Blog
Everything You Need to Know About IGA Light

Identity Governance and Administration (IGA) is a crucial component of cybersecurity strategies in modern organizations. However, traditional IGA implementations can be complex, time-consuming, and costly, making them impractical for many businesses. This is where “IGA Light” comes into play—a streamlined, data-driven approach that delivers effective identity governance without the overhead of full-scale IGA deployments.
In this blog, we will explore the concept of IGA Light, its benefits, and how to implement it.
What is IGA Light?
IGA Light is a risk-focused Identity and Access Management (IAM) approach that prioritizes security value and threat reduction over complexity. It provides organizations with data-driven identity governance, enabling real-time risk analysis and adaptive access controls to mitigate security threats. By emphasizing rapid deployment and automation, IGA Light ensures continuous monitoring, anomaly detection, and proactive risk mitigation, giving organizations complete visibility and control over user access while reducing their attack surface.
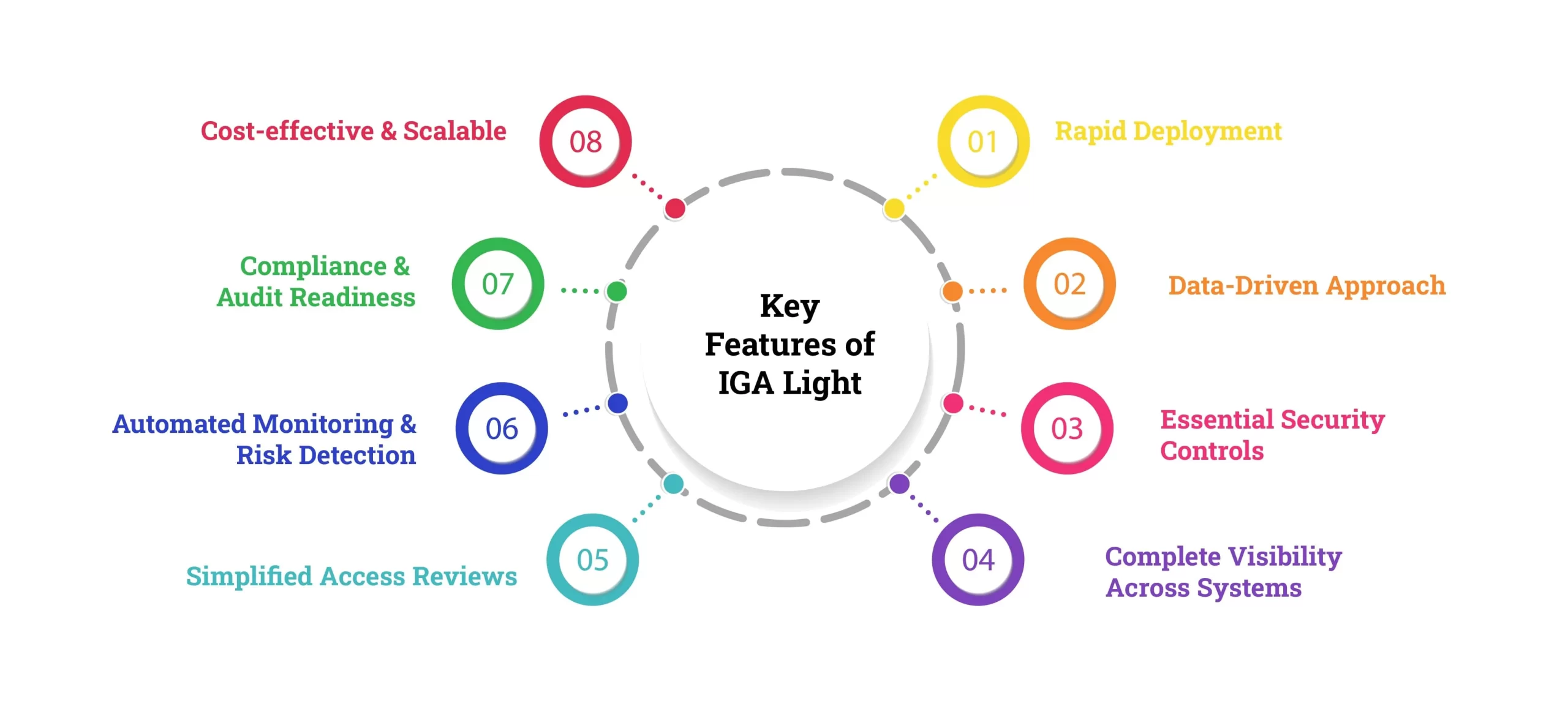
Key Features of IGA Light
Here are the key features of IGA Light that make it an effective and streamlined identity governance solution:
1. Rapid Deployment
Unlike traditional IGA solutions that require months for implementation, IGA Light can be deployed within days or weeks. This ensures quick visibility into access controls and governance without long project timelines.
2. Data-Driven Approach
IGA Light prioritizes identity governance as a data problem rather than a purely process-driven issue. It gathers user access data from critical systems, applies security controls, and highlights potential risks.
3. Essential Security Controls
Rather than offering exhaustive IGA functionalities, IGA Light focuses on core security measures, such as:
- Identifying and removing orphaned accounts (inactive accounts with access).
- Managing privileged access to prevent unauthorized control.
- Reducing access accumulation (excessive permissions over time)
4. Complete Visibility Across Systems
IGA Light provides a centralized view of user access across an organization. This helps security teams and IT administrators track who has access to what and detect any unauthorized access.
5. Simplified Access Reviews
- Traditional access reviews can be time-consuming and complex.
- IGA Light simplifies this by enabling business-friendly access reviews, allowing non-technical users to validate and clean up user access easily.
6. Automated Monitoring & Risk Detection
- Continuous monitoring ensures that access rights are reviewed over time.
- Suspicious or excessive access permissions are flagged for immediate action.
- Helps prevent insider threats by proactively identifying unusual access patterns.
7. Compliance & Audit Readiness
IGA Light helps organizations meet regulatory standards such as:
- GDPR, SOX, NIS2 Guide, ISO 27001, and more.
- Provides automated reports and logs for audit trails.
8. Cost-effective & Scalable
- Lower Total Cost of Ownership (TCO) than full IGA solutions.
- Suitable for small to mid-sized organizations looking for governance without high implementation and maintenance costs.
- Scales with business needs while remaining lightweight and efficient.
Benefits of Implementing IGA Light
1. Improved Security Posture
- Helps prevent security breaches by ensuring only authorized users have access to critical systems.
- Reduces orphaned accounts, minimizing the risk of former employees retaining access to sensitive data.
- Enforces the least privilege access, preventing excessive permissions that could be exploited.
2. Faster Deployment & Time-to-Value
- Unlike traditional IGA solutions that take months to implement, IGA Light can be deployed in days or weeks.
- Organizations can quickly gain visibility into user access and start mitigating security risks immediately.
- Provides immediate return on investment (ROI) by enhancing governance with minimal setup.
3. Cost-Effective Solution
- Lower total cost of ownership (TCO) compared to full-featured IGA platforms.
- Reduces costs associated with manual access reviews, audits, and risk management.
- No need for large IT teams to manage the system—IGA Light is simpler and requires less maintenance.
On average, IAM solutions reduce IT administrative costs by 50%.
4. Ensures Compliance with Regulations
IGA Light helps organizations meet regulatory and industry standards such as:
- GDPR (General Data Protection Regulation)
- ISO 27001 (Information Security Management)
- NIS2 (Network and Information Security Directive)
- SOX (Sarbanes-Oxley Act) and HIPAA (Health Insurance Portability and Accountability Act)
5. Increased Visibility & Control Over User Access
- Provides a centralized view of user access across applications and systems.
- Makes it easy to track who has access to what, ensuring transparency.
- Reduces shadow IT risks by identifying unauthorized access points.
20% of all user accounts in enterprises are orphaned, leading to security risks. (Source: Gartner)
6. Simplified Access Reviews for Business Users
- Non-technical stakeholders can easily review and approve/revoke access rights.
- Reduces the burden on IT teams by making access reviews more intuitive and efficient.
- Ensures that users only retain access that is relevant to their current job roles.
7. Continuous Monitoring & Risk Detection
- Real-time monitoring ensures that access risks are identified and addressed promptly.
- Helps detect privilege creep (when users accumulate unnecessary access over time).
- Enhances Identity Threat Detection & Response (ITDR) by identifying anomalies in access behavior.
Insider threats cost organizations an average of $15.4 million annually.
8. Scalable for Future Growth
- Ideal for SMBs and mid-sized enterprises looking to establish identity governance without the high costs of enterprise IAM solutions.
- Can scale as organizations expand their workforce and IT infrastructure.
- Works seamlessly with cloud-based and hybrid environments.

Implementing IGA Light: A Step-by-Step Guide
Step 1: Assess Your Identity Governance Needs
Before implementing IGA Light, it’s essential to evaluate your organization’s identity governance requirements.
Key Considerations:
- What systems and applications need governance?
- Who will be the main users and administrators of IGA Light?
- What compliance regulations (e.g., GDPR, SOX, ISO 27001) does your organization need to meet?
- What are your security priorities (e.g., reducing orphaned accounts, enforcing least privilege, preventing insider threats)?
Step 2: Select the Right IGA Light Solution
Choosing the right IGA Light platform depends on factors like ease of integration, automation capabilities, and compliance support.
Key Factors to Consider:
- Integration: Can it connect with your existing Active Directory (AD), cloud applications, and databases?
- Automation: Does it support automated access reviews and alerts?
- Security Features: Does it help detect orphaned accounts, excessive permissions, and policy violations?
- Scalability: Can it grow as your organization expands?
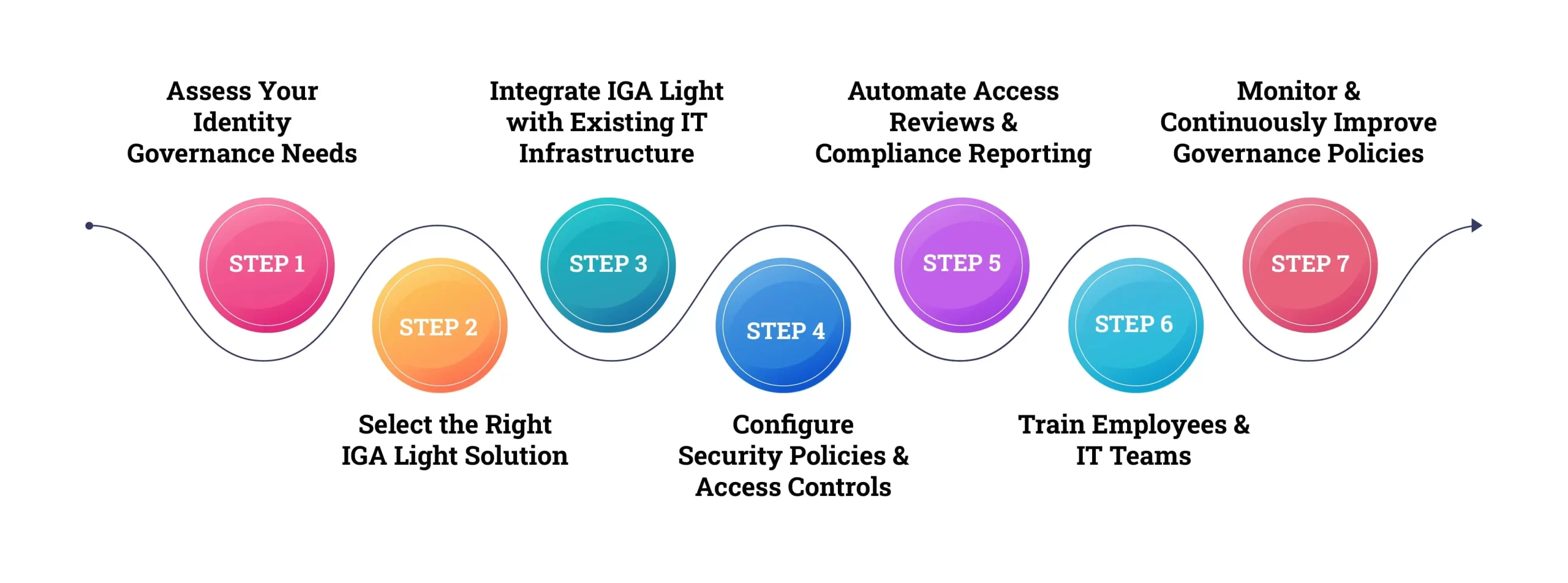
Step 3: Integrate IGA Light with Existing IT Infrastructure
Once you have selected your IGA Light solution, the next step is seamless integration with your IT ecosystem.
Integration Steps:
- Connect to your identity sources (e.g., Active Directory, cloud services, HR systems).
- Sync user identities from different platforms (Office 365, AWS, SAP, etc.).
- Define role-based access (RBAC) policies to establish user permissions.
- Enable automated access reviews to periodically validate access rights.
- Implement multi-factor authentication (MFA) if needed for additional security.
Step 4: Configure Security Policies & Access Controls
Defining clear security policies is crucial for minimizing risk and enforcing proper access controls.
Key Security Policies to Implement:
- Least Privilege Access: Ensure users only have access to resources required for their job roles.
- Separation of Duties (SoD): Prevent conflicts of interest (e.g., an employee shouldn’t request and approve their own access).
- Orphaned Account Cleanup: Regularly remove accounts belonging to former employees or inactive users.
- Privileged Access Management (PAM): Restrict and monitor administrative-level access.
Step 5: Automate Access Reviews & Compliance Reporting
IGA Light simplifies access reviews and compliance reporting by automating repetitive tasks.
Steps to Automate Access Reviews:
- Schedule periodic access certifications for critical systems.
- Enable alerts for unusual access patterns (e.g., an employee gaining excessive permissions).
- Generate compliance reports automatically to meet regulatory audits.
- Use AI-driven analytics (if available) to detect security risks in access permissions.
Step 6: Train Employees & IT Teams
Effective identity governance requires both user awareness and IT team training.
Training Plan:
- Educate employees on why access governance is important.
- Train IT staff on IGA Light’s dashboard, reports, and alerts.
- Conduct regular phishing and insider threat awareness training.
- Ensure department managers know how to approve or revoke user access.
82% of data breaches involve a human element, such as social engineering or credential misuse. (Source: Verizon 2023 DBIR)
Step 7: Monitor & Continuously Improve Governance Policies
After implementing IGA Light, continuous monitoring and optimization are necessary to adapt to changing security threats and compliance needs.
Key Monitoring Tasks:
- Analyze audit logs for unusual access patterns.
- Review access controls every 6 months to ensure least privilege principles are followed.
- Adjust policies based on compliance changes (e.g., GDPR updates, SOX requirements).
- Gather feedback from IT teams and business units to improve the system.
Challenges and Considerations in Implementing IGA Light
While IGA Light offers numerous benefits, organizations must consider a few challenges and limitations:
1. Limited Scope Compared to Full IGA Solutions
- Traditional IGA solutions provide a broader range of features, including advanced automation, full lifecycle management, and deep integrations with multiple systems.
- IGA Light focuses on essential identity governance features, which may not be sufficient for large enterprises with complex IAM needs.
2. Integration with Existing Systems
- Ensuring that the IGA Light solution integrates seamlessly with existing IT infrastructure and applications is crucial.
- Some solutions may require additional customization or manual configurations to work efficiently.
3. User Adoption and Training
- Business users and IT teams must be adequately trained to leverage IGA Light effectively.
- Without proper onboarding and awareness, organizations may face resistance to change.
4. Scalability
- While IGA Light is excellent for small and mid-sized enterprises, organizations planning for long-term growth must evaluate whether it can scale with their evolving needs.
Conclusion
IGA Light offers a practical and efficient alternative to traditional IGA solutions. Organizations can achieve strong identity governance without excessive costs and complexity by leveraging automation, data-driven insights, and rapid deployment.
The case study of the European insurance company highlights how a well-implemented IGA Light solution can provide immediate and tangible benefits, improving security, compliance, and operational efficiency. As identity governance becomes an increasingly critical component of cybersecurity, adopting IGA Light can help organizations take control of user access effectively and affordably.
For businesses looking to improve their identity governance strategy without overextending resources, IGA Light presents a compelling solution. Ready to take control of user access? Explore lightweight IGA solutions and transform your security approach today!
ABOUT AUTHOR

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.




