation strategies can help organizations transition in stages while minimizing disruption.
3. Offline Access
Some passwordless authentication methods depend on an internet connection, which can pose problems for users who need access in offline environments, such as during travel or in remote locations.
- Solution: Implement decentralized offline PINs or local authentication methods that do not require an internet connection. Hardware security keys and built-in device authenticators like Windows Hello or Apple’s Face ID can enable secure authentication without needing an active network connection.
4. Device Compatibility
Passwordless authentication methods may require specific hardware, such as biometric scanners, security keys, or modern smartphones, which might not be available to all users.
- Solution: Organizations should conduct a thorough assessment of their existing devices and plan for upgrades where necessary. Choosing authentication solutions that support multiple authentication factors—such as biometrics, PINs, and security keys—ensures flexibility across different devices and user needs. Ensuring compatibility with cross-platform authentication methods like FIDO2/WebAuthn can provide a seamless experience across desktops, mobile devices, and web applications.
Passkeys and Passwordless Authentication
The FIDO Alliance created passkeys as a phishing-resistant alternative to passwords. The two main categories are device-bound and synchronized. It is possible to utilize synced passkeys across several devices without having to re-enroll each one. Microsoft, Google, and Apple have been implementing support for synchronized passkeys across their different operating systems since 2022.
Because device-bound passkeys may incorporate features and controls that consumer passkeys cannot, they are typically preferred on an enterprise level. There are vendors in the market who offer FIDO device-bound passkey that can be used for desktop access and connects with the enterprise’s whole technological stack.
Passwordless Security, Passkeys, and Zero Trust
According to the OMB, CISA, and other security frameworks, passwordless phishing-resistant multi-factor authentication is the cornerstone of every Zero Trust security endeavor.
Organizations may implement Zero Trust authentication principles without making the user experience harder by utilizing FIDO device-bound passkey security standards. Assuring that your authentication procedures meet the greatest degree of assurance (NIST 800-63B AAL3) and laying a strong basis for your Zero Trust security architecture it creates the necessary trust in the user’s identity.
Keep in mind that synchronized passkeys do not offer this degree of certainty. Additionally, companies must ensure that they cover all use scenarios, including distributed workforces, remote workers, and frequent travelers.
What To Look For in a Passwordless Solution
Not all passwordless solutions are created equal. Key factors to consider include:
- FIDO2/WebAuthn Support: Ensures compatibility with industry standards and enhances security with public-key cryptography.
- Multi-Device and Cross-Platform Compatibility: A strong solution should work seamlessly across desktops, mobile devices, and cloud applications without forcing users into a single ecosystem.
- Phishing and MFA Fatigue Resistance: The solution must protect against social engineering attacks and prevent attackers from exploiting authentication fatigue.
- User-Friendly and Frictionless Experience: Authentication should be simple, intuitive, and not create additional steps that slow down users.
- Strong Recovery and Backup Options: There should be secure ways to regain access if a device is lost, such as biometric fallback, hardware keys, or cloud-synced passkeys.
- Scalability and Enterprise Integration: The solution should easily integrate with existing IT infrastructure, identity providers, and business applications.
- Compliance and Regulatory Alignment: Ensuring adherence to security standards like GDPR, CCPA, and NIST guidelines is crucial for enterprise adoption.
Conclusion
Passwordless authentication is the future of digital security. With passwords proving to be an outdated, insecure, and costly method of authentication, organizations must adopt modern solutions to protect users and data. Whether through biometrics, security keys, or passkeys, the shift to passwordless authentication isn’t just about convenience—it’s a crucial step toward a safer, more efficient digital world.
Recent Posts
- Let’s root for each other and watch each other grow
- Passwordless authentication: The Open Sesame route to more secure digital enterprises
- Clearing the Air on Cloud Security: Myths, Facts, & Benefits
- IT/OT convergence a way forward towards robust OT security system
- Generative AI adoption risks you should address to safeguard your enterprise

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
