Streamline Identity Management with End-to-End Lifecycle Solutions
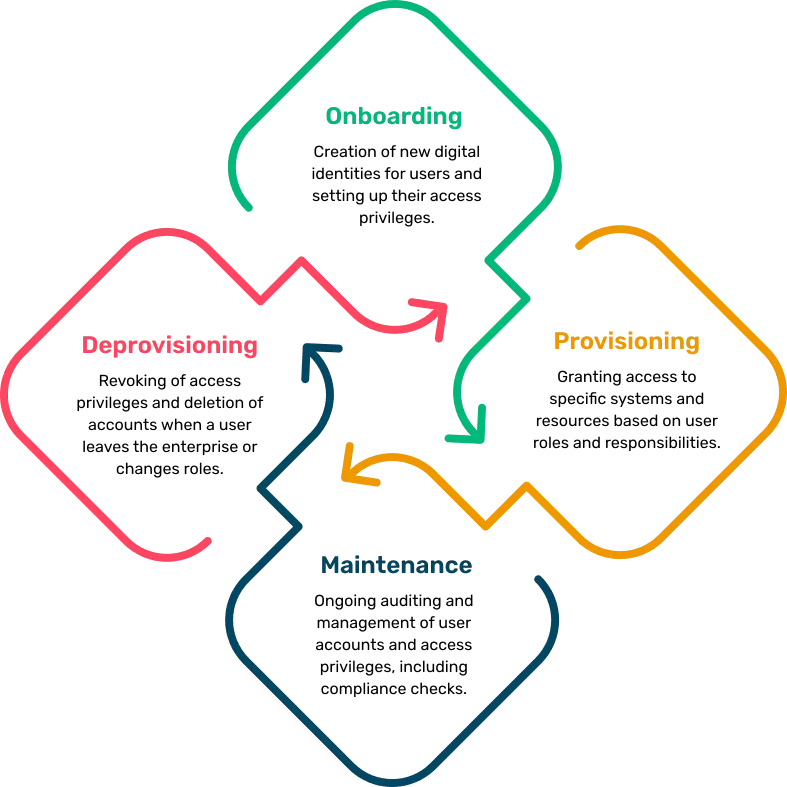
Control user access, tighten security, and minimize risks at every stage of the identity journey. Our ILM solutions give you complete control over who gets access, when, and how.
Contact Our Experts