Blog
Maximize Cybersecurity with Existing Cloud Investments | Paramount

Maximize Your Cybersecurity Posture with Existing Cloud Investments
With the increasing adoption of cloud technology, cybersecurity has become a top priority for businesses worldwide. However, as companies seek robust security solutions, the challenge of managing cybersecurity budgets looms large, particularly in regions like the Middle East and Africa (MEA), where digital transformation is accelerating. Rather than investing in additional tools, many organizations can leverage the security features already embedded within their cloud infrastructure, optimizing both their cybersecurity posture and cost-effectiveness.
Strengthening Cybersecurity Without Breaking the Bank
Cybersecurity spending in MEA is expected to grow from $6.2 billion in 2024 to $8.4 billion by 2027. Despite this growth, budget constraints persist, and organizations face pressure to maximize security without inflating costs. Many businesses use multi-cloud or hybrid cloud setups that include tools and services offering built-in security features that, if properly utilized, can be instrumental in strengthening defenses without adding extra financial burdens.

The Growing Demand for Cost-Effective Cybersecurity Solutions
As organizations adopt hybrid and multi-cloud environments, they encounter new security challenges. Traditional cybersecurity in MEA region approaches often struggle to adapt to cloud complexities, and adding third-party security solutions can become financially burdensome. In response, businesses are focusing on making the most of existing security features within their cloud environments. Leveraging these built-in tools can alleviate some of the financial strain associated with cybersecurity investments while still safeguarding sensitive data, infrastructure, and applications.
For example, Microsoft’s cloud security framework offers a Zero Trust architecture that secures identities, endpoints, applications, and networks. With these types of native tools, businesses can maintain a robust security posture without incurring additional costs. As a result, optimizing in-built security features has emerged as a critical, cost-effective strategy in the MEA region and beyond.
Leveraging Built-In Cloud Security Tools for Maximum Efficiency
Leading cloud providers like Microsoft, Amazon Web Services (AWS), and Google Cloud include a range of built-in security tools designed to help organizations manage and secure their cloud assets. Yet, many companies still fail to utilize these offerings fully. By utilizing Microsoft’s E5 built-in security tools, businesses can save approximately $1.5 million annually in costs when compared to deploying separate third-party solutions, covering aspects such as Identity and Access Management, Data Loss Prevention, and Endpoint Protection.
Let’s explore some examples of how existing cloud tools can enhance security without significantly impacting the budget.
-
Identity and Access Management (IAM):
IAM solutions, such as Azure Active Directory and AWS Identity and Access Management, help control access to critical resources. They enable organizations to enforce strict access policies, multi-factor authentication, and user privilege management, all without the need for additional software.
-
Data Loss Prevention (DLP) and Encryption:
Most cloud providers include DLP tools that can prevent data leaks and enforce data compliance policies. Encryption tools for data at rest and in transit further protect sensitive information, offering an additional layer of security that’s often included in subscription plans.
-
Monitoring and Threat Detection:
Cloud-native monitoring solutions, like Microsoft Sentinel or AWS CloudWatch, are highly effective for detecting and responding to threats in real-time. These solutions often include advanced threat intelligence capabilities and can be integrated with Security Information and Event Management (SIEM) systems for comprehensive monitoring.
-
Zero Trust Cloud Security Architecture:
Zero Trust frameworks provided by cloud platforms like Microsoft ensure that every access request is verified before being granted, thereby reducing potential vulnerabilities. This layered approach includes identity verification, device health checks, and role-based access controls, fortifying security at each access point.
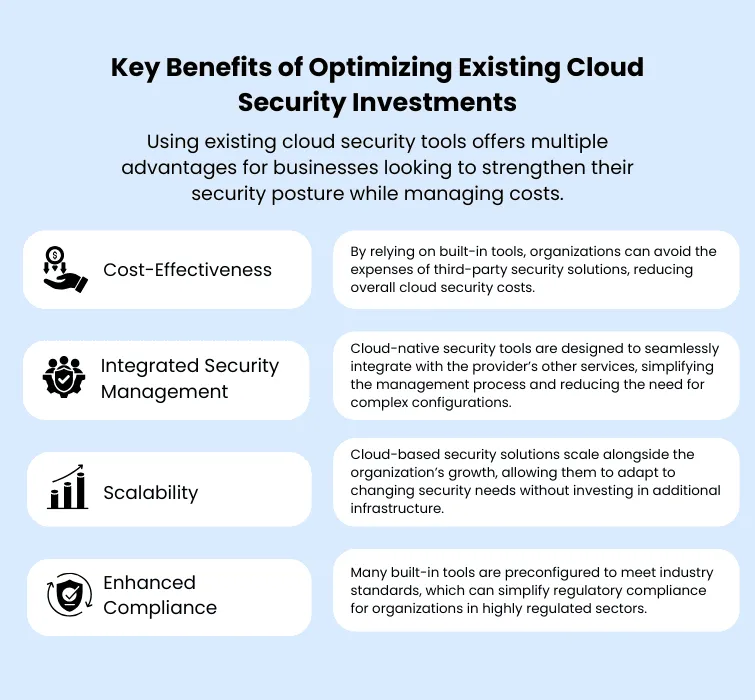
Practical Strategies to Enhance Security with Existing Cloud Investments
Optimizing cloud security isn’t just about cost-cutting; it’s also about leveraging the full potential of available tools to protect critical assets effectively. Here are several practical strategies that businesses can adopt:
-
Implement Identity and Access Management (IAM):
IAM frameworks not only improve security but also simplify user management. By setting up multi-factor authentication and role-based access controls, organizations can restrict access to authorized users, minimizing potential security breaches.
-
Automate Threat Detection and Response:
With tools like Microsoft Sentinel, companies can immediately implement automated threat detection to address potential security issues. This automation enhances response times, helping to prevent data breaches before they escalate.
-
Enforce Data Protection Policies:
Encryption and DLP policies, available within most cloud environments, prevent unauthorized access to sensitive data. With data encryption and regular security audits, companies can reduce their exposure to potential threats.
-
Adopt a Zero Trust Framework:
Zero Trust security works on the principle that no entity, whether inside or outside the organization, is automatically trusted. By deploying Zero Trust policies, companies can require verification for each user and device attempting to access resources.
-
Utilize Compliance and Audit Tools:
Most cloud providers offer compliance management tools to help businesses align with industry regulations. For example, Microsoft Compliance Manager allows companies to monitor compliance status and automatically generate audit reports, ensuring regulatory adherence without additional software costs.

The Webinar: Expert Guidance on Maximizing Cloud Security Investments
Paramount, a cybersecurity leader, recently hosted a webinar focused on maximizing cloud security investments. The session covered essential strategies for making full use of existing cloud security features, providing real-world examples of cost-effective cybersecurity.
The webinar highlighted how businesses can reduce capital expenditures (capex) by optimizing existing licenses and implementing a zero-trust architecture. For instance, using Microsoft’s Entra ID for privileged access management reduced security risks and improved application accessibility for one company. Paramount’s experts shared insights on how small changes—like enforcing multi-factor authentication or utilizing DLP tools—can make a big difference in securing cloud environments.
How Can Paramount Help?
Paramount offers an array of cybersecurity services designed to help businesses make the most of their cloud investments. With expertise in cloud security, IAM, and Zero Trust frameworks, Paramount helps organizations navigate complex security challenges while optimizing costs.
Paramount’s consultants specialize in cloud security assessments. They help businesses evaluate their current security postures and recommend adjustments to better leverage cloud-native tools. Whether it’s enabling secure access, ensuring compliance, or enhancing data protection, Paramount provides tailored strategies that align with business goals and budgetary constraints.

Case Studies
Case Study 1: Reducing Data Loss and CapEx by Leveraging Microsoft Purview
A Middle Eastern corporation struggling with data visibility and management leveraged Microsoft Purview’s DLP tools to structure its data handling processes. The company implemented a data classification framework that reduced data loss by 80% and eliminated capex costs by 90%, all by utilizing existing Microsoft licenses.
Case Study 2: Minimizing Attack Surfaces in a Large-Scale Mass Transit System
With millions of users, a large mass transit system faced challenges in managing access control. Paramount worked with the client to implement a security posture assessment and a Zero Trust framework using Microsoft Entra ID and Intune. The new system reduced the attack surface by 90%, allowing the client to meet security goals while minimizing budget impact.
Recent Posts

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
