AI Roadmap Development
Get a clear, step-by-step roadmap tailored to your organization’s priorities, ensuring maximum ROI.
7 in 10 CEOs hesitate to implement AI into their enterprise’s security posture—simply due to uncertainties about the technology’s strategic fit and return potential.
Coming from conflicting vendor claims or lack of knowledge, these uncertainties often cause delays in adoption that compromise your organization’s integrity.

Maximize security, minimize complexity. At Paramount, we help you cut through all such uncertainties and guide you through the AI adoption journey for optimal cybersecurity outcomes.
Get a clear, step-by-step roadmap tailored to your organization’s priorities, ensuring maximum ROI.

Make intelligent decisions. We help you filter out genuine AI innovations from market buzz for smarter adoption.

Focus only on what works for you. Map out and adopt AI use cases relevant for your organizational needs.

We’ll design and help execute an end-to-end AI adoption strategy, tailored for your cybersecurity landscape.
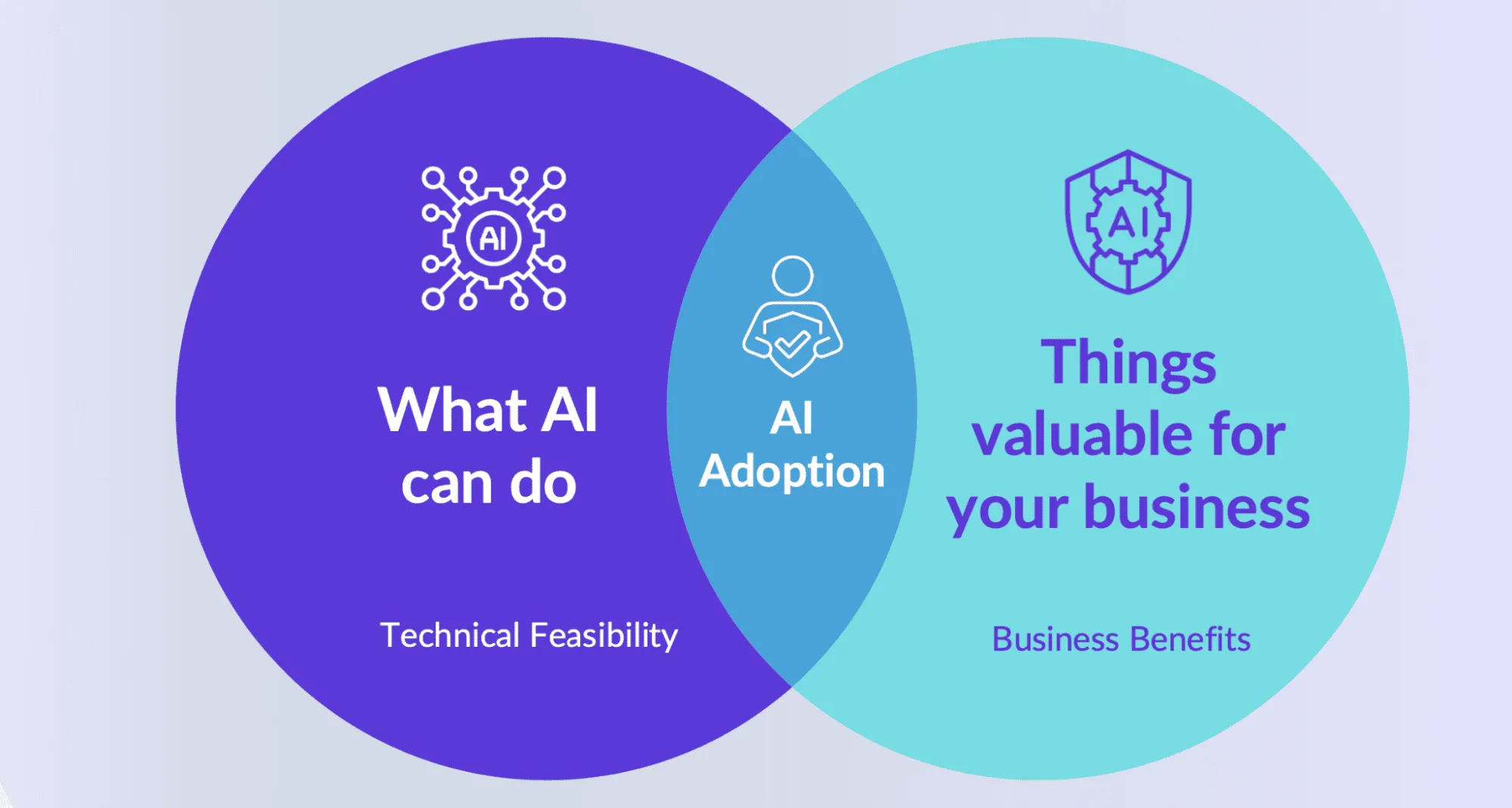
AI works best in areas where it delivers critical business benefits, while also having high technical feasibility. Using this, we’ve compiled an evaluation matrix that clearly highlights AI’s adaptability to different security requirements.
Criticality
Transaction Cost Advantage
Repeatability and Data Availability
Ease of Standardization
Transaction Frequency
Time Sensitivity
Criticality
Transaction Cost Advantage
Repeatability and Data Availability
Ease of Standardization
Transaction Frequency
Time Sensitivity
Criticality
Transaction Cost Advantage
Repeatability and Data Availability
Ease of Standardization
Transaction Frequency
Time Sensitivity
As part of Cybersecurity Awareness Month, take our quick assessment to discover how well-equipped your organization is to face evolving threats. This interactive quiz will identify your strengths and vulnerabilities, providing tailored insights and actionable steps to enhance your security posture. Don’t wait for a breach—embrace proactive measures today to ensure a safer future for your organization and contribute to securing our world!Whether it’s for self-healing networks or predictive threat intelligence, we help you integrate different AI tools and technologies into your organization with a pragmatic transformative strategy. From integrating MLSecOps to adopting industry standards like ISO 42001:2023, we cover all your requirements along the way.

Detect vulnerabilities, analyze scripts, and enhance incident investigation with Security Copilot’s advanced AI functionalities—while keeping your enterprise data 100% secure.