Blog
Threat Intelligence Platform

How to Build a Threat Intelligence Platform That Works for You
Advanced Persistent Threats (APTs) involve stealthy, persistent adversaries who don’t seek quick attacks. Instead, they linger in the background, learning your network’s every move, waiting for the right moment to strike. Traditional defenses may not be sufficient to fend off these threats.
In regions like the Middle East, where countries such as Saudi Arabia and the UAE rank among the top cyberattack targets, the question is not “if” but “when” your organization will be attacked. APT groups, like Tropic Trooper, continuously expand their attack scopes, targeting sensitive government and private sector data. The financial and reputational losses from these breaches often exceed millions of dollars.
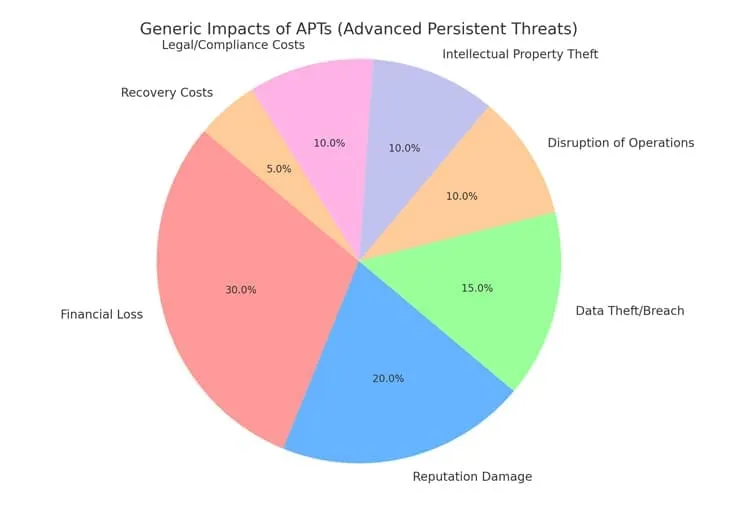
The Impact of Advanced Persistent Threats (APTs) on Your Organization
1. Financial Loss
APT attacks often cause financial harm through:
- Direct theft of money or assets.
- Regulatory fines for data breaches, especially in sectors like finance or healthcare.
- Recovery costs from forensic investigations and remediation efforts.
- Business disruption from downtime, leading to lost revenue.
2. Fact
The average data breach costs over $3.8 million.
3. Data Theft
APTs often target:
- Intellectual property like product designs and trade secrets.
- Customer information, including personal and financial data.
- Business plans and strategic information, potentially affecting market position.
4. Operational Disruption
APTs target critical systems to disrupt:
- Industrial control systems in energy, manufacturing, or transportation.
- Healthcare systems, endangering lives through service interruptions.
- Supply chains, leading to logistical slowdowns and unfulfilled orders.
5. Reputational Damage
A significant attack can result in:
- Customer churn: Loss of customers who doubt your data security.
- Broken partnerships: Business partners may terminate contracts due to risk concerns.
6. Regulatory Penalties
- Fines from GDPR or HIPAA violations.
- Increased compliance scrutiny through audits and investigations.
7. Long-Term Espionage
APTs maintain access for prolonged periods to:
- Gather intelligence on networks and vulnerabilities.
- Plan future attacks for maximum impact.
- Discover hidden weaknesses for later exploitation.
Building an Effective Threat Intelligence Platform (TIP)
1. Data Collection & Aggregation
Collect data from:
- Internal sources: Firewalls, intrusion detection systems (IDS), and endpoint detection tools.
- External sources: Open-source intelligence (OSINT), industry alerts, and government advisories.

2. Correlating Threat Data with Context
Your TIP must map threat data to the organization’s risk profile to filter out noise and focus on relevant threats.
3. Automating Threat Response
Automate responses to reduce attacker dwell time:
- Isolate compromised systems to prevent lateral movement.
- Trigger alerts to notify the Security Operations Center (SOC).
- Block malicious IPs and quarantine suspicious files automatically.
Steps to Build a Threat Intelligence Process
1. Define Your Organization’s Needs
Identify key assets, likely adversaries, and industry-specific risks to develop a customized TIP.
2. Select the Right Tools
Ensure tools integrate with SIEM, endpoint detection, and incident response platforms.

3. Automate & Configure Responses
Pre-define actions for specific threat levels to ensure rapid, consistent responses.
4. Continuous Monitoring & Threat Hunting
Use SIEM and endpoint tools to maintain real-time visibility across your IT environment.
5. Integrate TIP with Security Infrastructure
Ensure seamless integration with SOC processes and security tools to streamline workflows.
6. Train Your Team
Invest in scenario-based training for SOC teams to ensure readiness against advanced threats.
Continuous Improvement through Feedback Loops
1. Post-Incident Reviews:
Analyze security incidents to refine TIP settings and response playbooks.
2. Stay Informed:
Keep up with peer incidents and evolving threats in your industry.
3. Evolve with Threat Actor Tactics:
Regularly update detection rules to keep pace with new vulnerabilities.

Why You Need a Threat Intelligence Platform (TIP)
-
Stay Ahead of Threats:
Real-time insights help preempt cyberattacks.
-
Reduce Human Error:
Automation minimizes manual processes and enhances response times.
-
Accelerate Incident Response:
Correlating threat data with contextual insights ensures faster mitigation.
The Time to Act is Now
With 58% of organizations in the Middle East expecting APT attacks in the coming year, the threat landscape is evolving rapidly. Contact a cybersecurity provider to integrate a TIP with cutting-edge technologies, real-time monitoring, and automation.
Recent Posts
- Preparing for Data Privacy Compliance: A Guidee
- 8 IAM Challenges Every Organization Faces and How to Tackle Them Using Identity Data Analytics
- Preparing for AI in Cybersecurity: A Strategic Guide for Businesses
- Why AI Language Models Matter to Your Business
- How to Detect and Prevent Deepfake Attacks in Cybersecurity

Protect your online assets from cyber threats with Paramount

Comprehensive cyber security solutions for individuals and businesses

Significantly reduce the risk of cyber threats and ensure a safer digital environment.
